- Jamf Nation Community
- Products
- Jamf Pro
- Re: jamfAAD continues to request enrollment even t...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-16-2022 10:08 AM
Users that have already properly enrolled into Intune and completed enrollment continue to get pop ups of jamfAAD.
I have verified in Intune that the device is enrolled AND the policy was completed successfully in JAMF. This pop up continues to run and request users to continue. This sometimes disrupts end user workflows or presentations while on a zoom call. Is there a setting possible in the profile where I can set the retry option to 0 if already successfully completed. I've tried flushing the logs, delete the device from Intune, then re-enroll the mac back but users still get prompted. Even when I've un-scoped the policy from the user they still get the pop up. Possibly coming form the Intune side? I'm open to any ideas.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-16-2022 11:08 AM
To clear that prompt, I ran the script below, removed Company Portal App, and removed the device from InTune. In your case, you'd re-enroll into Intune and see if it's better from a clean slate.
Forgot where I found the script below, but thank you to that person.
#!/bin/bash
#macOS WPJ and jamfAAD item clean up
#By Bryce Carlson - 3/2/2021
#
#This script will remove the Workplace Join items made by Company Portal durring a device registration. It will also clear the jamfAAD items from the gatherAADInfo command run after a sucessful WPJ
#Clearing this data will allow for a re-registration devices side.
#
#NOTE: THIS SCRIPT WILL NOT CLEAR AZURE AD RECORDS (those are created by Company Portal). IT MAY CLEAR MEM RECORDS IF A JAMFAAD GATHER AAD INFO COMMAND RUNS AFTER THIS AS THE AAD ID IS NOW MISSING. THIS WILL RESULT IN A DEACTIVATION OF THE DEVICE RECORD SENT FROM JAMF PRO TO AAD (AND AAD TO MEM).
#
#variable to run as current user
currentuser=`stat -f "%Su" /dev/console`
#
#variable for current logged in user AAD ID cert. and WPJ key
AAD_ID=$(su "$currentuser" -c "security find-certificate -a -Z | grep -B 9 "MS-ORGANIZATION-ACCESS" | awk '/\"alis\"<blob>=\"/ {print $NF}' | sed 's/ \"alis\"<blob>=\"//;s/.$//'")
#CERT_BY_SHA=$(su "$currentuser" -c "security find-certificate -a -Z | grep -B 9 "MS-ORGANIZATION-ACCESS" | grep "SHA-1" | awk '{print $3}'")
#
echo "Removing keychain password items for jamfAAD"
#jamfAAD items
su "$currentuser" -c "security delete-generic-password -l 'com.jamf.management.jamfAAD'"
rm -rf /Users/"$currentuser"/Library/Saved\ Application\ State/com.jamfsoftware.selfservice.mac.savedState
rm -r /Users/"$currentuser"/Library/Cookes/com.jamf.management.jamfAAD.binarycookies
rm -rf /Users/"$currentuser"/Library/Saved\ Application\ State/com.jamf.management.jamfAAD.savedState
su "$currentuser" -c "/Library/Application\ Support/JAMF/Jamf.app/Contents/MacOS/JamfAAD.app/Contents/MacOS/JamfAAD clean"
#
echo "Removing keychain password items for Company Portal app (v2.6 and higher with new com.microsoft.CompanyPortalMac bundle ID)"
#Company Portal app items
rm -r /Users/"$currentuser"/Library/Cookies/com.microsoft.CompanyPortalMac.binarycookies
rm -rf /Users/"$currentuser"/Library/Saved\ Application\ State/com.microsoft.CompanyPortalMac.savedState
rm -r /Users/"$currentuser"/Library/Preferences/com.microsoft.CompanyPortalMac.plist
rm -r /Library/Preferences/com.microsoft.CompanyPortalMac.plist
rm -rf /Users/"$currentuser"/Library/Application\ Support/com.microsoft.CompanyPortalMac
rm -rf /Users/"$currentuser"/Library/Application\ Support/com.microsoft.CompanyPortalMac.usercontext.info
su "$currentuser" -c "security delete-generic-password -l 'com.microsoft.CompanyPortal'"
su "$currentuser" -c "security delete-generic-password -l 'com.microsoft.CompanyPortalMac'"
su "$currentuser" -c "security delete-generic-password -l 'com.microsoft.CompanyPortal.HockeySDK'"
su "$currentuser" -c "security delete-generic-password -l 'com.microsoft.adalcache'"
su "$currentuser" -c "security delete-generic-password -l 'enterpriseregistration.windows.net'"
su "$currentuser" -c "security delete-generic-password -l 'https://device.login.microsoftonline.com'"
su "$currentuser" -c "security delete-generic-password -l 'https://device.login.microsoftonline.com/' "
su "$currentuser" -c "security delete-generic-password -l 'https://enterpriseregistration.windows.net' "
su "$currentuser" -c "security delete-generic-password -l 'https://enterpriseregistration.windows.net/' "
su "$currentuser" -c "security delete-generic-password -a 'com.microsoft.workplacejoin.thumbprint' "
su "$currentuser" -c "security delete-generic-password -a 'com.microsoft.workplacejoin.registeredUserPrincipalName' "
#
echo "Removing WPJ for Device AAD ID $AAD_ID for $currentuser"
su "$currentuser" -c "security delete-identity -c $AAD_ID"
#echo "Removing WPJ for Device AAD ID $AAD_ID for $currentuser from SHA hash $CERT_BY_HASH"
#
echo "Please REBOOT this macOS device to re-load the login.keychain and re-run the Azure Registration via Self Service AFTER you ensure device removal from AAD and MEM server side."
