HI ,
I've been trying to get new recovery key and store them in JSS with no luck .
I set it as it says on manuals :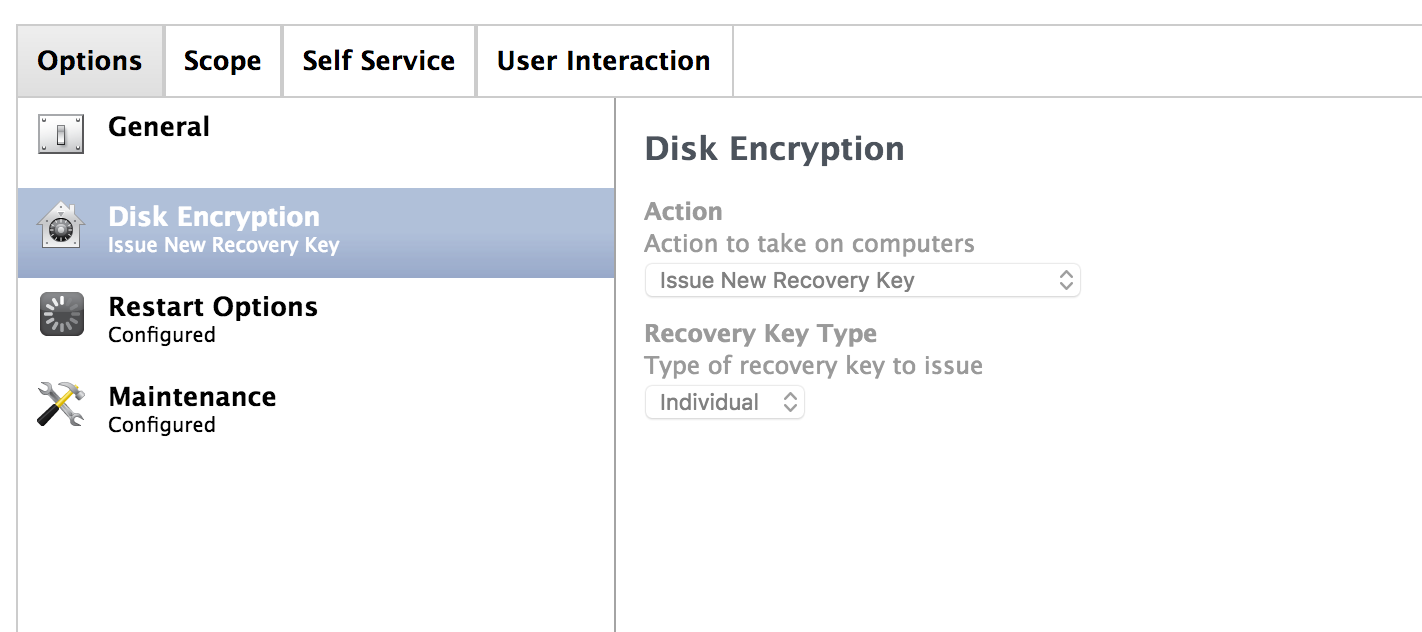
it get it fails but no errors and no key :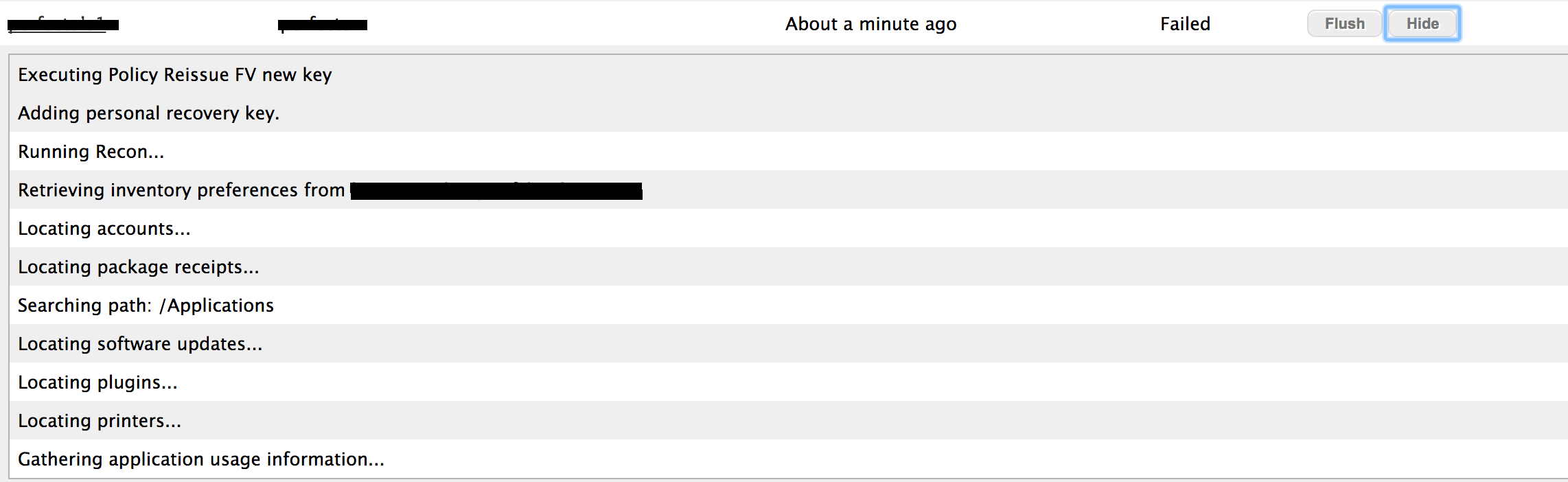
anyone made it work? there is a bug I'm not aware of ?
Regards ,
Meir
 +13
+13Do you already have keys for these machines escrowed into the JSS, or does the management account have FV access?
It's a machine with FV2 enabled before it added to JSS , I got no keys for it .
