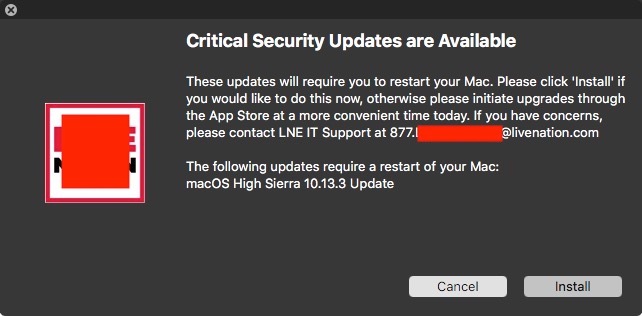
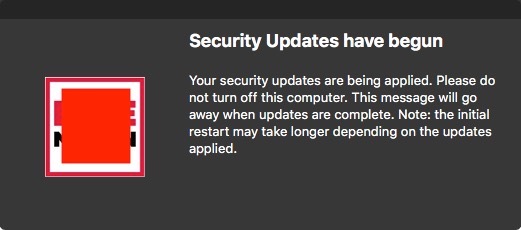
Just wanted to get a general consensus as to what method people prefer when running software updates on their clients.
Options I've seen so far are:
- Download the packages from Apple and push them out like any other policy.
- Enable the "Software Update" payload in a policy and install that way
- Run the softwareupdate -i -a command via script or as part of the "files and processes" payload in a policy.
Your preference???