exit 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-16-2022 11:08 AM
To clear that prompt, I ran the script below, removed Company Portal App, and removed the device from InTune. In your case, you'd re-enroll into Intune and see if it's better from a clean slate.
Forgot where I found the script below, but thank you to that person.
#!/bin/bash
#macOS WPJ and jamfAAD item clean up
#By Bryce Carlson - 3/2/2021
#
#This script will remove the Workplace Join items made by Company Portal durring a device registration. It will also clear the jamfAAD items from the gatherAADInfo command run after a sucessful WPJ
#Clearing this data will allow for a re-registration devices side.
#
#NOTE: THIS SCRIPT WILL NOT CLEAR AZURE AD RECORDS (those are created by Company Portal). IT MAY CLEAR MEM RECORDS IF A JAMFAAD GATHER AAD INFO COMMAND RUNS AFTER THIS AS THE AAD ID IS NOW MISSING. THIS WILL RESULT IN A DEACTIVATION OF THE DEVICE RECORD SENT FROM JAMF PRO TO AAD (AND AAD TO MEM).
#
#variable to run as current user
currentuser=`stat -f "%Su" /dev/console`
#
#variable for current logged in user AAD ID cert. and WPJ key
AAD_ID=$(su "$currentuser" -c "security find-certificate -a -Z | grep -B 9 "MS-ORGANIZATION-ACCESS" | awk '/\"alis\"<blob>=\"/ {print $NF}' | sed 's/ \"alis\"<blob>=\"//;s/.$//'")
#CERT_BY_SHA=$(su "$currentuser" -c "security find-certificate -a -Z | grep -B 9 "MS-ORGANIZATION-ACCESS" | grep "SHA-1" | awk '{print $3}'")
#
echo "Removing keychain password items for jamfAAD"
#jamfAAD items
su "$currentuser" -c "security delete-generic-password -l 'com.jamf.management.jamfAAD'"
rm -rf /Users/"$currentuser"/Library/Saved\ Application\ State/com.jamfsoftware.selfservice.mac.savedState
rm -r /Users/"$currentuser"/Library/Cookes/com.jamf.management.jamfAAD.binarycookies
rm -rf /Users/"$currentuser"/Library/Saved\ Application\ State/com.jamf.management.jamfAAD.savedState
su "$currentuser" -c "/Library/Application\ Support/JAMF/Jamf.app/Contents/MacOS/JamfAAD.app/Contents/MacOS/JamfAAD clean"
#
echo "Removing keychain password items for Company Portal app (v2.6 and higher with new com.microsoft.CompanyPortalMac bundle ID)"
#Company Portal app items
rm -r /Users/"$currentuser"/Library/Cookies/com.microsoft.CompanyPortalMac.binarycookies
rm -rf /Users/"$currentuser"/Library/Saved\ Application\ State/com.microsoft.CompanyPortalMac.savedState
rm -r /Users/"$currentuser"/Library/Preferences/com.microsoft.CompanyPortalMac.plist
rm -r /Library/Preferences/com.microsoft.CompanyPortalMac.plist
rm -rf /Users/"$currentuser"/Library/Application\ Support/com.microsoft.CompanyPortalMac
rm -rf /Users/"$currentuser"/Library/Application\ Support/com.microsoft.CompanyPortalMac.usercontext.info
su "$currentuser" -c "security delete-generic-password -l 'com.microsoft.CompanyPortal'"
su "$currentuser" -c "security delete-generic-password -l 'com.microsoft.CompanyPortalMac'"
su "$currentuser" -c "security delete-generic-password -l 'com.microsoft.CompanyPortal.HockeySDK'"
su "$currentuser" -c "security delete-generic-password -l 'com.microsoft.adalcache'"
su "$currentuser" -c "security delete-generic-password -l 'enterpriseregistration.windows.net'"
su "$currentuser" -c "security delete-generic-password -l 'https://device.login.microsoftonline.com'"
