- Jamf Nation Community
- Products
- Jamf Pro
- Re: Microsoft Defender - Privacy Preferences Polic...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Microsoft Defender - Privacy Preferences Policy Control in macOS 10.15
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-05-2020 11:07 AM
Microsoft has a really nice "deploy with JAMF" document on their Defender page. Which includes a section for configuring the PPPC for Defender in 10.15 Catalina.
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/mac-install-with-jamf
And it doesn't quite work. The approve extension is working, but Defender doesn't have Full Disk access unless we check it manually in Security prefs. Anyone else using Defender and started to deploy to Catalina? Any help is appreciated, thanks!
- Labels:
-
Configuration Profiles
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-05-2020 12:53 PM
just wanted to chime in that the Microsoft documentation for EMS Mac is awful. InTune documentation has features that do not exist for example, so I am not surprised that this doesn't work correctly. I dread the day someone working on our Microsoft stack gets the bright idea that we should deploy ATP to Macs...
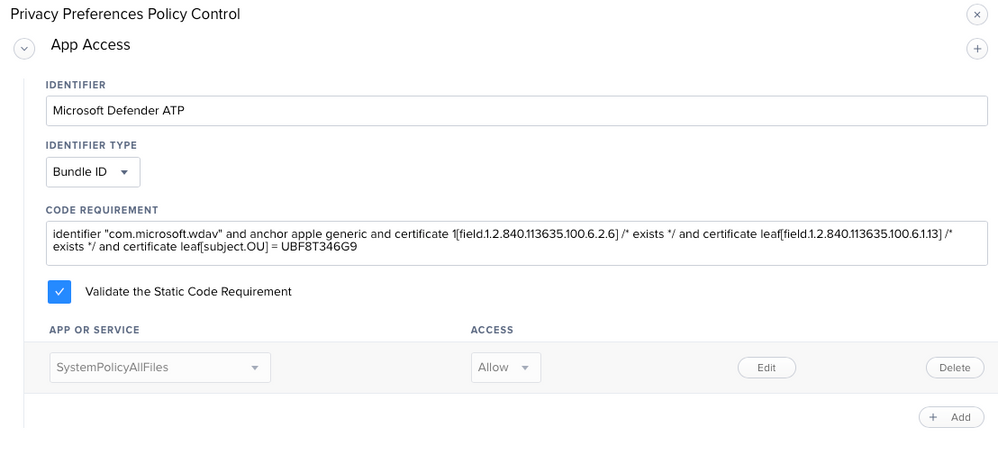
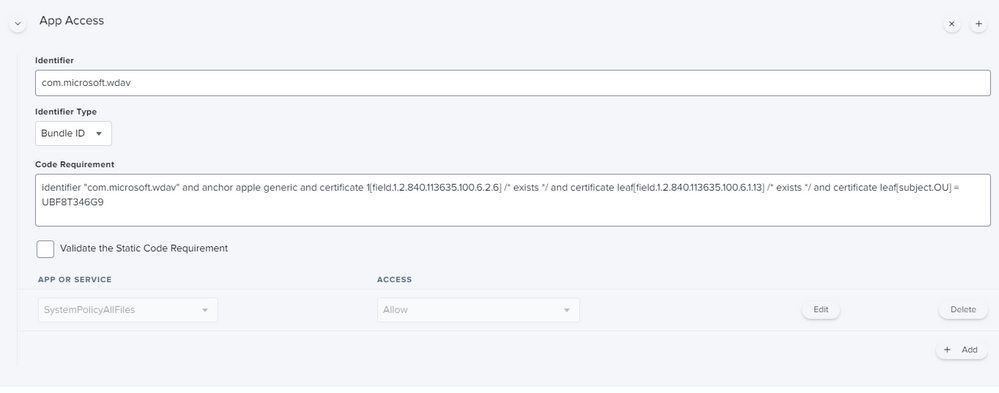
that being said, your identifier is not a valid bundle ID, but you are specifying to tie to a bundle ID. the ATP documentation says to use "com.microsoft.wdav" : https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/mac-install-with-jamf
Also word of warning on the same page
macOS 10.15 (Catalina) contains new security and privacy enhancements. Beginning with this version, by default, applications are not able to access certain locations on disk (such as Documents, Downloads, Desktop, etc.) without explicit consent. In the absence of this consent, Microsoft Defender ATP is not able to fully protect your device.
sounds like they might still not have it fully working with Catalina yet...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-07-2020 03:30 PM
Yes, I read similar posts with the same issue and Sophos, so it sounds like the PPPC settings still need some additional cooking. Thanks for the reply!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2020 07:34 AM
Does anyone have any news about this? I'm still trying to make it work but no luck..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2020 12:24 AM
I'm in test for Microsoft Defender and am seeing some machines obey the full disk access Configuration Profile and some not seeming to know it's there. These are all machines on Catalina (10.15.x)
The info I used for the Full Disk Access configuration profile was from here https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/mac-jamfpro-policies#step-6-grant-full-disk-access-to-microsoft-defender-atp and the two payloads are in it.
Late last year I had the same sort of issues with Sophos and Catalina that people seem to be mentioning and this is their notice about it. https://community.sophos.com/intercept-x-endpoint/f/discussions/116336/sophos-notification-advisory-full-disk-access-required-message-displays-on-catalina-when-using-an-mdm-solution-with-the-correct-access The fact that Sophos said it would be corrected in a version of the software made me think that they had a problem in their code.
