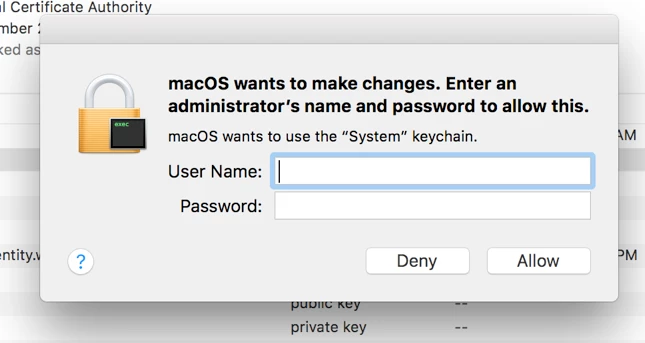
Testing out GlobalProtect for our Mac users and running into this keychain issue. We are using a local Certificate for authentication but the machine wants to use the system keychain every time GP tries to connect. The goal is to have the users never have to authenticate or enter a password after the local cert is installed.
I have already amended the ACL to include the GP app but the keychain still wants to be accessed. I am also using an administrator account, but still am prompted. If I manually unlock the System keychain from the keychain menu I am still prompted when I try and connect.
Thank you for any help or tips someone may have.