New system extensions for Bitdefender
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
01-14-2021
07:14 AM
- last edited
4 weeks ago
by
![]() kh-richa_mig
kh-richa_mig
Hi,
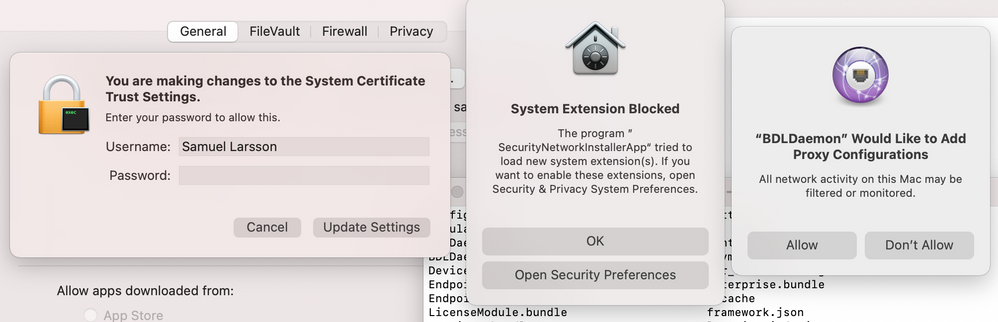
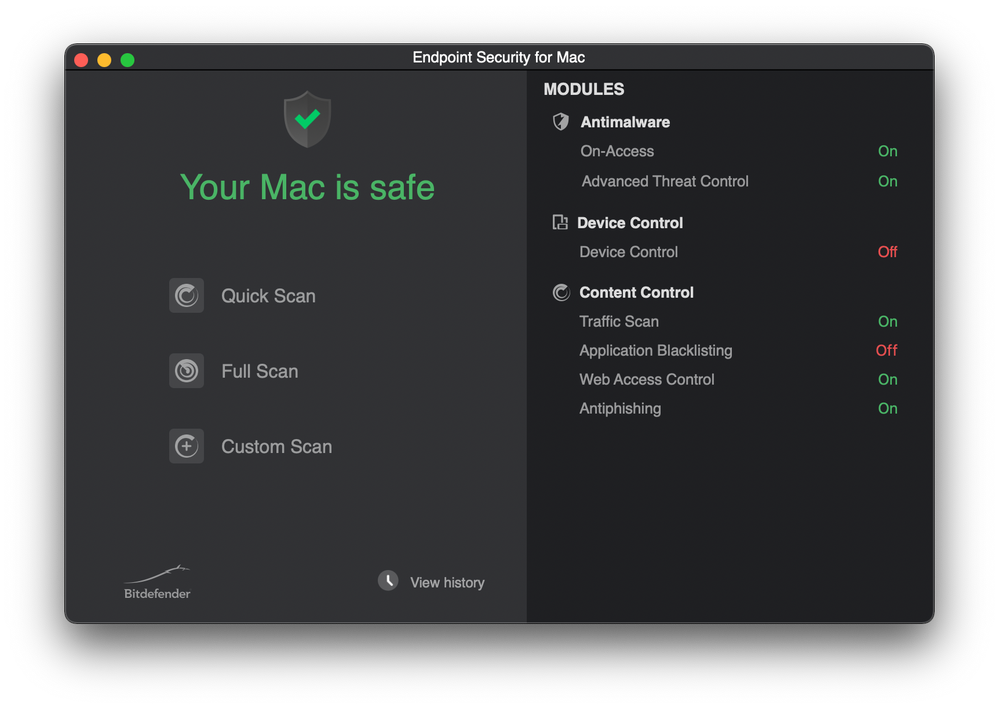
Bitdefender has activated a new web content control module in the Endpoint Security app, which now results in the end user having to approve a system extension.
I have tried to add the below approved system extensions in a config profile, but they still show up. What else can I do?
- Labels:
-
Configuration Profiles
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-11-2021 06:55 AM
@samuellarsson I got hit by the same thing today after my clients for 4.15 update of Bitdefender, here is my configuration and early testing shows it is working for now.
Got info from this page https://www.bitdefender.com/support/changes-to-bitdefender-endpoint-security-for-mac-in-macos-big-su...
export the SSL cert from one of you clients keychain as .cer and add it to your payload.
Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-11-2021 06:59 AM
Hi Samuel,
Did you manage to get this working?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-12-2021 06:46 AM
@greatkemo Thank you for your step-by-step tutorial.
I managed to make it work but, is there a way to avoid having to type in the password for the certificate?