I've been helped to get a support ticket running with Microsoft and have also pointed out that there are others having this problem.
I remember that with Sophos I made an extra Full Disk Access Configuration Profile and that it fixed some machines so potentially it tickled something. I tried the same thing with Defender but no joy. I also tried unscoping the problem machines and then rescoping but that made no difference.
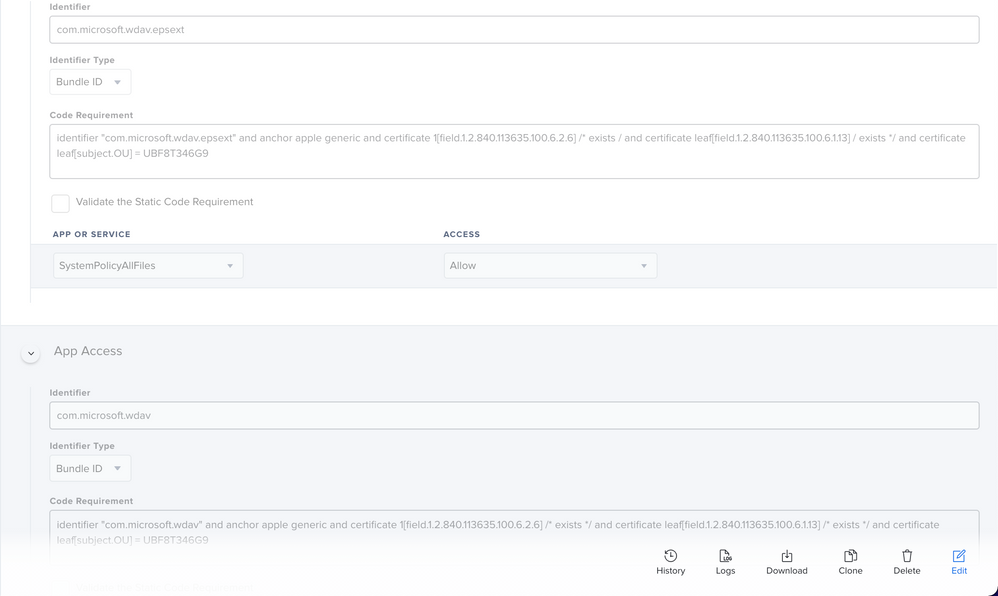
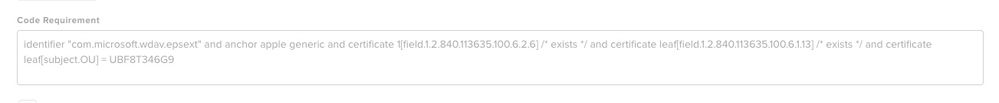
Some machines did start thinking they had full disk access when I realised I had missed the full disk access for com.microsoft.wdav.epsext (EDR) and added that. It wasn't the complete solution though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-18-2021 10:33 AM
Yes, same PPPC issue here with Defender. Originally thought the MS instructions were great and especially the new profile provided but then quickly found out it didn't work :(. After some trial and error I used the privacy settings from the older setup instructions and adjusted the newer profile: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/mac-jamfpro-policies Go to the: MDATP MDAV - grant Full Disk Access to EDR and AV
Edited my profile with those two and pushed. Defender goes to "No Action Needed" right away. Testing on a clean install now (11.2). I also found a script out there (rtrouton?) that suppresses the MAU agreement that worked better than the profile. Getting closer but not quite perfect (at least in 11.2). Hope that helps!
EDIT: mosermat is correct, the boxes aren't checked :(. One more piece missing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2021 11:51 AM
@peterrolz I'm deploying the exact same config profile you have pictured but the client machine (MacBook on MacOS 11.2) doesn't actually check the boxes for Full Disk Access. For reference, Step 7 here is what's needed for a successful setup. If I go to Microsoft Defender Security Center and find the machine, it's not logging device data. If I go back to the MacBook and check the boxes for Full Disk Access for Microsoft ATP and the Security Extension, go back to Microsoft Defender Security Center, I immediately get data. This tells me all the other configs are good except these 2 check boxes for Full disk Access.
I've also tried to accomplish this manually by using the PPPC utility and dropping Microsoft Defender ATP in...still no bueno.
I'm opening a support ticket with Microsoft to see if I can get an answer. If I do I'll try to remember to update here. If you have any advice please let me know as well? Thanks-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-03-2021 11:35 AM
@mosermat any luck with Microsoft? We are having the same issue and about to open a ticket too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2021 03:52 PM
I was having the same issue. I went and got the intune XML file for defender and looked at what was in it.
I think the MS article has a typo. I changed this in my PPC policy. The MS article seems to be missing a * after exists
Not sure if this is the same issue you have but it fixed it for me
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-05-2021 03:18 PM
Thanks @kphinney but I already had the asterisk. Must have been from older instructions as the current ones are missing - Current instructions:
/ exists / and certificate leaf[field.1.2.840.113635.100.6.1.13] / exists /
I have:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-26-2021 08:24 AM
Has anyone been able to get this fixed yet? Having the same problem now. Confirmed the check box is not granting full disk access.
Code looks the same as everyone else here, 2 App Access created following the MS documentation, which appears to have been updated 3 days ago.
anything else i can try?