- Jamf Nation Community
- Products
- Jamf Pro
- Re: Mac Sierra 802.1x wireless before login
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Mac Sierra 802.1x wireless before login
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2017 09:06 AM
We are looking at moving from WPA-Personal PSK to WPA-Enterprise 802.1x. We have over 1000 Macbooks, running Sierra, Windows 2012 R2, Windows NPS for Radius and a test AP configured for 802.1x. I have setup NPS, created a JAMF profile and pushed it to a test Mac. Once the profile, with certs, is on the machine I can go into settings, network and click 802.1x connect button and it works.
When I log out, or restart, there is no network till I log into the local account. Once logged in, the 802.1x network comes up and I have connectivity.
Can anyone help me! I have scoured the internet and all answers are useless for getting this done.
- Labels:
-
Jamf Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2017 09:19 AM
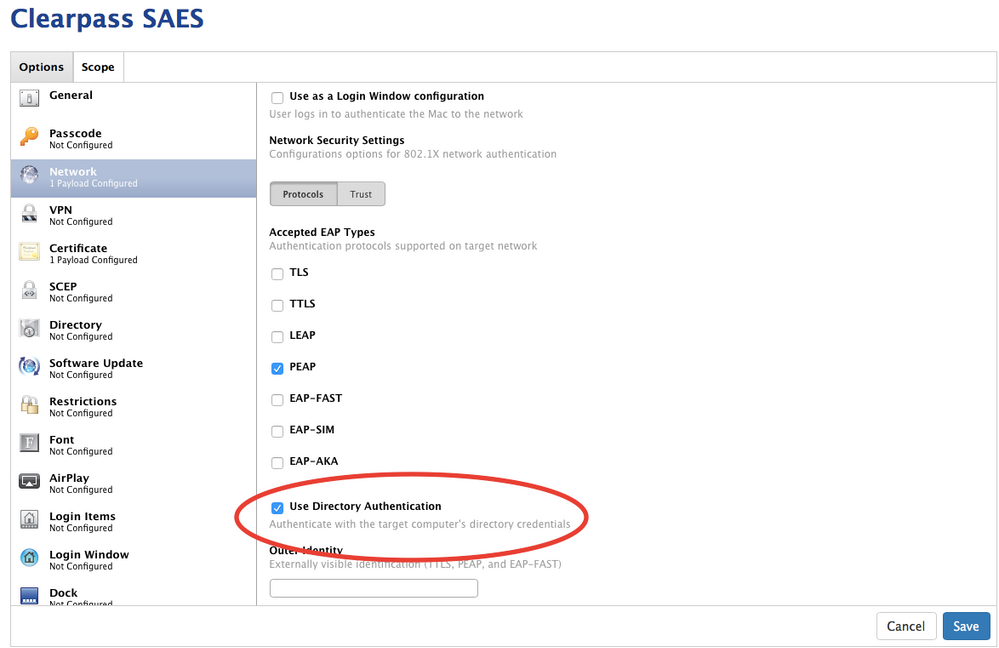
Did you enable "Use Directory Authentication"? That way the machine connects at the machine level and at the login window.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2017 10:04 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2017 11:46 AM
Our macbooks are bound to the AD. While using WPA-Personal, the Macbooks would have network at login. When we test 802.1x, there is no network at login.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2017 12:02 PM
Where is "Use Directory Authentication"? I see "Use as a Login Window configuration" in the Network Payload.
Many thanks for the help... my keyboard has an imprint of my head where I have beat it against it so much :-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2017 12:11 PM
It depends on your infrastructure, but we have this working in Sierra with the following settings using Cisco wireless:
In the Network WiFi Payload we use these settings:
-AutoJoin – Yes
-Hidden Network – Yes
-Security Type – WPA2 Enterprise
-Use as a Login Window Configuration – Yes
-Use Directory Authentication - Yes
Then we create an AD "User" that this profile connects to (with a PW that never changes). We isolate these down to rooms, but you could set these accounts up in a way that works for you. Macs don't support genuine AD 802.1x "computer" accounts in the same way that Windows does, creating this hurdle when you're first setting it up.
There could be a way to set this up with certificate-based authentication that doesn't use the method above, but I haven't tested that approach yet. Mine likely isn't very scalable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2017 12:12 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2017 12:29 PM
Found it! The issue was in the Network Payload. We are using 802.1x TTL and did not have the "Identity Certificate" dropdown set to a value. Changed that to our AD certificate and "Robert is your moms brother"!
Thank you all for your input.