- Jamf Nation Community
- Products
- Jamf Pro
- Jamf Pro 10.34.2 Now Available
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Jamf Pro 10.34.2 Now Available
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2021 12:25 PM - edited 12-20-2021 06:24 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 12:40 PM
tough time to take out the cloud when people are also trying to remediate log4j with Jamf. Hope this includes a way for Jamf to detect 3rd party log4j issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2021 07:18 AM - edited 12-18-2021 12:15 PM
@swapple wrote:tough time to take out the cloud when people are also trying to remediate log4j with Jamf. Hope this includes a way for Jamf to detect 3rd party log4j issues.
they added this to Jamf Protect this week - "SuspiciousJavaActivity
This analytic will show when the curl command or an interactive bash shell is executed under Java. To date these are the most common actions being taken by successful log4j exploits. These actions might also be performed by legitimate Java applications in your environment. It is up to the analyst to determine if the detected application should be performing these actions."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-18-2021 02:13 PM
But did the figure this out 2 seconds before they did the update so there was no choice but to kick everyone working in Jamf out?? No time to schedule it? No notifications???
We understand the need to do it. The method has destroyed a lot of confidence in Jamf that it was done with very little notice.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-18-2021 03:24 PM
I don't know what you're complaining about. They sent out a mail during my lunch break, 20 mins before they kicked it off, outlining an undefined start time of "soon", and with no expected completion time. lol.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 12:50 PM
any ideas on ETA? This literally went down as we are enrolling several devices for EOD delivery
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 12:52 PM
Was there communication or notice for the cloud maintenance? The previous release note said that the cloud instance was mitigated already. Why are we doing this during the day now and not when 10.34.2 was first released? This action has disturbed my works on remediating Log4J with my security dept and my companies Mac and iOS provisioning.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:01 PM
@ShadowGT
I believe the original patch secured for version .15 which we have learned introduced their own vulnerabilities which version .16 patches.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:04 PM
@atomczynski That makes sense and thank you for the info, but I'm more concerned about the unscheduled maintenance downtime during working hours.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:09 PM
This is unfortunate timing on the maintenance period. ETA please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:19 PM
Agree here, the maintenance period should had been communicated before it even started.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:20 PM
No access to admin console. This is a major disruption to my hospital operations!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:25 PM
All good valid points.
I do belive they either saw it already being exploited or weighted the potential risk in future scheduling vs an operations disruptions and decided to go with the route they did.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:31 PM
The timing kinda stinks, I was in the middle of a Tanium agent update deployment to my fleet...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:31 PM
This is completely unacceptable. Zero communication of a "scheduled" maintenance in the middle of the work day? If any of us did this, we'd be shown the door. There had better be a good explanation for this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 06:26 PM
Communication was sent via email, prior to the change being implemented.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-20-2021 11:15 AM
Thats a terrible reply and look at the situation. Giving a heads up 20 minutes before taking the instance out is not acceptable by any means unless they actively noticed an attack ongoing. Most of us were hit in the middle of the day with no warning, I don't check my email every minute, as my workflow does not allow for this. Taking down an instance with close to no warning is unacceptable in every sense of the word. While you are technically correct, the issue is not whether or not an email or communication went out. But the shoddy and terrible timing and effects it had for those of us caught with little to no warning. Don't be so glib with your response, just because you may not have been effected, doesn't mean the rest of us weren't.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-20-2021 11:19 AM
Never claimed I wasn't affected and never claimed anyone else was. I merely stated communication was sent out. Also, you bring up a good point, that to my knowledge has not been determined or at least publicly communicated: that is that none of us know whether an attack was active or not. Don't be so quick to rush to conclusions is merely all i was trying to infer with my factual response.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-20-2021 11:22 AM
I agree with your last part, and understand where you are coming from as your answer was technically correct, but as you can see from the myriad of responses here, the timing and execution was terrible. Even taking that into account, the communication was also incredibly poor. The response you are posting on this thread (in a few locations) just comes off as a little tone deaf considering the impact it had on a lot of us. I meant no attack or disrespect by any means, so I apologize if it comes off that way, but there were a lot of issues introduced to our environment due to computers being knocked offline (server connections) during usage that we are still trying to get resolved
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-20-2021 11:25 AM
I certainly understand, we were in the middle of testing some detection scripts for log4j and poof, gone. I thought it would be around an hour tops, but nope, quite an extended outage. I understand the pain, but also want to cut JAMF some slack in the sense that I've not seen anything else like this in the 5 or so years I've been a customer and due to the severity of the vulnerability/the unknown of whether there was an actual attack in place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-20-2021 11:30 AM
You do bring up a good point, Jamf has been fairly solid overall, and frankly their patch policy has been on the better end of companies I use. I think this is one of those "I'm frustrated at the situation" kind of things. Especially given the impact and timing, not just in the day/week, but just right before the holidays, with some folks having smaller crews, etc. My thoughts are they had an active attack or proof of one that happened since the last patch (if I remember correctly there were 2 in a short window) but either way. Sorry for the post venting, and hope you have a happy holiday season!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-20-2021 11:31 AM
All valid points for venting 🙂 Merry Christmas Friend and a Happy New Year!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:36 PM
Dang near had a heart attack when one of my techs messaged me "Hey is our Jamf portal down?"