the enrollment have been done via url jss cloud , how can I know if the management account is FV enabled ?
 +8
+8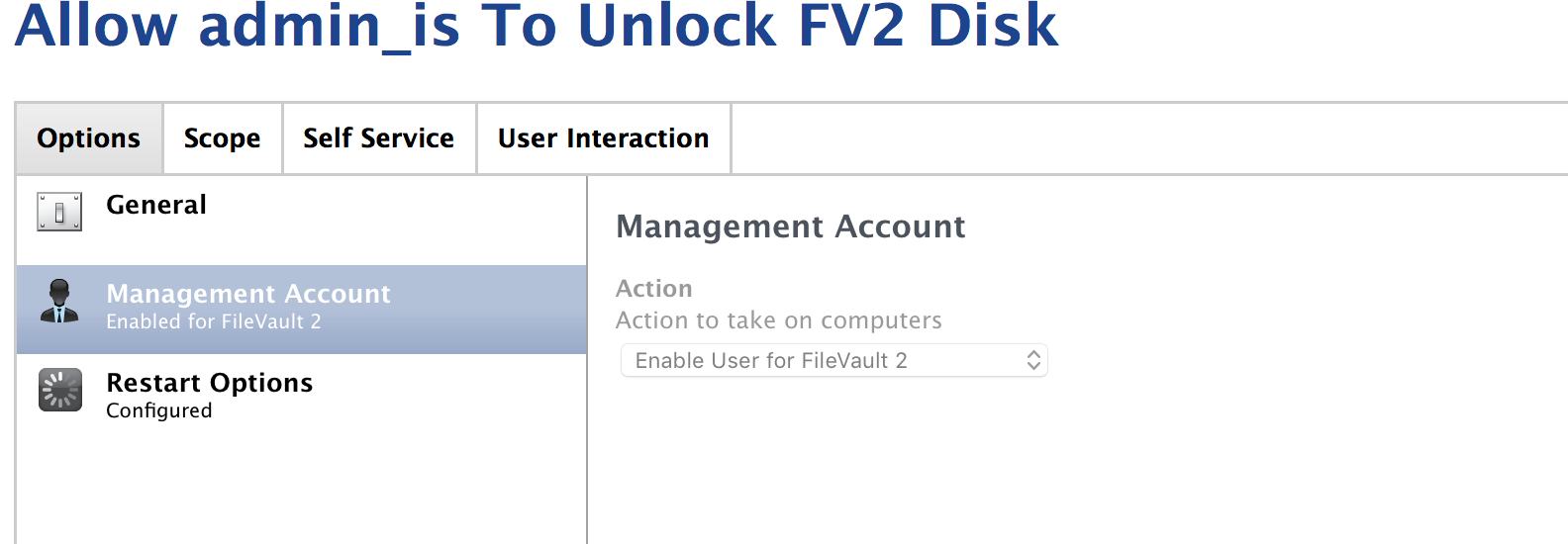
You then need a policy that has the "Capture Recovery Key" payment within disk encryption enabled. If you run the "capture key" policy with with my pictured policy and your pictured config profile enabled and you STILL don't get a key, it's possible that the machine simply needs to be decrypted, and then re-encrypted again via policy.
