- Jamf Nation Community
- Products
- Jamf Pro
- Re: How to set Google Chrome Policy via Casper
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-22-2017 03:25 PM
Dear Forum Members,
Since the update of Google Chrome to 57, we have issue of "Your connection is not private" error and basically Chrome doesn't work with anything now. We are waiting on a proxy upgrade and in the mean time, also told to do a workaround on all clients for Google Chrome. Basically we need to set the Chrome Policy "EnableSha1ForLocalAnchors" to true. We did for all Windows clients via Group Policy. But I have no idea what to do with the Mac Clients. Anyone can shed some lights on how to approach this on a Mac?
Thanks all!
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2017 08:58 PM
Thank you @nsantoro for your generous code. I copied them into TextEdit and saved it as extension .mobileconfig. When I try to upload it from Configuration Profile in JSS, it didn't allow me. However, I got it working by creating com.google.chrome.plist file with the following code:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>EnableSha1ForLocalAnchors</key>
<true/>
</dict>
</plist>
I then uploaded to Configuration Profile section in the JSS by creating a new one and upload the plist file in the Custom Settings. Distribute to the iMac and it worked.
Thank you everyone!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-22-2017 03:27 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-22-2017 06:16 PM
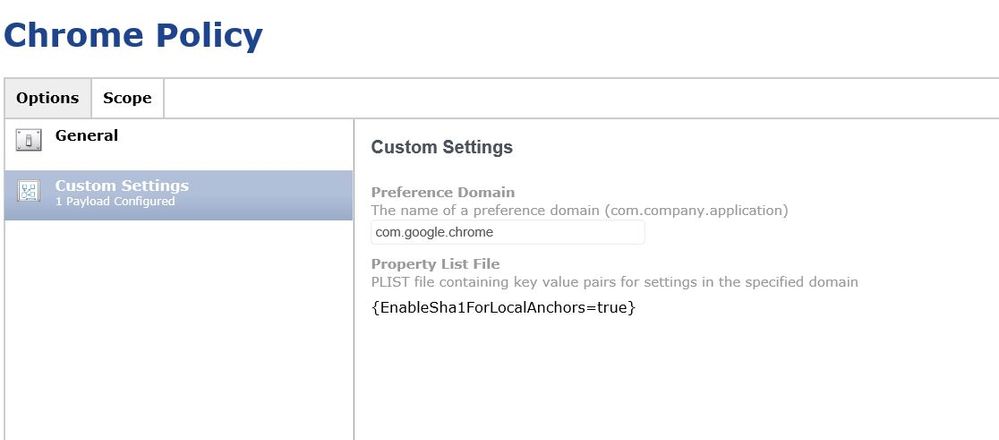
Maybe push out a Configuration Profile with Custom Settings.
Create a plist with the correct setting.
Here's a link to a site that I've used for doing things like setting Chrome to use the system print dialog and block extensions. https://www.chromium.org/administrators/policy-list-3
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-18-2017 11:30 AM
Hi Wangl2.
Take this code, and save it as a mobileconfig file. (Example GooglePolicy.mobileconfig)
Then upload it in Jamf / Configuration Profile.
