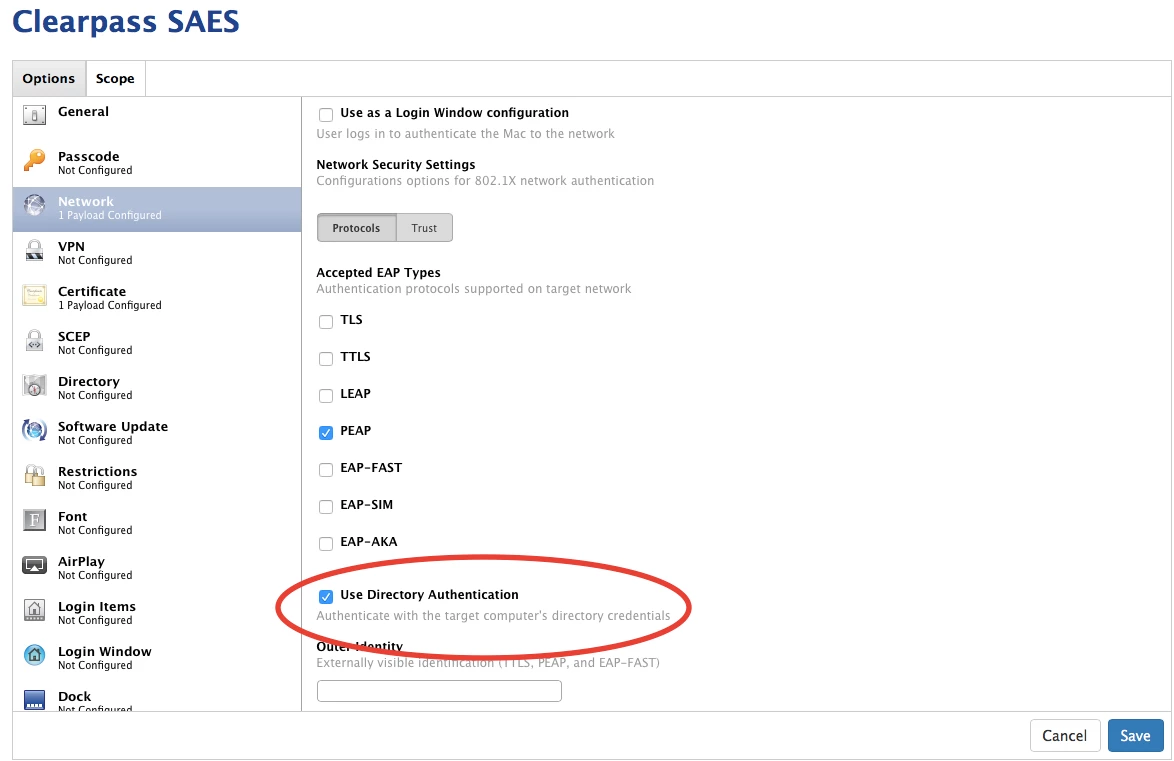
We are looking at moving from WPA-Personal PSK to WPA-Enterprise 802.1x. We have over 1000 Macbooks, running Sierra, Windows 2012 R2, Windows NPS for Radius and a test AP configured for 802.1x. I have setup NPS, created a JAMF profile and pushed it to a test Mac. Once the profile, with certs, is on the machine I can go into settings, network and click 802.1x connect button and it works.
When I log out, or restart, there is no network till I log into the local account. Once logged in, the 802.1x network comes up and I have connectivity.
Can anyone help me! I have scoured the internet and all answers are useless for getting this done.