 +5
+5Maybe someone can clarify, but is it even possible to re-direct recovery keys if you're not applying a disk encryption configuration from casper?
 +8
+8@seann Absolutely - say the machine is already encrypted because a user did it on their own, or you've moving to managed encryption using JAMF from another product. Then you simply re-issue a recovery key so it escrows in the JSS.
tried to add filevault management account and I get this error :
Executing Policy Enable FV2 Management account
Adding user to filevault
Error adding user to FileVault: Added users failed error.
what am I missing?
 +6
+6Enabling the management account will only work if there is a valid individual recovery key already escrowed. If you don't have one already, scope a configuration profile to redirect the key to the JSS. Then make sure that the recovery key is valid. If it isn't, use a script to generate the key using a FileVault-enabled account's credentials. I'm on mobile but I can expand further.
 +11
+11@m3ir ... here is the script for redirect. Follow @andykang directions and use this script..
#!/bin/bash
####################################################################################################
#
# Copyright (c) 2013, JAMF Software, LLC. All rights reserved.
#
# Redistribution and use in source and binary forms, with or without
# modification, are permitted provided that the following conditions are met:
# * Redistributions of source code must retain the above copyright
# notice, this list of conditions and the following disclaimer.
# * Redistributions in binary form must reproduce the above copyright
# notice, this list of conditions and the following disclaimer in the
# documentation and/or other materials provided with the distribution.
# * Neither the name of the JAMF Software, LLC nor the
# names of its contributors may be used to endorse or promote products
# derived from this software without specific prior written permission.
#
# THIS SOFTWARE IS PROVIDED BY JAMF SOFTWARE, LLC "AS IS" AND ANY
# EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
# WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
# DISCLAIMED. IN NO EVENT SHALL JAMF SOFTWARE, LLC BE LIABLE FOR ANY
# DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
# (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
# LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
# ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
# (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
# SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
#
####################################################################################################
#
# Description
#
# The purpose of this script is to allow a new individual recovery key to be issued
# if the current key is invalid and the management account is not enabled for FV2,
# or if the machine was encrypted outside of the JSS.
#
# First put a configuration profile for FV2 recovery key redirection in place.
# Ensure keys are being redirected to your JSS.
#
# This script will prompt the user for their password so a new FV2 individual
# recovery key can be issued and redirected to the JSS.
#
####################################################################################################
#
# HISTORY
#
# -Created by Sam Fortuna on Sept. 5, 2014
# -Updated by Sam Fortuna on Nov. 18, 2014
# -Added support for 10.10
# -Updated by Sam Fortuna on June 23, 2015
# -Properly escapes special characters in user passwords
#
####################################################################################################
#
## Get the logged in user's name
userName=$(/usr/bin/stat -f%Su /dev/console)
## Get the OS version
OS=`/usr/bin/sw_vers -productVersion | awk -F. {'print $2'}`
## This first user check sees if the logged in account is already authorized with FileVault 2
userCheck=`fdesetup list | awk -v usrN="$userName" -F, 'index($0, usrN) {print $1}'`
if [ "${userCheck}" != "${userName}" ]; then
echo "This user is not a FileVault 2 enabled user."