On the client/test mac type in:
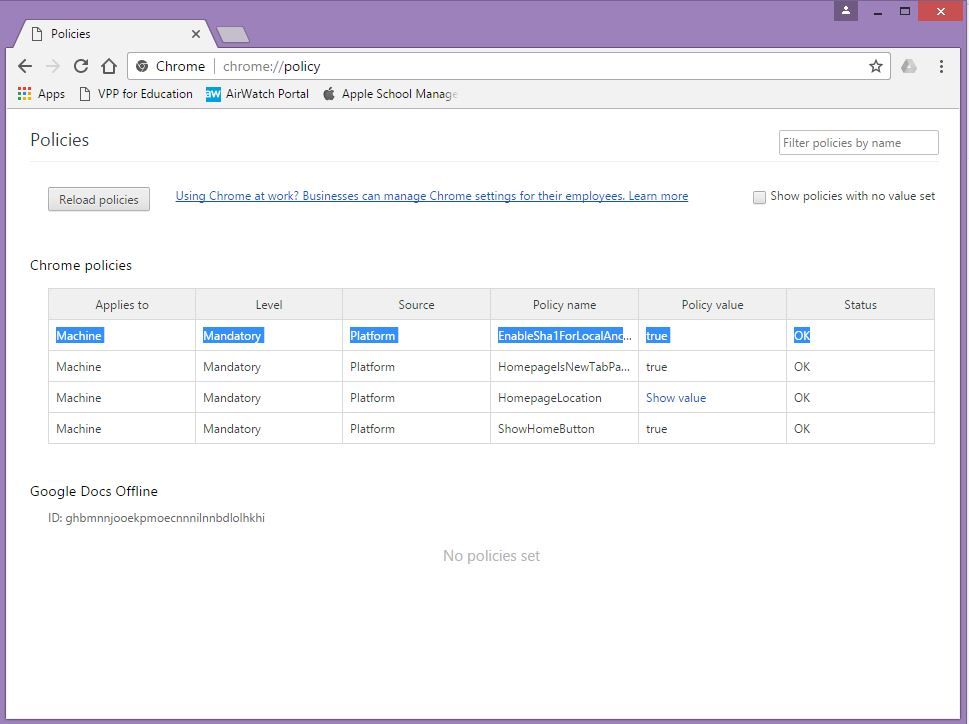
chrome://policy
EnableSha1ForLocalAnchors - will be seen as a managed policy, and allow you to get to sha1 sites.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadIdentifier</key>
<string>com.schoolname.profile.chrome</string>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>2015-04-20-6-20</string>
<key>PayloadOrganization</key>
<string>school name here</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadDisplayName</key>
<string>Google Chrome Policy</string>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadType</key>
<string>com.apple.ManagedClient.preferences</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadIdentifier</key>
<string>com.normandale</string>
<key>PayloadUUID</key>
<string>121-qasd</string>
<key>PayloadEnabled</key>
<true/>
<key>PayloadDisplayName</key>
<string>Custom: (com.google.Chrome)</string>
<key>PayloadContent</key>
<dict>
<key>com.google.Chrome</key>
<dict>
<key>Forced</key>
<array>
<dict>
<key>mcx_preference_settings</key>
<dict>
<key>ShowHomeButton</key>
<true/>
<key>DeviceAutoUpdateDisabled</key>
<true/>
<key>EnableSha1ForLocalAnchors</key>
<true/>
</dict>
</dict>
</array>
</dict>
</dict>
</dict>
</array>
</dict>
</plist>- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-21-2017 12:03 PM
@nsantoro That did the trick when we added a key EnableCommonNameFallbackForLocalAnchors so that didn't ding our users either.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-25-2017 05:14 AM
Great thanks to all for the above tips, Chrome works again for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2017 08:58 PM
Thank you @nsantoro for your generous code. I copied them into TextEdit and saved it as extension .mobileconfig. When I try to upload it from Configuration Profile in JSS, it didn't allow me. However, I got it working by creating com.google.chrome.plist file with the following code:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>EnableSha1ForLocalAnchors</key>
<true/>
</dict>
</plist>
I then uploaded to Configuration Profile section in the JSS by creating a new one and upload the plist file in the Custom Settings. Distribute to the iMac and it worked.
Thank you everyone!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-12-2017 08:57 AM
@wangl2 This worked for me too - thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2017 03:18 PM
@Sterritt yea, not sure I'd ever enable EnableSha1ForLocalAnchors, with the move away from SHA-1, that sounds dangerous, guess depends on the situation.
We're looking at enabling EnableCommonNameFallbackForLocalAnchors if only to avoid a flood of Help Desk calls when we push 58 out to users, due to private PKI certs on a bunch'a servers lacking Subject Alternate Names.
I'd imagine it'll take some time for folks running private PKI certs on their servers to redo them to include Subject Alternate Names (SAN). Although it seems like Mozilla Firefox 48 and later flicked that switch.
https://donmontalvo.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-20-2018 02:15 PM
@Sterritt -happy to help! glad it worked out for you.