su "$currentuser" -c "security delete-generic-password -l 'https://device.login.microsoftonline.com/' "
su "$currentuser" -c "security delete-generic-password -l 'https://enterpriseregistration.windows.net' "
su "$currentuser" -c "security delete-generic-password -l 'https://enterpriseregistration.windows.net/' "
su "$currentuser" -c "security delete-generic-password -a 'com.microsoft.workplacejoin.thumbprint' "
su "$currentuser" -c "security delete-generic-password -a 'com.microsoft.workplacejoin.registeredUserPrincipalName' "
#
echo "Removing WPJ for Device AAD ID $AAD_ID for $currentuser"
su "$currentuser" -c "security delete-identity -c $AAD_ID"
#echo "Removing WPJ for Device AAD ID $AAD_ID for $currentuser from SHA hash $CERT_BY_HASH"
#
echo "Please REBOOT this macOS device to re-load the login.keychain and re-run the Azure Registration via Self Service AFTER you ensure device removal from AAD and MEM server side."
exit 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-17-2022 12:27 AM
Hello @robertoa
I just want to clarify below that Jamf AAD prompt is something which can come and thats normal, please read below information and feel free to reach me if you need any additional resources as well.
Once the initial registration is completed jamfAAD continues to run in the background and has to authenticate every 24 hours to Azure to confirm the Azure AD record is still intact and confirm the AAD Device ID. Why? Well, because it has to report it to JPRO as proof of the integrity of the registration, and the activity of the device.
This is why we have the WPJ key and cached credentials. jamfAAD actually authenticates silently to Azure and uses the items in the keychain to do so. As long as the WPJ key is ok, the Azure AD record is intact, the device is online (to contact Azure), the cached password is valid…. all is well. jamfAAD silently authenticates, gets the Device ID, reports it to JPRO, JPRO sends inventory data to Intune… everyone happy. (Quick note: JPRO only sends an inventory update to MEM when something changed..)
However, whenever this silent authentications fails, for whatever reason, jamfAAD will go into interactive mode and prompt the end user to authenticate again! This is 100% normal and expected behaviour. Furthermore, there are other situations where Azure may even instruct jamfAAD to go in interactive mode, such as an expired MFA lifetime.
- Sam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-23-2023 12:43 PM
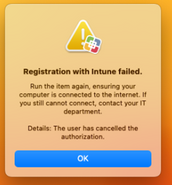
@Samstar777 that means JamfAAD is required for Jamf pro (on prem)? In my situation I able to complete the registration via company portal and then JamfAAD popup and asking for Azure Athentication though my device is showing on register complete (on endpoint) and on portal device is showing registered with azure AD. This is the error I am getting after put my Azur authentication
And then showed registration failed
In this situation what I am missing, please help me. Another thing is looks like I couldn't push conditional policy from Intune on Azure register device. Any help is appriciated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-21-2023 12:14 AM
Hey Sam!
Do we have any chance to troubleshoot, why some Devices nearly daily gets those prompts?
Without cleaning the registration?