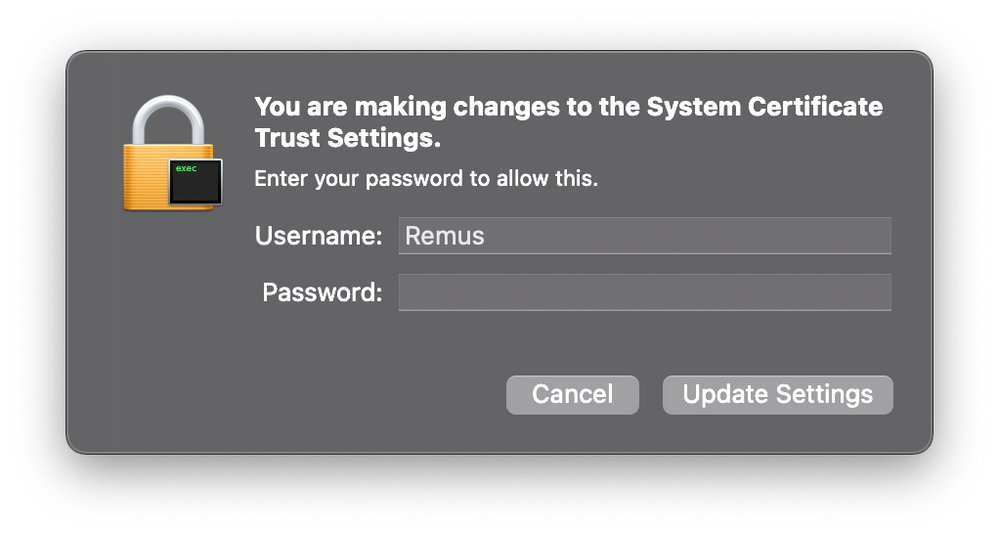
I exported the Bitdefender CA SSL certificate from my test machine and added it to JAMF. The certificate gets pushed from JAMF but then when Bitdefender starts, it ask for credentials to modify The System Certificate Trust……
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-12-2021 06:51 AM
@remus I am not seeing this issue, did you check the box for Allow all apps to use this certificate?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-12-2021 07:11 AM
@greatkemo Ahaaaa! It is checked.
I'm testing on Big Sur 11.1.
If you are not seeing the same behaviour then maybe there is bug in 11.1. (Wishful thinking, hehe)
I'll update to 11.2.1 and test again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-12-2021 07:51 AM
@remus and you selected your certificate in the Content Filter payload?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-12-2021 08:44 AM
One thing I would also add, when I exported the cert from my laptop, it was already trusted, I did not have an issue with the trust. Not sure if that helps or not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-14-2021 11:27 PM
@greatkemo This is driving me nuts… Still not working! Every time I have to authenticate to make changes to the certificate.
When JAMF pushes the certificate it is "Always Trust"-ed in the keychain.
As soon as Bitdefender installs, it creates another certificate that needs to be authenticated.
Is there a chance I could have your Configuration Profile for Bitdefender?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2021 04:42 AM
@remus this is giving me trouble now too. It seems if the client already had BD installed it does not give me a prompt, but if it is a new install, I get the prompt to trust the certificate. I need to work on it a bit more and see what is the deal with it, and maybe even open a case with Bitdefender to provide better documentation for deploying with jamf pro.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2021 04:47 AM
I just looked through Bitdefender support site and they have put up new documentation for jamf pro.
Here is the link: Bitdefender Endpoint Security for Mac: How to Configure Jamf Pro for macOS Big Sur 11.0 and later
However, this is nothing in there about the certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2021 05:06 AM
@greatkemo Ooooo goody… It's not just me then!
I called Bitdefender and they told me to follow the information on that document that you also linked.
Now I'm writing back to tell them that the information in that documentation is incomplete. There is no mention on how to handle the certificate.
So go ahead and open a case as well! The more the merrier! :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2021 05:14 AM
I suppose this is another way of doing it...
https://www.jamf.com/jamf-nation/discussions/36644/how-to-set-a-self-signed-certificate-to-always-tr...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2021 06:10 AM
@remus What I think is happening is when BD runs, it is adding the certificate, and it looks like they are not using the updated API through their app to trust it. It is pointless to try and add the cert using a profile because it seems to be ignored and another cert is installed with a different expiry date and all. So this needs to be fixed by the developer in a future update. Hopefully soon.
As for the add-trust using the security command, that has been changed in Big Sur and will prompt for user authentication.
https://developer.apple.com/documentation/macos-release-notes/macos-big-sur-11_0_1-release-notes#Sec...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2021 06:49 AM
@greatkemo Thank you so much for your feedback.
I also realised that the "add-trust" command thingy is not "silently" working anymore. :(
I'll keep you posted in case I hear back from the Bitdefender people.
I wrote back that the certificate part of their documentation is missing. I haven't heard anything back yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2021 07:36 AM
Experiencing the same issues and have also gone back and forth with Bitdefender support.