exit 3
fi
## Check to see if the encryption process is complete
encryptCheck=`fdesetup status`
statusCheck=$(echo "${encryptCheck}" | grep "FileVault is On.")
expectedStatus="FileVault is On."
if [ "${statusCheck}" != "${expectedStatus}" ]; then
echo "The encryption process has not completed."
echo "${encryptCheck}"
exit 4
fi
## Get the logged in user's password via a prompt
echo "Prompting ${userName} for their login password."
userPass="$(/usr/bin/osascript -e 'Tell application "System Events" to display dialog "Enter your computer login password to unlock FileVault2 (Casper Admin):" default answer "" with title "Login Password" with text buttons {"Ok"} default button 1 with hidden answer' -e 'text returned of result')"
echo "Issuing new recovery key"
if [[ $OS -ge 9 ]]; then
## This "expect" block will populate answers for the fdesetup prompts that normally occur while hiding them from output
expect -c "
log_user 0
spawn fdesetup changerecovery -personal
expect "Enter a password for '/', or the recovery key:"
send "{${userPass}}"
send
log_user 1
expect eof
"
else
echo "OS version not 10.9+ or OS version unrecognized"
echo "$(/usr/bin/sw_vers -productVersion)"
exit 5
fi
exit 0@JustDeWon I actually tried this script at first and it seemed to start working , but I stopped since I thought there is easy built in method doing it . seems there isn't , so I'll test it again , Thanks!
@andykang Thanks for the heads up !
Update : when trying running this script on machine , it asks for user password and then I get this error :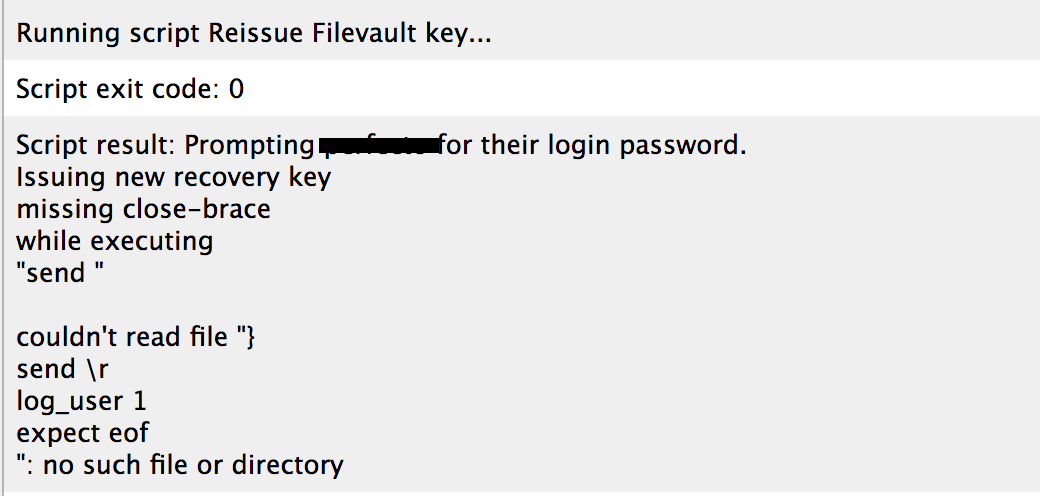
the target machine is 10.12.4 , if it's make any difference .
is something wrong with it ? or is there a mismatch with Sierra ?
Regards ,
So I've been doing this very thing from a migration from an old JSS to a new JSS. I followed @rtrouton's guidance HERE to create a plist with the recovery key and add it to my existing FileVault users. At that point, It was easy to re-capture a new key. Our JAMF Service/Management account is not default FV2 enabled, so I had to add the plist, import it, and then regenerate the key. I also follow up deleting that plist file since it's got our management account in clear text.
I do mine in sequential steps to catch failures so step 1 is push the key via a casper package, 2 runs the import key into FV2, 3 is generate the new recovery key, and 4 sends a trigger to delete the plist I pushed out.
