- Jamf Nation Community
- Products
- Jamf Pro
- Locking out a Macbook if it is ever stolen? any id...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-17-2016 05:41 PM
Hi all,
I'm searching through Casper JSS for anything that could lock out a Macbook from users. I'm not trying to do anything malicious here (well, that depends on how honest you think I am ;) ). But I'm the Mac admin for about 600 Macbooks. If an employee ever takes the Macbook out of he company, I want to get control of it again. The Macbook is company property.
I am thinking chaning the user's password on a Macbook? Or even something severe like deleting the user's folder? (I think that's too much as it means we can't recover the data)
Solved! Go to Solution.
- Labels:
-
Jamf Pro
-
Usage Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2016 02:30 AM
In Casper Suite go to 'Computers'
Search for the machine in question
Click on it
Go to the 'Management' tab
Click on LOCK COMPUTER
Enter a 6 digit code
The machine will then reboot, lock itself, and then won't unlock again without the code you chose
You do need to bear in mind of course that the machine will then be offline and untraceable (until such time as it's reactivated with the 6 digit pin) which you may (or may not) want
It'd also make sense to create a configuration profile with a login window payload with your organisations' ownership details and roll it out to the machine. You could even send the user a message that way!
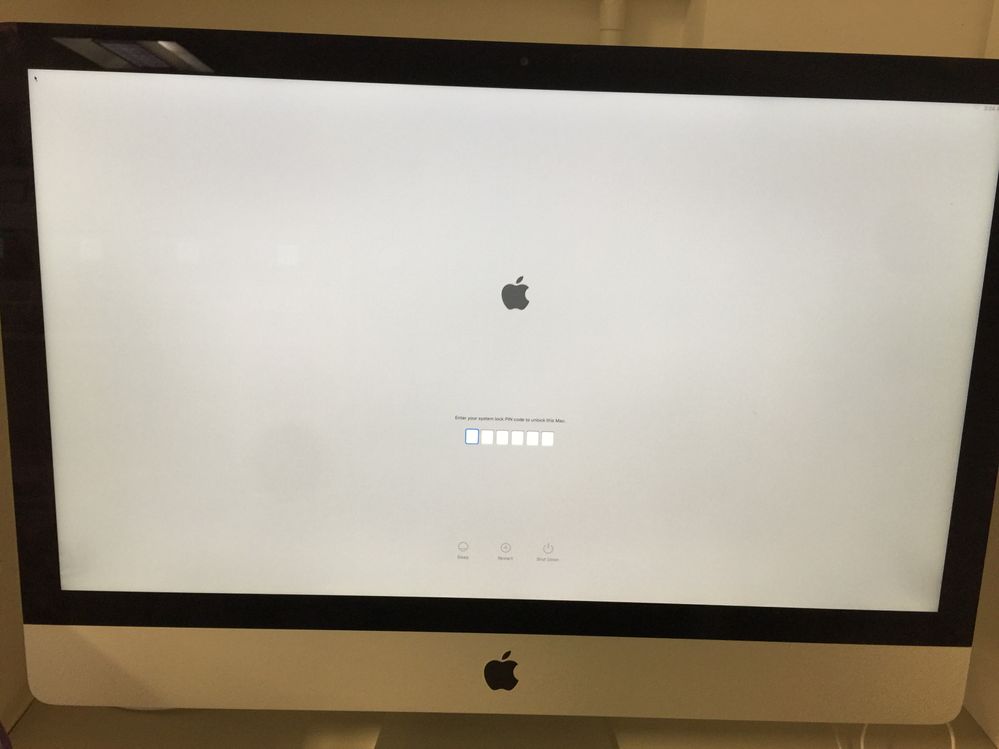
The login window text only appears on the normal login screen though. The lock screen looks like the picture below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-17-2016 06:28 PM
If you have Apple Push Notification setup in the JSS you can send a remote lock or even a remote wipe. To bypass the lock you have to have the five-digit code used when the command was pushed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-17-2016 10:16 PM
I do have the push certficate and I have Computer Management > Security > Enable Push Notification = checked.
But where would I be able to send a remote lock policy over?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2016 02:30 AM
In Casper Suite go to 'Computers'
Search for the machine in question
Click on it
Go to the 'Management' tab
Click on LOCK COMPUTER
Enter a 6 digit code
The machine will then reboot, lock itself, and then won't unlock again without the code you chose
You do need to bear in mind of course that the machine will then be offline and untraceable (until such time as it's reactivated with the 6 digit pin) which you may (or may not) want
It'd also make sense to create a configuration profile with a login window payload with your organisations' ownership details and roll it out to the machine. You could even send the user a message that way!
The login window text only appears on the normal login screen though. The lock screen looks like the picture below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2016 05:56 AM
I guess that will not work if the JSS server is not reachable from outside?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2016 08:15 AM
I believe it would work as the lock command comes from Apple. That said, you can always just erase the computer. They don't have activation lock like iOS devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2016 01:35 PM
You could couple the ideas posted here with an IP geolocation EA to try and locate the computer if the person is not responding to requests. Even a fullscreen jamfhelper message with text like "This computer has encountered an error. Please call "company name" at "company IT phone number" for assistance. I have recovered stolen laptops using tools like this. I think it depends on which direction you want to go. I always try recovering the equipment first because I would prefer to have the computer back. A remote lock or wipe may prompt the user to toss it. Of course, your JSS has to be reachable from the outside for what I am describing to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2016 01:50 PM
All of the remote lock options, or really any functionality pushed via a management suite, whether coming via a policy or Apples MDM commands do require that the client device can reach the JSS to get the actual command, so the JSS would have to be externally accessible.
Everything via the JSS is client initiated communication (not counting Casper Remote but it still requires access to the JSS). All of Apples push notification functionalities in the MDM framework work via the following process; an MDM server sends a command to Apple to tell a device to check in to their mdm server, when said device has network access and can reach Apples servers they are then told to check into the MDM server they are enrolled to for work to be done, once the device connects back to the MDM server it will receive the command/profile/etc.
Nothing about which command or type of configuration profile or its payloads is actually sent to Apple to be sent directly to the devices, we just tell Apple to tell the device to check in to their MDM server as is defined in their MDM profile.
The only slight exception to this rule is some data is sent to Apple in regards to DEP Prestage enrollment information but thats because settings are defined prior to actual MDM enrollment and management.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2016 03:44 PM
Great answers everyone.
I remember from CCT course the lock computer was shown. I just didn't remember where it was.
Now for me to do a few rounds of testing to see how it goes within our company.
Thanks again :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-19-2016 04:06 AM
Just one thing to add here (a little sneaky but since your post title mentioned MacBooks being stolen..) is that you can also utilise the JSS and have it retrospectively install and activate Prey on a stolen MacBook (assuming it is still talking to your JSS).
For example you can cache the Prey installer in an obscure location and leave it dormant. Using either extension attributes or even smart group criteria (based on IP Address range for example) you can run a very simple script (see here that installs and activates the client so that you can collect screenshots and pics every few minutes.
The advantage this way is you only track devices if needed in the event of a device being stolen. Of course this is something you need to build a very specific and strict policy around to protect your user's privacy (this is another big discussion) but this is far a more thorough solution for lost/stolen devices than simply sending an erase MDM command.