- Jamf Nation Community
- Products
- Jamf Pro
- Re: JAMf and Microsoft Teams - limit access to spe...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
JAMf and Microsoft Teams - limit access to specific tenant ID
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-28-2022 07:02 PM
Hi, First time poster here.
We have a fleet of student iPads that we're managing through Jamf, and that have Microsoft Teams deployed on them for classwork.
The students have learned that, if they tap "+ Add Account" within Teams, they can connect a personal Teams account within the app, and have been using this to send notes in class without oversight.
We've been able to limit the Windows Desktop Teams App so that it'll only allow accounts on a specific Teams "tenant ID" to sign in - and we're hoping that a similar capability is possible in the iOS Teams app via Jamf, but have had trouble finding any information about it.
Is this something that anyone has managed to accomplish, or has advice about? I'm relatively new to Jamf, so step-by-step guides are greatly appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-30-2022 06:24 PM
I ran into a similar issue and unfortunately, wasn't able to determine how to do this on iOS or macOS.
Also, this is a rabbit hole that will send you spiraling. Even though you block the ability within the app, will you also be preventing them from navigating to teams.microsoft.com, creating a personal Teams account and using the web interface in the same manner? Ultimately, this will have to fall to classroom management to monitor devices while in class and punish "passing notes" when found. For after school hours, you could use your institution filter to prevent access to Teams, thereby blocking both the app and website, so that they could not use it for a chat room.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-01-2022 05:14 PM
It has definitely been a rabbit hole so far.
I've already told the teachers that, even if we get this sorted, the students will still be able to use other Teams accounts, if they ever discover that web browsers exist (/s) - but ours is not to question why, ours just to do or die, it seems.
I'll see if I can make the suggestion of using the "View Student Screen" capability of Apple Classrooms as an added form of supervision - but I doubt that'll go over well.
(Fortunately it's not a boarding school, and the iPads don't leave the premises, so after-hours isn't an issue)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-09-2022 08:44 AM
I was able to limit app logins using an app config. Doing so removed the "Add Account" button and only allows the user assigned to the iPad to log in to the Teams app. I haven't tested this on macOS but I would imagine it works the same.
MS Teams App Config:
<dict>
<key>IntuneMAMAllowedAccountsOnly</key>
<string>Enabled</string>
<key>IntuneMAMUPN</key>
<string>$EMAIL</string>
</dict>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2023 05:30 AM
In case anyone is referencing this, the solution I posted back in December of 2022 no longer works. The app config has no effect of restricting users to a specific tenant. As of this posting, I am unaware of a method to restrict the tenant without dual-enrolling devices into Jamf AND Intune. Say what you will, but co-managing in 2 MDMs looks and sounds like total chaos.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-25-2023 01:47 PM
I used the following App Configuration and it was working:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>IntuneMAMAllowedAccountsOnly</key>
<string>Enabled</string>
<key>IntuneMAMUPN</key>
<string>%EMAIL%</string>
</dict>
</plist>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-25-2023 06:15 PM
How are you using that app config (as written) with Jamf? The formatting is incorrect and "%EMAIL%" isn't a variable in Jamf.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-26-2023 06:12 AM
We are using Jamf School. Not sure if this makes a difference.
There is a section under the options area for Show Advanced Options with a check box to add a managed configuration. Then you can add the xml code in the box.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-31-2023 06:43 AM
@awrightfrhc , I don't mean to be pedantic, but when you deploy the app config you listed earlier via Jamf School, it removes the "Use another account" button at the MS Teams login screen?
I'm asking because I'm currently in week 4 of an open support ticket with Microsoft, and getting them to understand the issue has been challenging. It doesn't help that they have constantly bounced me between their internal teams.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-31-2023 09:08 AM
It still has the "Use another account" button but it restricts it to a Microsoft account. There is also an "Account Restrictions" button that says Only accounts added by your IT admin are allowed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-31-2023 09:21 AM
Ah, so yours isn't working either. Whew!
As long as that "Use another account" button is visible, students can use any Microsoft account, so they aren't restricted to just your tenant, which is the entire point of deploying this app config.
Our goal(which the app config formerly helped with by removing the "Use another account" button) is to prevent kids from signing in with their Xbox Live accounts (or other personal MS accounts) and circumvent all of the MS Teams restrictions we have in place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-14-2023 11:03 AM
We are having the same issue and concern as well. It was working perfectly earlier in year and recently brought back the "Use Another Account" button. We have been testing it and noticed if they leave the Teams App and go back into Teams it does then apply the account restrictions and logs out the "personal" account. Is this the same behavior everyone else is seeing? This is still problematic as the student could take the time to log back in the "personal" account and gain access to Chat and other items we are trying to prevent. Does anyone have a case open with Microsoft?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2023 04:37 AM
I haven't noticed that particular behavior. In my last few months of testing, I can't get the "Use Another Account" button to disappear at all.