 +6
+6Try this script as it's newer than the one posted above.
https://github.com/JAMFSupport/FileVault2_Scripts/blob/master/reissueKey.sh
#!/bin/bash
####################################################################################################
#
# Copyright (c) 2013, JAMF Software, LLC. All rights reserved.
#
# Redistribution and use in source and binary forms, with or without
# modification, are permitted provided that the following conditions are met:
# * Redistributions of source code must retain the above copyright
# notice, this list of conditions and the following disclaimer.
# * Redistributions in binary form must reproduce the above copyright
# notice, this list of conditions and the following disclaimer in the
# documentation and/or other materials provided with the distribution.
# * Neither the name of the JAMF Software, LLC nor the
# names of its contributors may be used to endorse or promote products
# derived from this software without specific prior written permission.
#
# THIS SOFTWARE IS PROVIDED BY JAMF SOFTWARE, LLC "AS IS" AND ANY
# EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
# WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
# DISCLAIMED. IN NO EVENT SHALL JAMF SOFTWARE, LLC BE LIABLE FOR ANY
# DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
# (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
# LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
# ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
# (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
# SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
#
####################################################################################################
#
# Description
#
# The purpose of this script is to allow a new individual recovery key to be issued
# if the current key is invalid and the management account is not enabled for FV2,
# or if the machine was encrypted outside of the JSS.
#
# First put a configuration profile for FV2 recovery key redirection in place.
# Ensure keys are being redirected to your JSS.
#
# This script will prompt the user for their password so a new FV2 individual
# recovery key can be issued and redirected to the JSS.
#
####################################################################################################
#
# HISTORY
#
# -Created by Sam Fortuna on Sept. 5, 2014
# -Updated by Sam Fortuna on Nov. 18, 2014
# -Added support for 10.10
# -Updated by Sam Fortuna on June 23, 2015
# -Properly escapes special characters in user passwords
# -Updated by Bram Cohen on May 27, 2016
# -Pipe FV key and password to /dev/null
# -Updated by Jordan Wisniewski on Dec 5, 2016
# -Removed quotes for 'send {${userPass}}' so
# passwords with spaces work.
#
####################################################################################################
#
## Get the logged in user's name
userName=$(/usr/bin/stat -f%Su /dev/console)
## Get the OS version
OS=`/usr/bin/sw_vers -productVersion | awk -F. {'print $2'}`
## This first user check sees if the logged in account is already authorized with FileVault 2
userCheck=`fdesetup list | awk -v usrN="$userName" -F, 'index($0, usrN) {print $1}'`
if [ "${userCheck}" != "${userName}" ]; then
echo "This user is not a FileVault 2 enabled user."
exit 3
fi
## Check to see if the encryption process is complete
encryptCheck=`fdesetup status`
statusCheck=$(echo "${encryptCheck}" | grep "FileVault is On.")
expectedStatus="FileVault is On."
if [ "${statusCheck}" != "${expectedStatus}" ]; then
echo "The encryption process has not completed."
echo "${encryptCheck}"
exit 4
fi
## Get the logged in user's password via a prompt
echo "Prompting ${userName} for their login password."
userPass="$(/usr/bin/osascript -e 'Tell application "System Events" to display dialog "Please enter your login password:" default answer "" with title "Login Password" with text buttons {"Ok"} default button 1 with hidden answer' -e 'text returned of result')"
echo "Issuing new recovery key"
if [[ $OS -ge 9 ]]; then
## This "expect" block will populate answers for the fdesetup prompts that normally occur while hiding them from output
expect -c "
log_user 0
spawn fdesetup changerecovery -personal
expect "Enter a password for '/', or the recovery key:"
send {${userPass}}
send
log_user 1
expect eof
" >> /dev/null
else
echo "OS version not 10.9+ or OS version unrecognized"
echo "$(/usr/bin/sw_vers -productVersion)"
exit 5
fi
exit 0Thanks @andykang
with this updated script , I don't get any errors
but still my FileVault is not configured in management pane .