Glad we're getting Log4J mitigation, but it would've been nice to get some advanced warning on this so I could alert my team 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:38 PM
4pm on a Friday, thanks JAMF.....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2021 01:42 PM - edited 12-17-2021 01:44 PM
.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:45 PM
When it comes to mitigating vulnerabilities, one thing is for sure, Jamf is bad @$$!
https://donmontalvo.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:46 PM
Yeah this upgrade is pretty bad timing for us as well ... Pressure changes everything and it appears we customers get the short end of the stick 😕
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 01:55 PM
Ouch. I get why JAMF would want to get this patched ASAP. But just a bit of communication would have been nice so we can prepare on what we can and can't do during the update.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 02:00 PM
Some links that might find a home in your browser bookmarks, or maybe a Jamf FAQ:
server-tools.jar
https://archive.services.jamfcloud.com/#jamf-pro-server-tools/release/latest/gui/
Jamf Pro Server Tools
https://account.jamf.com/products/other/jamf-pro-server-tools
Jamf Pro
https://account.jamf.com/products/jamf-pro
https://donmontalvo.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 02:01 PM
No communication regarding a mid afternoon maintenance window on a weekday? Ouch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 06:29 PM
Email communication was sent prior to start
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-20-2021 11:35 AM
sorry but 20 min before taking it down when a previous email stated nothing needed to be done is just crazy and would be viewed as completely not okay in any corp environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-20-2021 11:38 AM
an emergency change control for an active exploited attack like this is acceptable to me as a customer especially considering the repercussions if said attack would have been successful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 02:12 PM
I was in the middle of wiping several machines campus wide, I got get some water and come back to the admin portal being down. Helluva way to not get ahead. Oh well, hopefully it's back up soon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 02:47 PM
appreciate the patch, but would really loved more email communication on when this was happening...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 02:56 PM
Really disappointed about the timing and lack of warning here. Doing enrollments and I was already cutting it close on an EOD deadline that I now won't be able to meet. Business will be negatively impacted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 02:57 PM
I am getting blown up by co-workers and will now have to have meeting about this. If the patch took 15 mins fine, but this? It's been over 2 hours in the middle of the work day!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 03:20 PM
Is there an estimated return to service? It’s been down for hours.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 03:30 PM
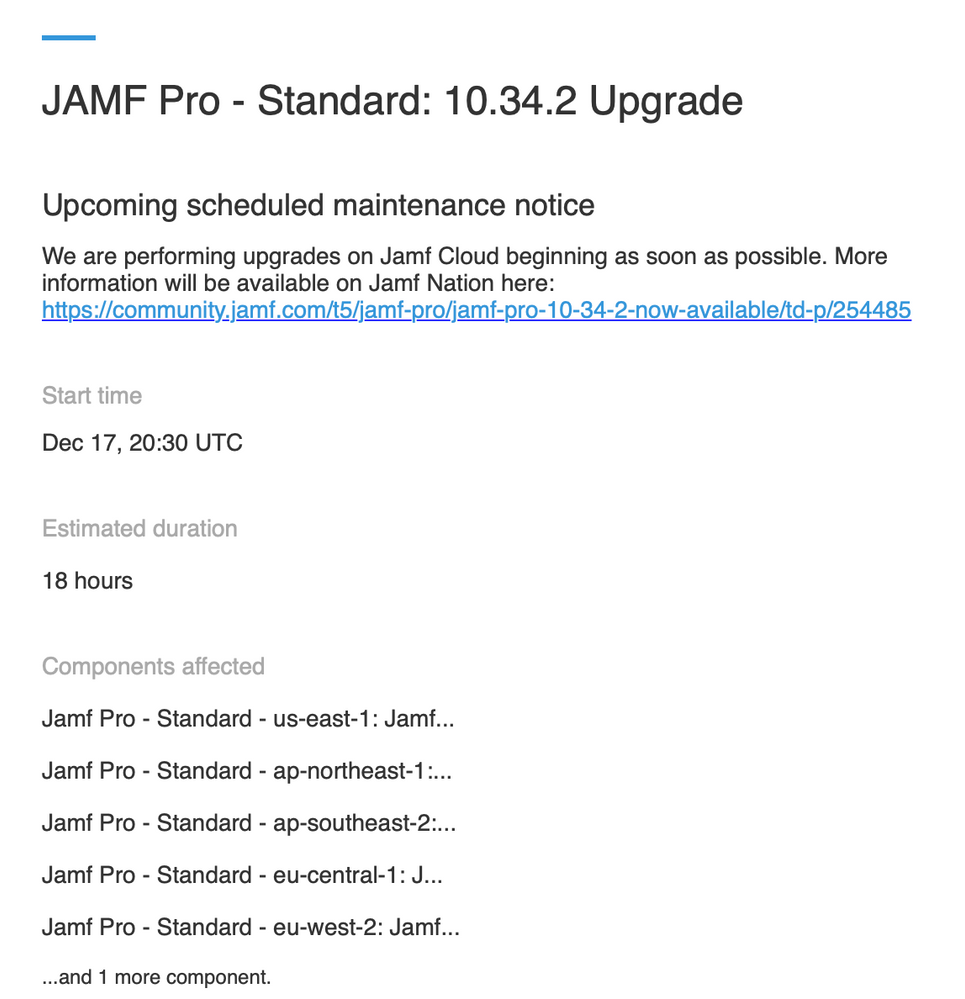
Looks like they were planning for a long one per the (separate!!!???) maintenance email:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2021 03:38 PM
Eighteen hours??? 😱 Oh no...