I've been trying to work with MS support since February, but they keep pawning me off to Intune support, and I have to close the ticket and start over again. I'll post it here if they ever acknowledge and/or resolve this issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2023 06:55 AM
you may want to write an additional key in com.microsoft.teams.plist as below.
defaults write /Library/Preferences/com.microsoft.teams.plist RestrictTeamsSignInToAccountsFromTenantList your Microft tenant ID
This works for me and able to block personal email login over MS Teams.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2023 07:00 AM
@Himanshu_panwar , While you are correct about the tenant key in the plist for macOS, this doesn't help with iPadOS.
The app config payload is the only option to configure an application in iPadOS. So far, the Microsoft-recommended app config hasn't been working since December '22.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-03-2024 04:44 AM
Has anyone had any success with this please? I saw an earlier mention of Intune - can Intune be used to restrict to a specific Tenant ID?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-03-2024 05:08 AM
This looks a possible solution but it's a beast to implement. Looks like it will apply tenant wide, cannot apply per user so you need to be committed: https://techcommunity.microsoft.com/t5/microsoft-entra-blog/tenant-restriction-v2-is-now-public-prev... I haven't tried it yet, will investigate further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-03-2024 08:12 AM
@taz_mcbr1 , It's definitely possible to achieve this through Intune/Jamf co-management; however, you are correct in stating that this is quite the beast to implement. Implementing co-management seems like an extraordinary amount of effort to work around an issue that Microsoft created and should fix.
Back in Feb 2023, I opened a ticket with Microsoft support, and after 10 months of back and forth, I finally got in touch with a support advisor who was willing to help push this through. As of Nov 2023, Microsoft has finally understood and acknowledged the issue with the MS Teams iOS/iPadOS app, and their MS Teams engineering group is working to fix it.
Here is a snippet from my last communication with Microsoft Support on Nov 27th, 2023:
As we had informed you earlier that we had engaged our Engineering (Product Group) to resolve this Issue on top priority. We have received an update from Engineering & they have considered this Issue as a Bug & created an Internal Work item to fix the Bug.
Unfortunately, we do not have any ETA for the resolution of this Bug as Engineering will be working from Backend on the Bug & shall be deploying the Fix accordingly.
As there is no action pending from our end at this moment hence, I wanted to follow up with you to see if we can archive this case for now. I have added all the Bug Details & Engineering discussion in the same Case & you can use it as a Reference to Track the progress of this Bug.I am foolishly optimistic that they will release a Teams iOS/iPadOS update for this in Q1 or Q2 of 2024.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-29-2024 08:43 AM
Hi Palmna,
Would you mind letting us know if the config start working again please? I've also raised a feature request at Jamf end - please upvote if useful. https://ideas.jamf.com/ideas/JN-I-28234
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-07-2024 08:26 AM
Good news for anyone following this thread - Microsoft confirmed today that it is a known bug that the key will not work on any MDM except Intune any more. The fix is scheduled to be released 31st March 2024. Many thanks to contributors like @palmna who also took the time to raise it with Microsoft.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-07-2024 08:34 AM
@taz_mcbr1, I'm glad to hear they've further confirmed the issue. I'm curious where you got the release date info. Can you share a link?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2024 01:26 AM
We are a Microsoft Gold Partner, so used our internal channels to reach out to the Microsoft team. The person I spoke to confirmed it was a known issue, there was a ticket number and that had a rollout date. However the ticket was internal view only so they couldn't give me the ID and they did caveat that MS had rolled out a lot of Teams changes lately (with the new app) so hopefully it wouldn't get bumped. I have a Microsoft ticket number and they said if it didn't rollout on that date, to reopen the ticket and the engineer would be able to use that to track the linked internal ticket and give me an update. I hope that helps - I will post back if I hear anything else.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-02-2024 07:05 AM
@taz_mcbr1, by chance did you hear if MS this fix on the 31st?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-02-2024 07:25 AM
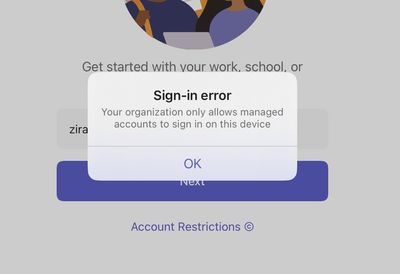
@mlefever, Good news!
I can confirm that the Teams app (version 6.6.0) is once again respecting the App config payload. Now, when I try to log in using a personal account, I get a "Your organization only allows managed accounts to sign in on this device" message:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-02-2024 07:38 AM
Great! I just confirmed this as well. Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-04-2024 12:53 PM
I have also validated that the following app config works, allowing you to specify the domain if they try to use another account. Just change domain.org to your domain.
<dict>
<key>domain_name</key>
<string>domain.org</string>
<key>IntuneMAMAllowedAccountsOnly</key>
<string>Enabled</string>
<key>IntuneMAMUPN</key>
<string>$EMAIL</string>
</dict>