- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-29-2015 09:22 PM
In a recent deployment of the SecureConnector, we are discovering a large number of systems generating errors after the SecureConnector deployment. It is suspected the process is being spawned twice. Our install policy is very generic without any custom configurations. Has anyone experienced similar behavior or found a resolution?
6/29/15 9:16:46.339 PM sshd[22462]: error: Bind to port 2201 on 127.0.0.1 failed: Address already in use.
6/29/15 9:16:46.340 PM sshd[22462]: fatal: Cannot bind any address.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-19-2017 09:34 AM
Hey guys, I created a bash file. Just put it in your scripts and deploy... It works perfectly.
[START CODE]
!/bin/sh
Downloading OSX Update Package to /tmp on the host
curl -o /tmp/update.tgz http://IPADDRESS/SC_packages/update.tgz; sleep 3
Extracting update.tgz to /tmp
tar -zxvf /tmp/update.tgz -C /tmp; sleep 3
Installing SecureConnector as a Daemon/Dissolvable w/ visible/invisible menu bar icon
echo '[Enter Password]' | sudo -S /tmp/Update/Update.sh -t daemon -v 1; sleep 3
Checking/Starting processes in case they did not start on install
daemon_pid=ps auxww | grep -v grep | egrep "ForeScout SecureConnector.-daemon" | awk '{print $2}'
agent_pid=ps auxww | grep -v grep | egrep "ForeScout SecureConnector.-agent" | awk '{print $2}'
daemon_plist=/Library/LaunchDaemons/com.forescout.secureconnector.daemon.plist
agent_plist=/Library/LaunchAgents/com.forescout.secureconnector.agent.plist
if [[ -z "$daemon_pid" && -z "$agent_pid" ]]; then #Starting Daemon process launchctl unload $daemon_plist launchctl load $daemon_plist
#Starting GUI process
launchctl unload $agent_plist
launchctl load $agent_plist
elif [[ ! -z "$daemon_pid" && -z "$agent_pid" ]]; then
#Starting GUI process
launchctl unload $agent_plist
launchctl load $agent_plist
fi
Clean-up a little
rm -rf /tmp/update.tgz /tmp/Update/
[END CODE]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-17-2015 05:15 PM
We are also using ForeScout SecureConnector. Recently it seems they created an actual Mac agent, not a cobbled folder with ssh keys. It seems to be working, but I suspect we have Macs that have SC installed but are not reporting in successfully to the Forescout console. Continuing to investigate....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-30-2015 08:25 AM
Can I ask how you are pushing SC out?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-30-2015 08:39 AM
@johnklimeck Last time I looked at SC, it was a bash script, not a real agent. It's in /var/ somewhere.
@Gonzalez I suspect you are right and it is being installed twice. The agent opens a root accessible sshd port, allowing the SC server to SSH into the workstation. To me, that is a big security hole. But binding to the same port twice suggests it is starting twice. Look in your LaunchDaemons/LaunchAgents; I don't remember how it started anymore. When I played with SC, I needed to download an installer from the server on each machine and couldn't deploy a package to all machines via the JSS. That change was also planned for the release about the end of the year.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-23-2015 11:05 AM
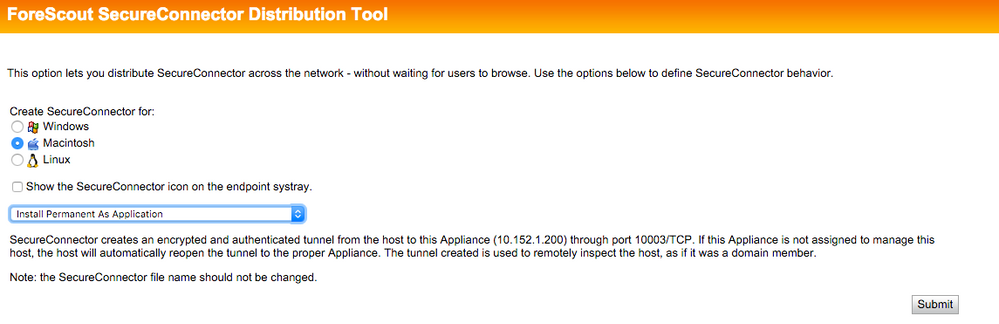
We're running Forescout - haven't had problems pushing the package out. I just tossed the .mpkg downloaded from the server into Casper Admin and created a policy to push it once per computer at check in.
Just make sure you are using the following options when downloading it from your Enterprise Manager server (important items are the "show the...icon" and "Install Permanent..."):
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-23-2016 08:51 AM
@jreinstedler What version of OS X are you running? (Edit: we're on 10.10.5) We installed the SecureConnector downloaded from the appliance and show it running when doing
ps auxww | egrep 'forescout|secureconnector' -ibut the ForeScout console is only showing the info that was available before installation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-14-2016 10:32 PM
Forescout just released a massive update to their Mac agent. This is now a proper agent with less of the funny business that the previous agent used. This is not a simple update however... the usual FS plugin for Macintosh is updated and a new OS X plugin is required. Once the plugins are installed, you'll also need to push an upgrade to all your existing agents from within the EM. Any machines without the agent can be installed using a shell script - however the system must NOT have FS installed. Check your Forescout portal for more info... I just went through the update myself.
