We use the Sophos cloud product, and we deploy and monitor it with several policies and smart groups defined by extension attribute values.
When the Sophos cloud agent is installed on a client machine, the agent attempts to register itself with the Sophos's servers. If the registration succeeds, the result is a properly managed agent and client.
The problem is that the agent will only attempt to register itself once. If the agent fails to register, it will never attempt to register again. This results in a misconfigured unmanaged agent on a client machine, which means that:
- the Sophos agent does not update
- the Sophos agent does not apply or enforce the policies that you've crafted within Sophos
- the client machine does not appear in the Sophos cloud adminsitration console
- the Sophos agent will not inform that user that there is a registration issue
When the registration problem is coupled with the fact that Sophos does not provide a great way to collect detailed information about the status of the cloud agent via the command line, it can be a bit difficult to identify Sophos cloud agent issues within a fleet of laptops from within the JSS. And if an agent failed to register, it won't appear in the Sophos cloud adminsitration console, so it is hard to track there too.
Thankfully there are two things we can use to our advantage.
- From the command line, you can run the "sophosupdate" binary
- If the update binary fails, it will give an exit code that is not zero, and we can capture that exit code
Below is the primary extension attribute that I've created to help monitor this.
- If Sophos is not installed, the EA will be set to "No update client"
- If Sophos is installed and updates properly or the client does not have a valid internet connection, the exit code will be zero (the latter means that we won't get false-positives from a bad network connection)
- If Sophos is installed and fails to update properly, which typically indicates that there is a registration issue or other failure, the exit code will be non-zero
#!/bin/bash
# Run the Sophos update
# Get the Sophos update location
sophos_path=`which sophosupdate | grep -A1 sophosupdate`
echo
# If the file exists...
if [ -e "$sophos_path" ]; then
echo "Running Sophos update located at $sophos_path"
$sophos_path
result=`echo $?`
else
echo "The Sophos update client was not found at $sophos_path"
result="No update client"
fi
echo "<result>${result}</result>"
exit 0Two smart groups are defined by the results of this EA. One monitors whether the Sophos update binary exists, and the other monitors whether the Sophos update binary exited with an error.
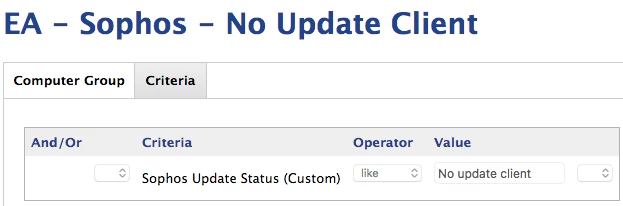
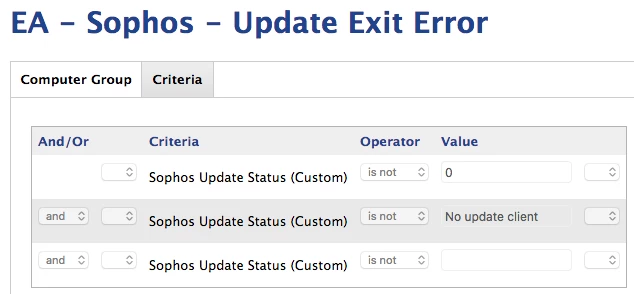
And we tie those into some other policies that automatically install or uninstall-reinstall Sophos as necessary and that file helpdesk tickets for ongoing issues related to clients with Sophos cloud agent issues.
I hope others find this helpful.


