- Jamf Nation Community
- Products
- Jamf Pro
- Re: Macbooks fall of AD domain
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Macbooks fall of AD domain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2020 06:41 AM
During the school year, we have teacher MacBooks that fall of the domain, so we have to manually go to the teacher unbind it and join them again, has anyone found a fix for this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2020 06:55 AM
I do not have a solution for your issue, but we experienced the same issues. If you are able to, I suggest utilizing NoMAD & NoMAD Login instead of binding your Macs.
I moved all macs in my environment off of AD & moved to NoMAD & NoMAD Login. The Support Team I work with that were dealing with the bound Macs are very very happy now.
Looking for a Jamf Managed Service Provider? Look no further than Rocketman
________________
Virtual MacAdmins Monthly Meetup - First Friday, Every Month
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2020 07:21 AM
What are you setting your computer object password change interval to? I think the default is 14 days which can cause some issues if machines don't get used on your network for a couple of weeks. You might try something longer like 90 days.
dsconfigad -passinterval 90
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2020 10:54 AM
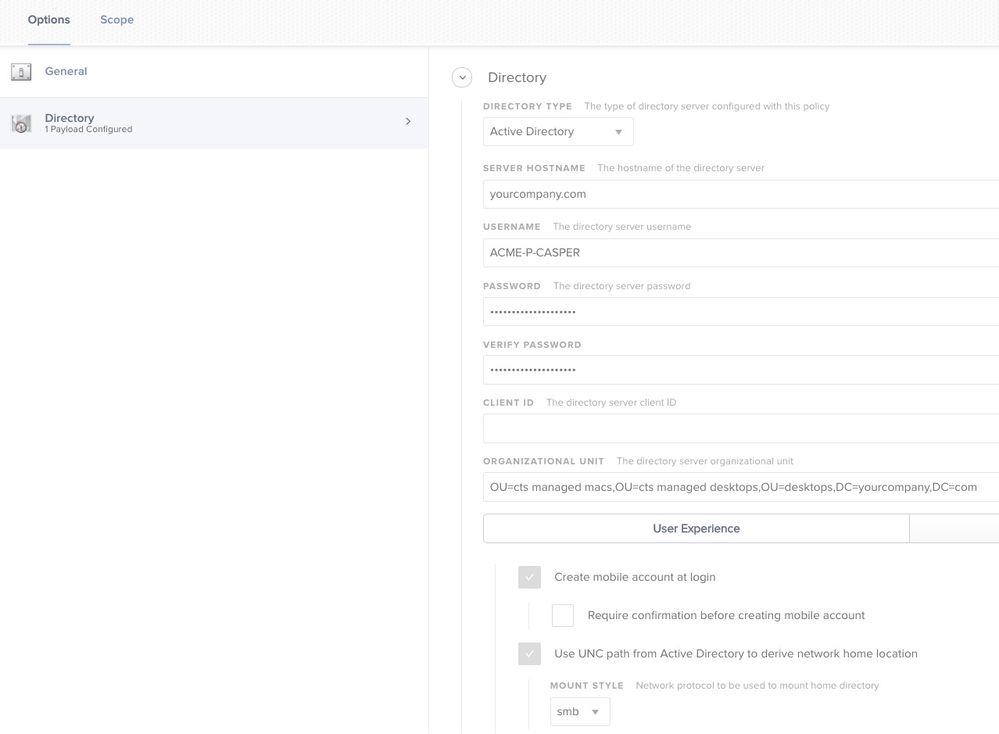
you can try using a configuration profile also, that's what we are using now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2020 10:58 AM
@jconte what do you have to config profile doing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2020 11:39 AM
binding the Mac to AD
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2020 12:00 PM
Also check with your AD admins - they might have a policy to suspend or remove stale computer records causing this...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2020 12:01 PM
Like user accounts, computer accounts in Active Directory (AD) authenticate with passwords and those passwords will expire. By default, this is every 30 days. Quite often over the summer, teacher laptops bound to AD go offline (go home) for months at a time and fail to communicate when they return to begin the next school year. Or some teachers simply don't use their laptops on the correct Wi-Fi network or at all.
Consult with your Active Directory administrators to learn what they have set for Domain member: Maximum machine account password age. Maybe they can adjust that or maybe you can encourage users to connect their Macs to your network on a periodic basis.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2020 01:08 PM
I ran into this at my last org.
On the computer assigned to me I set the interval to 0 so that the computer would pull in a new key daily as well as NoMad.
NoMad solved most of my issues where the web filter still worked fine and I was working with a local account.
There, Windows clients also sometimes run into the same problem and I suspect a replication between DCs is set for too long.
I've heard from my replacement that they ran into problems with iMac devices and had to rebind again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2020 03:42 PM
If you are creating mobile accounts, they should be able to log back into their machines even when it's not bound to AD anymore. If it's still communicating with your JamfPro, Create a smart group "Clients not bound" with criteria "Active Directory Status" operator "is not" then the value "your.domain". Run a rebind script scoped to this smart group, ongoing, recurring check-in, update inventory.