One note - they added an app to the /Applications folder which makes FS removal too easy - I would suggest at a minimum hiding the application...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-15-2016 08:23 AM
@jreinstedler,
Great to hear, questions, if I may:
I imagine one gets this new installer PKG from our Forsecout admins (from the FS appliance)
Can I just push this new PKG out with the JSS, and it will overwrite the existing, or, do I have to un-install first, before the new install
Agreed, chflags hidden on the FS app in /Applications, is a good idea
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-15-2016 05:48 PM
@johnklimeck The installer is provided as a DMG which contains a .app for the install. You can get it from your FS admins or you can grab it yourself if you know the IP address of one of your FS appliances or the FS Enterprise Manager. Typing https://{IP ADDRESSorHOSTNAME}/sc.jsp will get you to the page seen previously in this thread. From there you can download the standalone install package.
You cannot use any of the packages to update the existing FS managed endpoints. The FS admins will need to run a policy on FS to update the clients - they will need to review the FS docs for this.
All new clients can have FS installed one of two ways: slipped into your image or pushed via Casper. If you push via casper, you'll need a separate package that the FS admins will need to provide (it's in tgz form, which extracts to several sh files). This 2nd option will NOT work for existing machines - the install will fail and will leave the host in an unmanageable state, so you must make sure that only new machines receive this new package. I have not yet tested the package install on new endpoints yet. I am planning to do so soon, for now, the machines are getting upgraded via FS.
One major issue I see with this new version is that it's extremely easy to remove and if you use the "visible" version with the app icon, users can "Quit" the app which breaks communication with FS. This only lasts until the machine is restarted though. Hopefully FS can do something better in terms of protecting the agent and preventing it from being stopped. The previous version was very good at this... this new one... not so much.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-19-2016 10:51 AM
sorry to bump, but in a similar position.
how are you guys deploying it without needed to reboot/authenticate to open the app?
those are the only ways i am able to get it run, which, unlike trend or webex, launches and goes straight to menu bar.
thoughts?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-19-2017 09:34 AM
Hey guys, I created a bash file. Just put it in your scripts and deploy... It works perfectly.
[START CODE]
!/bin/sh
Downloading OSX Update Package to /tmp on the host
curl -o /tmp/update.tgz http://IPADDRESS/SC_packages/update.tgz; sleep 3
Extracting update.tgz to /tmp
tar -zxvf /tmp/update.tgz -C /tmp; sleep 3
Installing SecureConnector as a Daemon/Dissolvable w/ visible/invisible menu bar icon
echo '[Enter Password]' | sudo -S /tmp/Update/Update.sh -t daemon -v 1; sleep 3
Checking/Starting processes in case they did not start on install
daemon_pid=ps auxww | grep -v grep | egrep "ForeScout SecureConnector.-daemon" | awk '{print $2}'
agent_pid=ps auxww | grep -v grep | egrep "ForeScout SecureConnector.-agent" | awk '{print $2}'
daemon_plist=/Library/LaunchDaemons/com.forescout.secureconnector.daemon.plist
agent_plist=/Library/LaunchAgents/com.forescout.secureconnector.agent.plist
if [[ -z "$daemon_pid" && -z "$agent_pid" ]]; then #Starting Daemon process launchctl unload $daemon_plist launchctl load $daemon_plist
#Starting GUI process
launchctl unload $agent_plist
launchctl load $agent_plist
elif [[ ! -z "$daemon_pid" && -z "$agent_pid" ]]; then
#Starting GUI process
launchctl unload $agent_plist
launchctl load $agent_plist
fi
Clean-up a little
rm -rf /tmp/update.tgz /tmp/Update/
[END CODE]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2024 07:21 AM - edited 10-18-2024 07:24 AM
Old post, but Im a new Forescout SecureConnector customer and wanted to share that the example above is still relevant and works in 2024 as of SC version 29.0.
My script is similar but not identical. In my testing I haven't had to start any agents or daemons.
The main step here is to curl the SC installer archive from your org's appliance directly to ensure you get your org-specific config plist file (/Library/Preferences/com.forsecout.secureconnector.plist). I tried manually downloading a .dmg from our appliance web UI and building my own pkg installer from those resources, but it was rather messy. Here's my basic process
1 Using my custom Jamf script and curl, download the OEM installer tgz from the Forescout server: https://YOUR_SERVER/SC_packages/update.tgz
2 I place the install.tgz file in /private/tmp via the script
3 My script then extracts the tgz archive and a directory named “Update” (capital U) is created in the /private/tmp directory. This contains the critical installer parts (including the org com.forescout.secureconnector.plist)
4 My script calls the OEM FS script from /private/tmp/Update/Update.sh and completes the installation. I let it to the heavy lifting since it's 'blessed' by FS and they know what to do with their components.
5 Script can optionally cleanup the /private/temp/... resources too (or they will get deleted reboot per macOS)