- Jamf Nation Community
- Products
- Jamf Pro
- KRACK Wi-Fi Vulnerability
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
KRACK Wi-Fi Vulnerability
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-16-2017 01:05 PM
Does anyone know if there was a patch released or when it is expected to be released? Guessing this is a firmware update?
https://www.macrumors.com/2017/10/16/krack-wifi-vulnerabilities-patched-apple-ios-macos/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-16-2017 01:27 PM
I believe KRACK fixes are were seeded in the beta channels for all apple os's.
macrumors
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-16-2017 01:32 PM
What about 10.10/10.11/10.12 clients?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-16-2017 01:36 PM
@rqomsiya We're all waiting for that info from Apple like you are.
There is precendent for them only fixing the shipping OS... the only patch for the Broadpwn vulnerability was in 10.12.6.
Of the 10 CVE's, 9 require client-side patching. Of every device. sigh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-16-2017 01:52 PM
They have to patch this for 10.12.6 with a supplemental. I'd be surprised if they didn't patch 10.11 as well. This is too widespread.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-16-2017 02:38 PM
I'd like to think you're right @alexjdale , but their track record leaves me worried.... we're not ready to upgrade to 10.13 yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-16-2017 06:58 PM
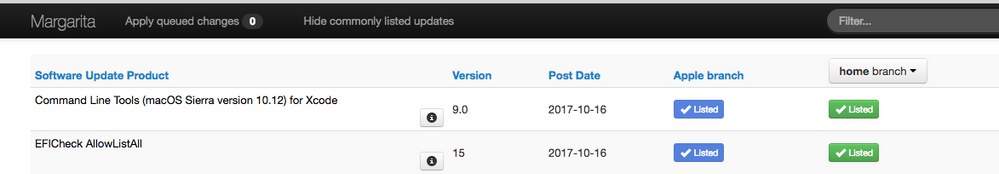
New update release a few hours ago. Might be a step in the right direction
EFICheck AllowListAll
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2017 09:29 AM
To be of any use to an attacker, both the WPA2 device and the connected client need to remain vulnerable to KRACK.
While it doesn't diminish the pressing need to patch the Macs and iOS devices, updating your WAPs will help. Ubiquiti, for example, released updates yesterday for their various UAPs. (UCK controller firmware 5.6.19 is also live.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2017 09:51 AM
@pete_c is right. According to discoverer Mathy Vanhoef, updates should occur on APs and on clients, but just APs will help your network, at least.
... luckily implementations can be patched in a backwards-compatible manner. This means a patched client can still communicate with an unpatched access point (AP), and vice versa. In other words, a patched client or access point sends exactly the same handshake messages as before, and at exactly the same moment in time. However, the security updates will assure a key is only installed once, preventing our attack. So again, update all your devices once security updates are available. Finally, although an unpatched client can still connect to a patched AP, and vice versa, both the client and AP must be patched to defend against all attacks!
https://www.krackattacks.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-18-2017 11:11 AM
So it's possible I just missed it, but, does anyone know if Apple has released a patch for Sierra to fix this vuln yet? In doing searches I'm not pulling anything up.
Or is so far the only statement from them, that, sure, if you are running our latest buggy new OS, you're fine, otherwise, you are SOL? I seriously hope they don't leave 10.12.x Macs out to dry just because 10.13 is out now. I'm getting asked how soon we can get a patch for this deployed, but we cannot go to High Sierra in our environment yet due to dependencies and the fact that it's not quite ready for prime time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-18-2017 11:25 AM
Hey Mike, from the latest I read they have a patch in beta for Sierra et al with good results so far . If history is an indication, they'll probably roll it out with 10.13.1 as a security patch for 10.12,10.11 and (maybe?)10.10, like they did for 10.12.6
we'll see
Larry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-19-2017 01:54 PM
Highly doubt 10.10 sees any updates. 10.11 and 10.12 will be lucky if they get this one. There is a new Security Update beta for Sierra floating around...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-01-2017 12:12 AM
https://support.apple.com/en-us/HT208221
Sync and check your SUS server.