I am trying to follow along on John Kitzmiller's blog about making file vault 2 mandatory. I want to ensure the things he details in this blog post. The main thing I want to accomplish here is that a user cannot defer FileVault 2 configuration since they may be like me and not reboot until a required reboot due to an update.
I am running into some questions that I have not been able to answer for myself. And go figure, my firewall team entered a block on APNs a couple days before I had @talkingmoose on the phone. Had no idea until we hit that issue.
John K talks about applying a config profile during enrollment and running a script containing: kill -9 pgrep loginwindow. I am not sure where to put that. He also mentions during enrollment. While most of my Mac's will be DEP and pre-staged, I have some that will not be able to do that since they are not in DEP. My test machine is one such animal, VM's as well, but anyhow.
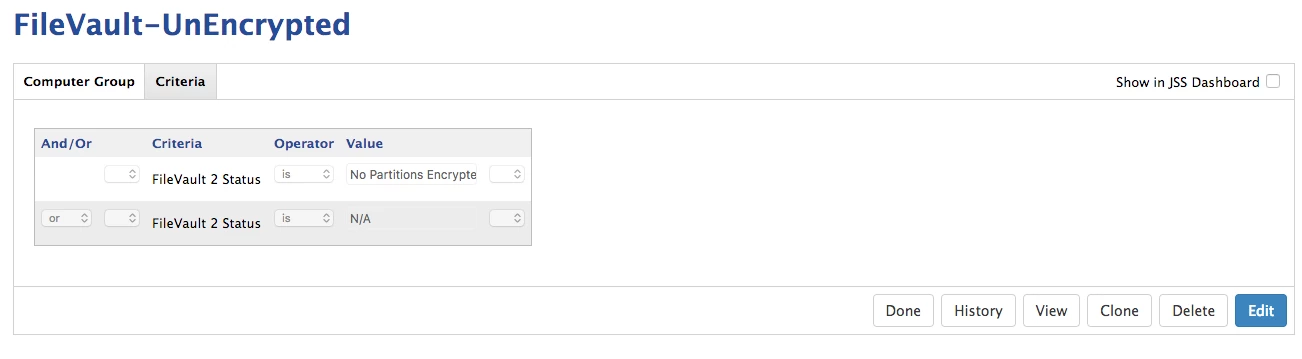
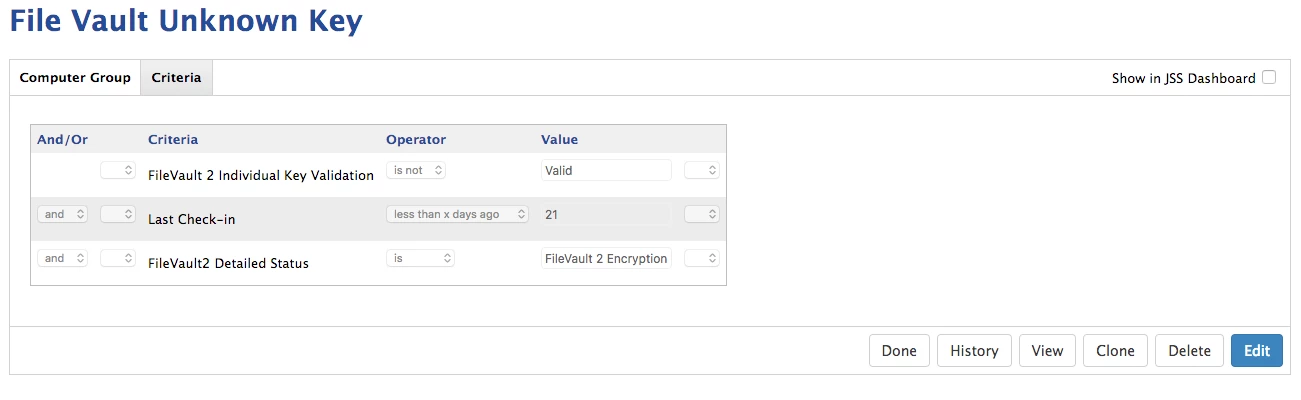
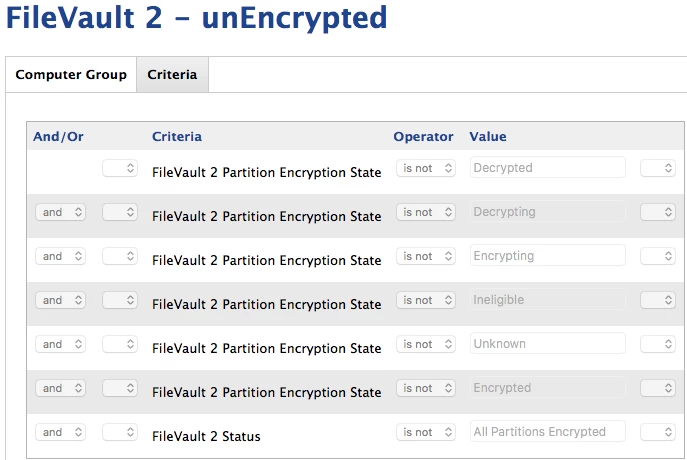
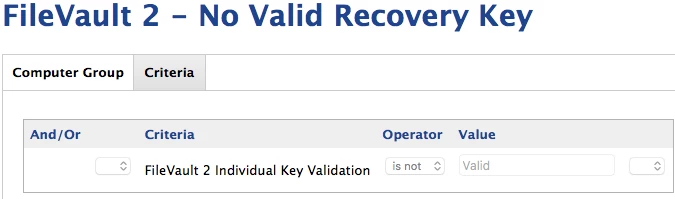
I have created what I think are all the right smart groups. My only question with the smart groups is whether I have the right criteria for checking FV2.
Has anyone followed this procedure have any advice? I am sure I can plow through it but if someone has any bits of info, that would be great.