Howdy,
Been on a long road trying to get Big Sur and Crowdstrike to play nice together. Almost there.
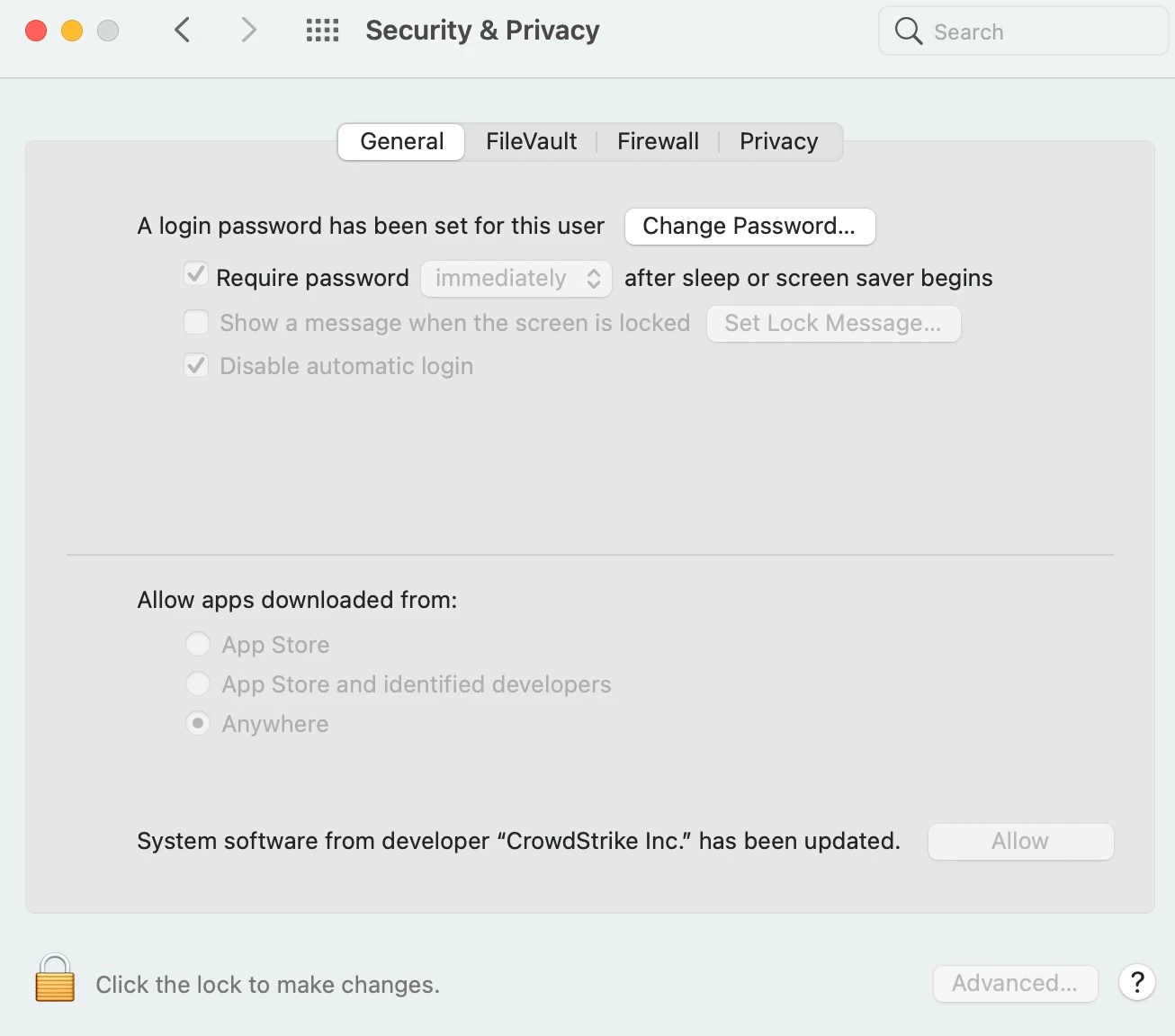
We've pushed a signed config profile to all our Catalina machines (BS is still restricted) and our Falcon sensors are up to date. The issue just seems that there is no way around the user having to allow "Crowdstrike, Inc" in Privacy settings.
I'm happy to let users know they should do this. My question is how do we double check without having to take their word for it. Per Crowdstrike we can't check it on their side so I'm hoping there's some jamf magic.
Curious if any Jamf/Crowdstrike folks been dealing with this?
Cheers