We just started registering the Devices to Intune via JPRO and some Users are already annoyed :D
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-17-2022 10:02 AM
You might consider filing feedback or opening a ticket with Microsoft. In my testing, I have found that the entire enrollment process is cumbersome and badly worded, and I'd like better visibility and control into the timing and need for these re-enrollment prompts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-17-2022 11:15 AM
MSFT ticket was submitted the other day. They are still gathering initial info like device ID and type of enrollment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2023 02:03 AM - edited 03-01-2023 02:13 AM
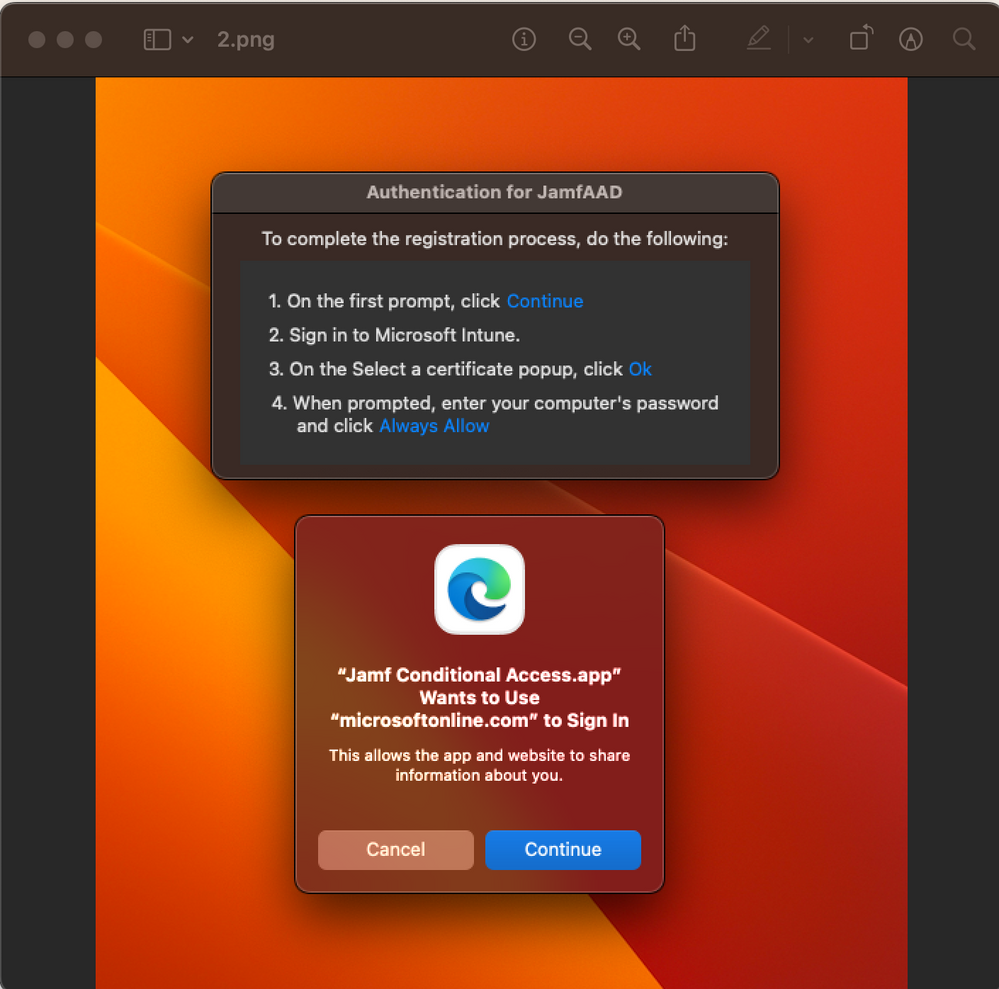
As of Jamf 10.43+ the JamfAAD app no longer exists and was replaced by "Jamf Conditional Access", which still accepts the "clean" argument and still get's the job done.
In the above script from @obi-k just replace the line
su "$currentuser" -c "/Library/Application\ Support/JAMF/Jamf.app/Contents/MacOS/JamfAAD.app/Contents/MacOS/JamfAAD clean"with
su "$currentuser" -c "/Library/Application\ Support/JAMF/Jamf.app/Contents/MacOS/Jamf\ Conditional\ Access.app/Contents/MacOS/Jamf\ Conditional\ Access clean"
And watch out for the "Cookes" typo in
rm -r /Users/"$currentuser"/Library/Cookes/com.jamf.management.jamfAAD.binarycookies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-01-2023 05:10 AM
@sakul is this part work?
AAD_ID=$(su "$currentuser" -c "security find-certificate -a -Z | grep -B 9 "MS-ORGANIZATION-ACCESS" | awk '/\"alis\"<blob>=\"/ {print $NF}' | sed 's/ \"alis\"<blob>=\"//;s/.$//'")
For me it just stuck here forever. I am on macOS Ventura
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2023 06:29 AM - edited 03-01-2023 06:30 AM
Yes it does, but since you mentioned it... get rid of the space here in the sed command:
...s/ \"alis...Also try running just the first part as the user that did the initial registration
security find-certificate -a -Z | grep -B 9 "MS-ORGANIZATION-ACCESS"You should get something like this in the output
...
attributes:
"alis"<blob>="#######-####-####-####-##########"
...