what still can be wrong ?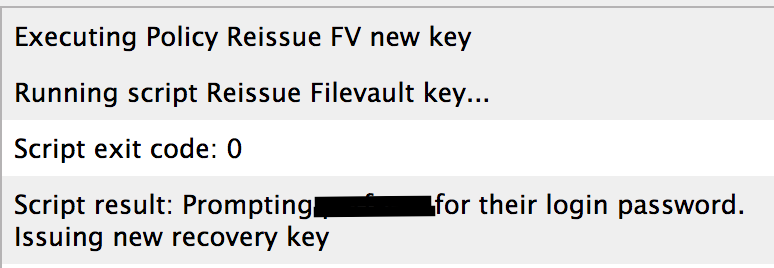
 +6
+6Do you have a configuration profile to redirect FV keys to the JSS?
First put a configuration profile for FV2 recovery key redirection in place.Ensure keys are being redirected to your JSS.
 +11
+11@m3ir .. it's prompting them for the password they used to enable FileVault2.. If they don't remember it, then you may have to reset their FileVault2 password, then try running the script again.
 +4
+4I'm having sort of the same problem.
I can get filevault to enable and pull the keys back to the JSS. That all works. However when I try to use this script to make our users have to enter their password and make a new one, they never get anything pop up on their screen asking them to enter their password and it fails.
It only works if I perform a sudo jamf policy on their machine.
If you're not able to get filevault enabled, try running a policy that turns on disk encryption policy and configure the disk encryption payload for current or next user and push that policy. We use ours on logout and it works nicely.
 +3
+3Folks,
I'm trying to use the script above.
It's getting the result:
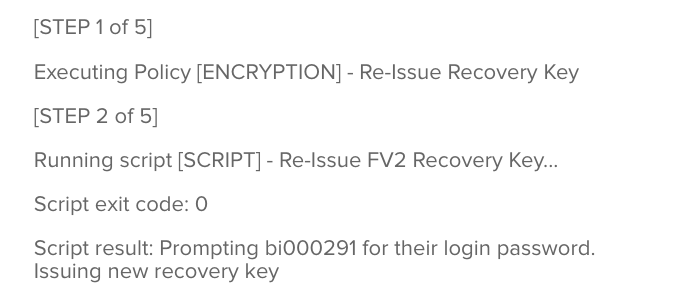
Does anyone knows how long before the new key is generated?
It's just in time?
Thanks in advance,
Use the latest script from : https://github.com/jamf/FileVault2_Scripts/blob/master/reissueKey.sh
just make sure you have
did you check "Update Inventory" after the running the script?
try run "jamf recon" on machine , or even do a restart and then "jamf recon".
Good Luck!
Hi everyone! I'm the maintainer of the jss-filevault-reissue workflow referenced above, and I've got a quick update that may be of interest to many of you.
My team has published a new tool called Escrow Buddy, which regenerates FileVault keys at the loginwindow, thus avoiding the need to prompt users for their password later. It should be suitable as a drop-in replacement for my previous jss-filevault-reissue workflow at most organizations.
You can read more in this announcement on the Netflix Tech Blog, and this post on my site specifically covers migrating from my old workflow to Escrow Buddy. Escrow Buddy's source code and installer are available on GitHub.
Thanks!
Hi everyone! I'm the maintainer of the jss-filevault-reissue workflow referenced above, and I've got a quick update that may be of interest to many of you.
My team has published a new tool called Escrow Buddy, which regenerates FileVault keys at the loginwindow, thus avoiding the need to prompt users for their password later. It should be suitable as a drop-in replacement for my previous jss-filevault-reissue workflow at most organizations.
You can read more in this announcement on the Netflix Tech Blog, and this post on my site specifically covers migrating from my old workflow to Escrow Buddy. Escrow Buddy's source code and installer are available on GitHub.
Thanks!
Wow, that's brilliant, thanks.
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.
Sorry, we're still checking this file's contents to make sure it's safe to download. Please try again in a few minutes.
OKSorry, our virus scanner detected that this file isn't safe to download.
OK