How to configure the clustering from on Prem to Jamf DMZ JSS?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-19-2022 07:34 AM
Trying to configure the clustering from on-prem server to Jamf DMZ external server windows based env
where do I configure the firewall rules on-prem or on the Jamf DMZ instances?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-19-2022 08:23 AM
@NisarFawad Your firewall settings aren't done in Jamf Pro, those will have to be done by the network team that manages your firewall. As for configuring the Jamf Pro instance in the DMZ, https://docs.jamf.com/technical-articles/Installing_a_Jamf_Pro_Web_Application_in_the_DMZ.html is a good source of info.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-20-2022 05:56 AM
@sdagley do I need the web application to configure or the Memcached in the DMZ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-20-2022 07:02 AM - edited 01-20-2022 07:03 AM
(Replied to wrong part of thread)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-20-2022 06:37 AM - edited 01-20-2022 07:03 AM
@NisarFawad If you're planning on using memcached servers (I think they're still optional, or at least they were before my environment was moved from on-prem servers) then I'd expect you'd want them inside your firewall. The only Jamf Pro related servers required in your DMZ are the JSS instance (or instances if you're running a load balancer in front of them), and your public Distribution Point server.
Speaking of DPs... If you're using SMB connections to your internal DPs from Mac endpoints then you'll definitely want to move to HTTPS as publicly exposing SMB ports on a DMZ server is not a good idea.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-20-2022 06:46 AM
Thanks, @sdagley. I'm trying to configure the current on-prem server to talk with my external server SQL DB (in the DMZ), which is the clients get the patches and 3rd party software updates without connecting to VPN.
Primarily should be the DMZ server, and secondary will be the internal JSS server.
I hope that makes sense to you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-20-2022 07:05 AM
@NisarFawad That's backwards. Primary JSS node, MySQL server, and Primary DP should be on internal network. Only the Client JSS node and public DP should be in your DMZ.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-30-2022 08:39 AM
@sdagley, Trying to locate this line on the external DMZ web application when I add the internal keystore cert in the external instance the DMZ won't work.
should I remove the DMZ current cert or where can change that on the server.xml file?
https://docs.jamf.com/technical-articles/Installing_a_Jamf_Pro_Web_Application_in_the_DMZ.html
- Copy the certificate keystore file from the internal server to the external server.
- Modify the server.xml file on the external server to point at the keystore file by locating the Connector Port element and adding the following lines:
keystoreFile="/path/to/keystore-file" keystorePass="changeit"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2022 06:57 PM - edited 01-30-2022 06:57 PM
@NisarFawadYou need the .keystore file from your Primary (Internal) JSS copied to the DMZ JSS so that it's using the same certificate and the instructions you reference should be clear on that. If you're asking exactly where the keystore can be found, it varies by the OS you're running. For RHEL, it used to be in /usr/local/jss/tomcat/ but I don't know if that has changed (it's been a while since I've used an on-prem JSS install)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-31-2022 06:35 AM
@sdagley found the Keystore cert under the C:\Program Files\JSS\Tomcat\certs\.keystore.
My question is regarding the server.xml file that needs to be tweaked too. I'm not sure where and which part I should change the instruction said the following. I can't find the line or step 3, the Connector Port element on the external server.xml file.
- Copy or make a note of the Keystore password from the server.xml file on the internal server. It should look similar to the following:
keystorePass="changeit"
- Copy the certificate Keystore file from the internal server to the external server.
- Modify the server.xml file on the external server to point at the Keystore file by locating the Connector Port element and adding the following lines:
keystoreFile="/path/to/keystore-file" keystorePass="changeit"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-31-2022 06:44 AM
@NisarFawad Somewhere in the server.xml file for your DMZ JSS (which should be located at C:\Program Files\JSS\Tomcat\conf\server.xml on Windows) you're going to find variables named keystoreFile and keystorePass (search for just the variables, not the whole line in Jamf's example). Change those to the path to the keystore file you copied to the DMZ JSS from the Internal JSS, and the password for it that you extracted from the server.xml file from your Internal JSS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
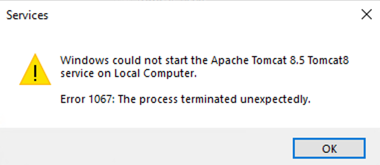
Posted on 01-31-2022 08:13 AM
I made the changes to the server.xml file and followed the steps by step, but now the apache tomcat is broken. The service is not starting back. I tried to start the service, getting an error because of looking at the cert on the server.xml file.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2022 08:39 AM - edited 01-31-2022 08:40 AM
Have you verified the access permissions on the copied keystore file are correct? Or looked at the tomcat log file to see what error(s) it shows?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-09-2022 03:50 PM
Hi @sdagley so I am able to access the internal database on the external instance DMZ, but my DMZ DNS name is different from the internal instance and I don't want to make the internal instance to the internet. when I do nslookup of my DMZ instance I can see it. not sure why not working? is that possible to use my DMZ Jamf instance different DNS name?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-09-2022 06:22 PM
@NisarFawad No. The DMZ JSS must have the same public DNS name as your internal DNS name, because that's the URL the Jamf Pro agent on your Macs is configured to connect to, and it's the certificate name that the JSS will present. Each JSS will have a different IP address despite having the same DNS name, that's what's known as Split DNS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-27-2022 08:27 PM
@sdagley, I'd pass out to do the clustering or internal Jamf instance connect our DMZ.
Is it possible to have one Jamf pro server with the DMZ configured with limited access? Suppose I'm trying to access the jamf pro URL outside the network route URL that is unreachable or not accessible. Only access it while connected VPN?