- Jamf Nation Community
- Products
- Jamf Pro
- Need some assistance with ESET EA plists for Full ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Need some assistance with ESET EA plists for Full Disk access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-20-2023 03:19 AM
Based on the downloadable .plist for Full Disk Access from https://help.eset.com/eea_mac/7/en-US/install_remote_pre-installation.html
The issue that I can't upload them to jamf as it has 4 different Preference Domain inside. So I'd like to split it between 4 preferences domains:
com.eset.app.Uninstaller; com.eset.devices; com.eset.eea.g2; com.eset.endpoint
But looks like I'm making syntax mistakes and can find them.
Tried with the example from https://developer.apple.com/documentation/devicemanagement/privacypreferencespolicycontrol
So my plists are almost the same, the difference if only in Identifier value and CodeRequirement value took from the shared plist:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC “-//Apple//DTD PLIST 1.0//EN" “http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>Services</key>
<dict>
<key>SystemPolicyAllFiles</key>
<array>
<dict>
<key>Identifier</key>
<string>com.eset.eea.g2</string>
<key>IdentifierType</key>
<string>bundleID</string>
<key>CodeRequirement</key>
<string>identifier "com.eset.eea.g2" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = P8DQRXPVLP</string>
<key>Allowed</key>
<true/>
<key>Comment</key>
<string>Allows ESET to scan all files for potential threats</string>
</dict>
</array>
</dict>
</dict>
</array>
</dict>
</plist>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2023 05:57 AM
JAMF could do fine with uploading the .mobileconfig from the vendor. Multiply payloads dont mess JAMF up unless .mobileconfig has a payload JAMF does not support, then you can usually just sign the .mobileconfig so JAMF does not screw with it.
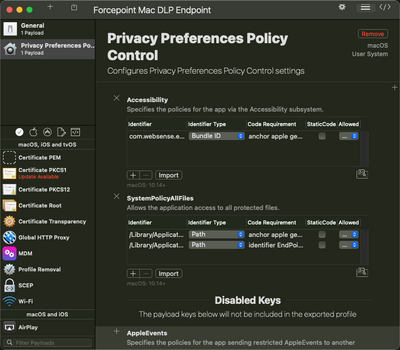
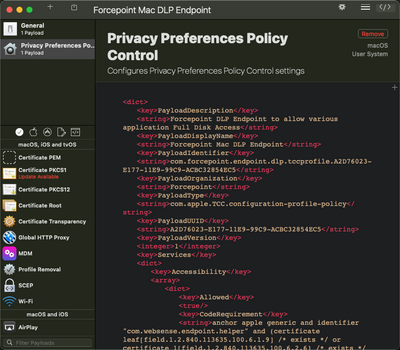
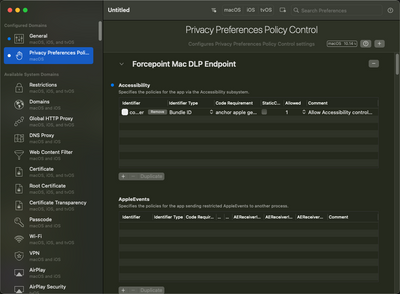
Your XML is missing a few things. It would probably be easier to do this in JAMF. You can make full disk access configuration profiles in JAMF's console, its the Privacy Preferences Policy Control payload. If you want to upload a .mobileconfig, you can use a tool like iMazing Profile Editor or ProfileCreator to make the config profile with a GUI. ProfileCreator lets you view the XML in app.
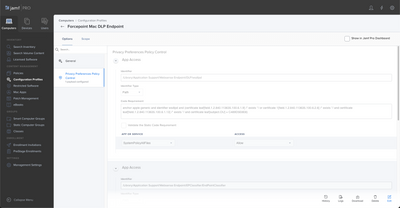
This is an example of full disk access for an application called ForcePoint to give you an idea of what it would look like.
JAMF
ProfileCreator
iMazing Profile Editor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-22-2023 06:01 AM
Thanks!
It works as expected when I create configuration profile via jamf pro payloads.
The issue is that I need a plist upload, because the goal is to add a custom HIP check to Global Protect.
GP can only validate custom checks for macos with plists.
As I got it, you can't get a plist from a conf profiles configured with payloads.
And when I try to upload conf profiles as plists with either eset's or some apple's Preference Domains it doesn't work as expected: ESET AV doesn't receive Full Disk Access.