- Jamf Nation Community
- Products
- Jamf Pro
- Force Xprotect to update?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-11-2020 07:54 AM
Hi,
How do you force an Xprotect version update?
Trying:
softwareupdate --background-criticaloutputted the following:
softwareupdate[92845]: Triggering background check with forced scan (critical and config-data updates only) ...
But running:
defaults read /Library/Apple/System/Library/CoreServices/XProtect.bundle/Contents/Info.plist CFBundleShortVersionStringshows an older version of XProtect
For our labs we updated to 10.15.7 using the Combo and Supplemental PKGs but the Xprotect version remained an old version.
We like to control the software update process so we have everything unchecked in Software Update
Not sure if that has something to do with Xprotect being unable to update even when running softwareupdate --background-critical from the Terminal.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2020 02:53 PM
@mvu thanks for the feedback it pushed me towards an answer. In the end the final piece was
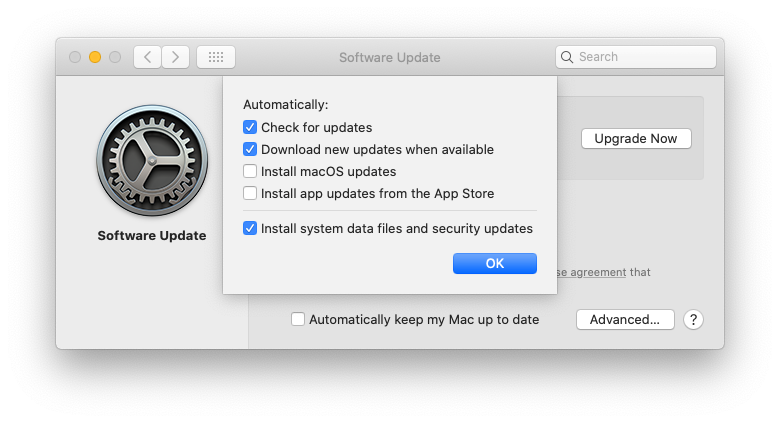
softwareupdate --background --include-configin combination with the following Software Update PreferencePane configuration
This Software Update PreferencePane configuration is displayed after running the following (assuming nothing was selected before):
/usr/bin/defaults write /Library/Preferences/com.apple.SoftwareUpdate.plist AutomaticCheckEnabled -bool true
/usr/bin/defaults write /Library/Preferences/com.apple.SoftwareUpdate.plist AutomaticDownload -bool true
/usr/bin/defaults write /Library/Preferences/com.apple.SoftwareUpdate.plist ConfigDataInstall -bool trueBasically if I tried to run
softwareupdate --background --include-config
without the above configuration for Software Update then the XProtect definitions would simply not update. Once I at least re-enabled the Mac's ability to check and download updates then running softwareupdate --background --include-config would finally grab the latest Xprotect data.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-11-2020 09:52 AM
Does this work?
a) softwareupdate --background --include-config
b) softwareupdate --background --include-config-data
If you want to install ALL Mac updates, including Xprotect and MRT:
c) softwareupdate --ia --include-config-data
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2020 02:53 PM
@mvu thanks for the feedback it pushed me towards an answer. In the end the final piece was
softwareupdate --background --include-configin combination with the following Software Update PreferencePane configuration
This Software Update PreferencePane configuration is displayed after running the following (assuming nothing was selected before):
/usr/bin/defaults write /Library/Preferences/com.apple.SoftwareUpdate.plist AutomaticCheckEnabled -bool true
/usr/bin/defaults write /Library/Preferences/com.apple.SoftwareUpdate.plist AutomaticDownload -bool true
/usr/bin/defaults write /Library/Preferences/com.apple.SoftwareUpdate.plist ConfigDataInstall -bool trueBasically if I tried to run
softwareupdate --background --include-config
without the above configuration for Software Update then the XProtect definitions would simply not update. Once I at least re-enabled the Mac's ability to check and download updates then running softwareupdate --background --include-config would finally grab the latest Xprotect data.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-18-2020 01:03 PM
If you wanted to keep those unchecked for control, you can download the Xprotect and MRT packages directly and upload to Jamf to push. There are a few ways to get the packages if you want to go that route.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-31-2020 12:07 AM
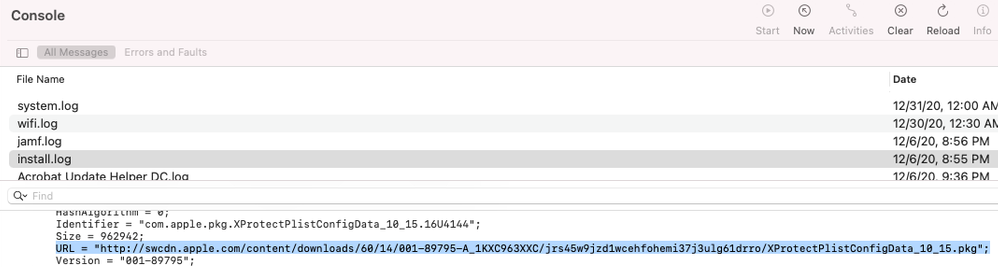
@mvu ah, you're right I could have just downloaded the pkgs for that. I think in the past I've installed things on a build machine and then looked at the install.log to figure out the URL path for the installed pkgs.
Or is there a better way of extracting/parsing for the pkgs in Apple's software repository?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-13-2021 08:28 AM
Yes, you can find the URL in the Console. You can also use Terminal and the softwareupdate -d command. I explain how I did this with Safari that in the link below. Someone mentioned the app SUS Inspector as well, which saves some work on digging for the URL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-12-2023 05:01 AM
@fgonzale I'm struggling to get this to work and all of our macOS devices are on the latest version of macOS (14.1.2..... I realize 14.2 was released yesterday...) but a handful of devices have an old version of XProtect for some reason. Do you happen to have a script that works to update XProtect? I tried running softwareupdae - d but no luck, but I think that's just because it's downloading the update, but not actually installing the update and I'm not to sure how to kick off the install.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-08-2024 11:31 AM
Create a new configuration profile with a Software Update payload that enforces automatic installation of configuration data and system data files.
Alternatively, package and deploy Eclectic Light's silnite utility, create a smart group based on XProtect Definitions Version (Computer Inventory > Security, currently version 2177), then create a policy scoped to that group to execute command "silnite au" (by default it installs to /usr/local/bin/) to check for and install updates.