If this line is missing then you don't have a registered AAD_ID.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-01-2023 08:13 AM
Thanks @sakul, I get
attributes:
"alis"<blob>="#######-####-####-####-##########"
when Ran only
security find-certificate -a -Z | grep -B 9 "MS-ORGANIZATION-ACCESS"Which mean device register with AAD_ID but couldn't grab those. But If I run following
currentuser=`stat -f "%Su" /dev/console`
AAD_ID=$(su "$currentuser" -c "security find-certificate -a -Z | grep -B 9 "MS-ORGANIZATION-ACCESS")
echo $AAD_ID
that was running forever. Any suggestion
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-01-2023 09:39 AM
This script is meant to run as the Jamf management user. The "su" command then impersonated the currently logged in user ($currentuser).
If you execute it in terminal then you're basically trying to impersonate yourself, which is why you're getting stuck.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2023 10:39 AM - edited 03-01-2023 10:46 AM
Thanks for that clarification. I got that Alias when I set EA for AAD_ID and ran from Jamf. One more question for this line:
rm -r /Users/"$currentuser"/Library/Cookes/com.jamf.management.jamfAAD.binarycookiesI couldn't see that folder named Cookes/ cookies here: /Users/$currentuser/Lubrary
Anny suggestion on this?
And another question is what these two lines are doing if you can explain please
su "$currentuser" -c "security delete-generic-password -l 'com.jamf.management.jamfAAD'"
And
su "$currentuser" -c "/Library/Application Support/JAMF/Jamf.app/Contents/MacOS/Jamf Conditional Access.app/Contents/MacOS/Jamf Conditional Access clean"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-01-2023 11:00 AM
That folder should be "Cookies". It's just a typo in the original script.
su "$currentuser" -c means "run following command as $currentuser"
"security delete-generic-password -l 'com.jamf.management.jamfAAD'" means remove password from keychain with the label 'com.jamf.management.jamfAAD'
"Jamf Conditional Access" is an tool to manage Conditional Access
Jamf Conditional Access collects device and user Azure Active Directory ID values and reports them to the Jamf Pro server.
Usage:
Jamf Conditional Access [-verbose] <command>
Available Commands:
clean Removes the Azure AD token from the user's keychain and the user's preferences from the preferences directory
gatherAADInfo Collect AAD information and send it to Jamf Pro server; use -disable-cache-read to always connect to Azure
help Print this help message
registerWithIntune Launches Microsoft Company Portal. If user successfully registers with Intune, gatherAADInfo runs.
version Print the version of Jamf Conditional Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-21-2023 09:25 AM
HI Guys, someone an idea, why the jamf conditional access app doesnt start with the authentication after running the device registration with the company portal app. The step with the company portal app runs fine. the second step for the conditional access app doesnt work.
Explanation:
I test on 3 devices.
two of this devices are running with my user and the same setup
on one macbook the registration went fine (twice)
on the other macbook the registration stops after the company portal.
How can i check if the conditional access app is installed on a macbook and how to ensure, that the conditional access app starts after device registering with company portal app.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-24-2023 05:04 AM
Temporary some issues are found in this process.
Temporary solution is
sudo jamf manage (before starting the azure registration with company portal)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-21-2023 03:11 AM
Hi Everyone,
Has anyone been able to solve this problem somehow? Although I asked both Jamf and Microsoft about this, I could not get a satisfactory answer or solution. Especially the Microsoft side is having a hard time understanding the problem. Is the main source of this problem Jamf Pro? Is it wrong for me to ask the Microsoft side a question? If anyone has found a solution can you please help me? I had to suspend a huge project right now. This pop-up is very annoying.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-21-2023 05:47 AM
For me this problem has been resolved. To resolve that we had to make chrome default with a profile and also we make a change in MS Azure for Jamf App like gave permission to access MS Azure from Jamf.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-21-2023 05:58 AM
In our environment, Chrome is already used as the default browser. However, I can say that I do not fully understand the situation in the other sentence you said. I mean the following sentence.
"we make a change in MS Azure for Jamf App like gave permission to access MS Azure from Jamf."
Can you elaborate a little more on what exactly you do here? Because of this problem, our administrators may decide to completely remove Jamf Pro from the environment. So I urgently need a permanent solution. I would be very grateful if you could help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-21-2023 06:35 AM
You have to follow this document: https://learn.microsoft.com/en-us/mem/intune/protect/conditional-access-integrate-jamf and work with Azure AD for "Create an application in Azure Active Directory" from steps 1 through 16. Here step # 6 to Step # 11 is the part i was talking about. Here your Azure Admin needs to give permission to access Jamf API to access MS Azure AD to avoid that pop-up. I hope I able to make you understand.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-21-2023 07:02 AM
Hi,
Actually, I remember doing these steps. Is the following field configured in your environment? I didn't do that. Because it has been said that this feature will be discontinued. I only did it by configuring the Device Compliance part.