#!/bin/bash
# Rebind/Bind to AD Script
computerid=`/usr/sbin/scutil --get ComputerName`
domain="school.org"
udn="admin"
password="password"
ou="OU=Domain Computers,DC=school,DC=org"
alldomains="disable"
localhome="disable"
protocol="smb"
mobile="enable"
mobileconfirm="disable"
useuncpath="disable"
user_shell="/bin/bash"
preferred="-preferred dc.school.org"
admingroups="District IT,District Staff,District Teachers"
# Activate the AD plugin
defaults write /Library/Preferences/DirectoryService/DirectoryService "Active Directory" "Active"
plutil -convert xml1 /Library/Preferences/DirectoryService/DirectoryService.plist
sleep 5
#Unbinding to AD
echo "Unbinding computer from Active Directory..."
dsconfigad -f -r -u $udn -p $password
rm -f /Library/Preferences/edu.mit.Kerberos 2>&1
# Bind to AD
echo "Binding to Active Directory..."
dsconfigad -f -a $computerid -domain $domain -u $udn -p "$password" -ou "$ou"
# Configure advanced AD plugin options
if [ "$admingroups" = "" ]; then
dsconfigad -nogroups
else
dsconfigad -groups "$admingroups"
fi
dsconfigad -alldomains $alldomains -localhome $localhome -protocol $protocol
-mobile $mobile -mobileconfirm $mobileconfirm -useuncpath $useuncpath
-shell $user_shell $preferred
# Restart DirectoryService (necessary to reload AD plugin activation settings)
killall DirectoryService
# Add the AD node to the search path
if [ "$alldomains" = "enable" ]; then
csp="/Active Directory/All Domains"
else
csp="/Active Directory/$domain"
fi
exit 0
fi
echo "Killing DirectoryService daemon..."
killall opendirectoryd
if [ "_${SUCCESS}" = "_YES" ]
then
echo "Finished."
exit 1
fiI haven't tested this on Catalina. But for binding purposes, it should work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2020 07:49 AM
With the work from home thing going on and no guarantee that teachers will connect their systems to the campus via vpn, does anyone have the straight info on this?
Above I read someone saying to use dsconfigad -passinterval to fix it by changing the interval and then another says it needs changed on the windows server side. Back in my windows days that meant a group policy change but I've never had to look into this on the Mac side. Do Macs actually read that group policy setting and act on it in the same way?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2020 08:32 AM
@jhuls It's not GP that sets that. I don't think there is a default domain policy for setting a machine password change requirement. But machines will "drop off" if they don't contact the domain in a certain amount of time.
Setting the -passinterval to 0 will prevent the Mac from rotating it's machine password, and would need to be set before binding. It won't work if you run that after.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2020 08:56 AM
@patgmac "Domain member: Maximum machine account password age"...unless I'm mistaken that does exactly what I was referring to in terms of changing the interval via group policy. There is also one that can disable.
So, if that does what I believe it does, I'm trying to learn if it can affect Macs? I read the post above by @talkingmoose that it does affect Macs but others here, including you, are saying passinterval is the answer. The last thing I want to do is implement one and it fail or ask our application support people to make a change to a setting that would impact our Windows users when they're saying that they don't have the issue of machines dropping off the domain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 10:43 AM
I don't believe I had that setting set in my domain, but it sounds like it would be what is causing the drop from the domain. What is the max age set to?
One thing I used to do (back when I used binding) was use an EA to check if the machine was still bound. Then based on that, I would re-bind when needed.
#!/bin/bash
#
# This script will check if the AD bind is in fact, working.
#
# Written by Patrick Gallagher
# Updated: 01/17/2017
domain=ad.company.com
netbiosDomain=AD
OSvers=$( sw_vers -productVersion | cut -d. -f2 )
nc -z ${domain} 636 > /dev/null 2>&1
reachable=$?
if [[ $reachable = "0" ]]; then
## Mac is on the network, continue
if [[ $(dsconfigad -show | awk '/Active Directory Domain/{ print $NF }') == "${domain}" ]]; then
ADCompName=$(dsconfigad -show | awk '/Computer Account/{ print $NF }')
## Mac has correct dsconfigad info, continue
if [[ "$OSvers" -ge "7" ]]; then
security find-generic-password -l "/Active Directory/${netbiosDomain}" | grep "Active Directory" > /dev/null 2>&1
if [ "$?" == "0" ]; then
## AD keychain file exists, continue
dscl "/Active Directory/${netbiosDomain}/All Domains" read /Computers/"${ADCompName}" | grep -i "${ADCompName}" > /dev/null 2>&1
if [ "$?" == "0" ]; then
## Successful lookup of computer record. AD communication is working
res="Yes"
else
res="No - AD Lookup Failed"
fi
else
res="No - AD Keychain Not Found"
fi
else
res="OS too old"
fi
else
res="No - Binding Broken"
fi
else
## Mac is not on the network or has no network connection
res="Remote"
fi
echo "<result>$res</result>"- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 11:49 AM
I inquired about this with my Apple SE and he confirmed that the group policy does not influence Macs and that the passinterval setting should be adjusted.
@patgmac Thanks for the script. I'll check it out. I don't know as much about Macs relationship to AD as I'd like so at the risk of sounding like a dumb question, does that script need to be run when the Mac is connected to the network that the AD domain resides? It would be nice to have a way to detect a potential trust issue before systems return to campus so I know what to expect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 01:24 PM
That's an EA, so it'll run every time the machine updates inventory. If it can't reach the domain, it'll return "Remote". If your machines won't be using VPN at all during WFH time, then this might not help much until they return.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 01:31 PM
Thanks. The EA part and what results to jamf I got. I wasn't sure if it was somehow detecting if there was a trust issue before reconnecting on campus or via vpn. Based on your last message it sounds like it would need to connect.
I appreciate the script. I already have it in operation and will certainly be useful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 02:43 PM
the key to keeping Macs from dropping off the domain:
1. have a system based connection to wifi, this way the laptop will have network access at the login screen - we use EAP-TLS with a computer certificate delivered by SCEP
2. dsconfigad -passinterval 0 - this sets it so the Mac never tries to change its computer object password with AD (respectively AD is set to never need a computer object password change)