- Jamf Nation Community
- Products
- Jamf Pro
- New Nasty making the rounds - Backdoor.MAC.Eleanor
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2016 07:16 PM
It's a trojan that comes along for the ride with a an app called EasyDoc Converter.app. It's a full-access backdoor which uses your expected resources of Tor, pastebin, etc.
I can't actually find the application anywhere (not that I looked that hard) but I've already setup "EasyDoc Converter.app" in my restricted software. I'm not sure that's the actual process name of the app at launch (when it prompts for credentials to get in place). :-
http://www.cultofmac.com/436670/dangerous-new-mac-malware-fully-compromises-os-x/
https://labs.bitdefender.com/wp-content/uploads/2016/07/Backdoor-MAC-Eleanor_final.pdf
Solved! Go to Solution.
- Labels:
-
Restricted software
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2016 11:44 PM
The consensus elsewhere is that this was found on macupdate . com. (Not putting a link to the site for obvious reasons).
The moral here is to always check where you are downloading your apps and installers from, run the pkg through Pacifist or Suspicious Package (my preference) and trash stuff without running it if in any doubt.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2016 11:44 PM
The consensus elsewhere is that this was found on macupdate . com. (Not putting a link to the site for obvious reasons).
The moral here is to always check where you are downloading your apps and installers from, run the pkg through Pacifist or Suspicious Package (my preference) and trash stuff without running it if in any doubt.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-06-2016 07:35 AM
Yeah, looks like they'd already taken it down. I checked there and even a few google searches. Wasn't too popular to begin with from what I can tell.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-06-2016 02:00 PM
I personally think the likelihood of having this in the fleet is very low - there are probably also other EA's out there, this is another to see if installed by returning either "None" or the path to each instance of ~/Library/.dropbox
#!/usr/bin/perl -w
my $userlist = `dscl . list /Users`;
chomp $userlist;
my @excludedusers = split(" ","daemon nobody _amavisd _appleevents _appowner _appserver _ard _assetcache _astris _atsserver _avbdeviced _calendar _ces _clamav _coreaudiod _coremediaiod _cvmsroot _cvs _cyrus _devdocs _devicemgr _displaypolicyd _distnote _dovecot _dovenull _dpaudio _eppc _ftp _gamecontrollerd _geod _iconservices _installassistant _installer _jabber _kadmin_admin _kadmin_changepw _krb_anonymous _krb_changepw _krb_kadmin _krb_kerberos _krb_krbtgt _krbfast _krbtgt _launchservicesd _lda _locationd _lp _mailman _mbsetupuser _mcxalr _mdnsresponder _mysql _netbios _netstatistics _networkd _nsurlsessiond _nsurlstoraged _ondemand _postfix _postgres _qtss _sandbox _screensaver _scsd _securityagent _serialnumberd _softwareupdate _spotlight _sshd _svn _taskgated _teamsserver _timezone _tokend _trustevaluationagent _unknown _update_sharing _usbmuxd _uucp _warmd _webauthserver _windowserver _www _wwwproxy _xserverdocs");
my @userslist = split("
", $userlist);
my @users;
my $result = "";
foreach my $u (@userslist) {
my $match = 0;
foreach my $e (@excludedusers) {
if ("$u" eq "$e") {
$match = 1;
}
}
if ($match == 0) {
push(@users, $u);
}
}
foreach (@users) {
my $home = `dscl . -read /Users/$_ NFSHomeDirectory | cut -d " " -f 2`;
chomp $home;
if (-e "$home/Library/.dropbox") {
$result = $result . "
$home/Library/.dropbox";
}
}
$result =~ s/^
+//;
if ($result =~ /^$/) {
system "echo "<result>None</result>"";
} else {
system "echo "<result>$result</result>"";
}- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-07-2016 06:46 AM
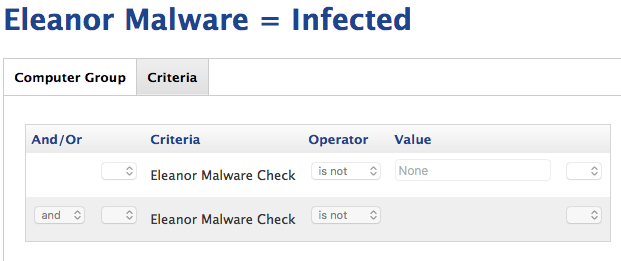
To find infected results you will need a smart group similar to this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2016 03:46 PM
@lisacherie is the blank field supposed to work? I thought that broke?
https://donmontalvo.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2016 07:48 PM
Hi @donmontalvo !
It still works at least on 9.96, haven't tried it with 9.97.
I think some people may have used the or instead of and in the smart group logic, which would make the results incorrect.
The screen shot above is what I've used with success. (Never had any infected, tested it by creating an empty file where the malware would).
Did you see any infected clients?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2016 12:27 AM
Hi Lisa, McAfee ENSM handles vulnerabilities, which is a good thing, when the team that manages that service is collaborative and responsive. :) I was curious about using blank fields in logic.
https://donmontalvo.com