Currently, I'm at a point where I have configured a Configuration Profile using the instructions provided by Bitdefender.
https://www.bitdefender.com/support/bitdefender-endpoint-security-for-mac:-how-to-configure-jamf-pro-for-macos-big-sur-11-0-and-later-2661.html
However, this Configuration Profile is not allowing the System Extension, nor accepting the SSL Certificate (of course nothing in the Configuration Profile that would do so)
For now I am focusing on the System Extension, waiting back on Bitdefender support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2021 07:44 AM
@cmasciarelli-L You should have a working System Extension and Content Filter after following the above article. As for the certificate, we've all been bitten by it, so waiting on a reply from support. But this is something their devs would probably need to fix so could take a while. They should not have put this update out as a fix for the content control not working in Big Sur, and leave us with a whole new problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-16-2021 04:40 AM
@greatkemo We got our answer from Bitdefender… and the answer is kind of embarrassing. It looks like a half-baked compatibility with Big Sur.
At this time we do not support importing the certificate through Jamf PRO because the certificate is unique for each station.
The certificate is generated locally on each station. For this reason they cannot be imported through Jamf PRO.
We have opened an internal case to find a solution to accept the certificate through JAMF Pro but we do not have a deadline for when it will be implemented.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-16-2021 04:59 AM
@remus I also got a lame response from them, which basically said that I was doing it wrong and that I should follow the steps in all the links which I already followed anyway.
I am sure the issue is this....
When you get prompted for a password to trust the certificate do this:
ps aux | grep add-trusted-cert | grep -v grepYou should see...
/usr/bin/security add-trusted-cert -d -r trustRoot -k /Library/Keychains/System.keychain /Library/Bitdefender/AVP/antivirus.bundle/rootCA.pemSo you can see that the app is trying to add their CA to the trust using the security command, which now in Big Sur requires users to authorize this transaction.
Instead, developers need to use Apple's API for certificates to add items to the keychain
https://developer.apple.com/documentation/security/certificate_key_and_trust_services/certificates
The annoying thing is, this is not new news a surprise from Apple, this was mentioned months ago.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-16-2021 05:59 AM
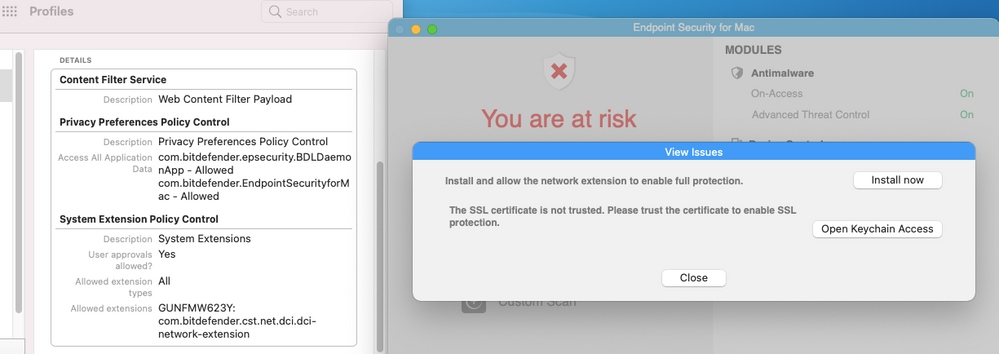
I'm still struggling with the System Extension for some reason.
Here is what my Configuration Profile looks like
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-16-2021 06:21 AM
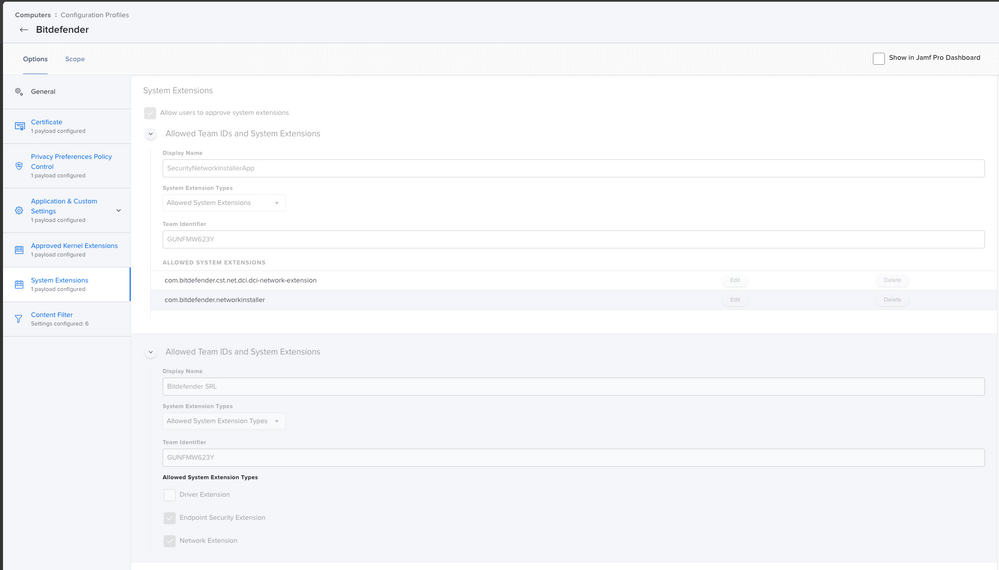
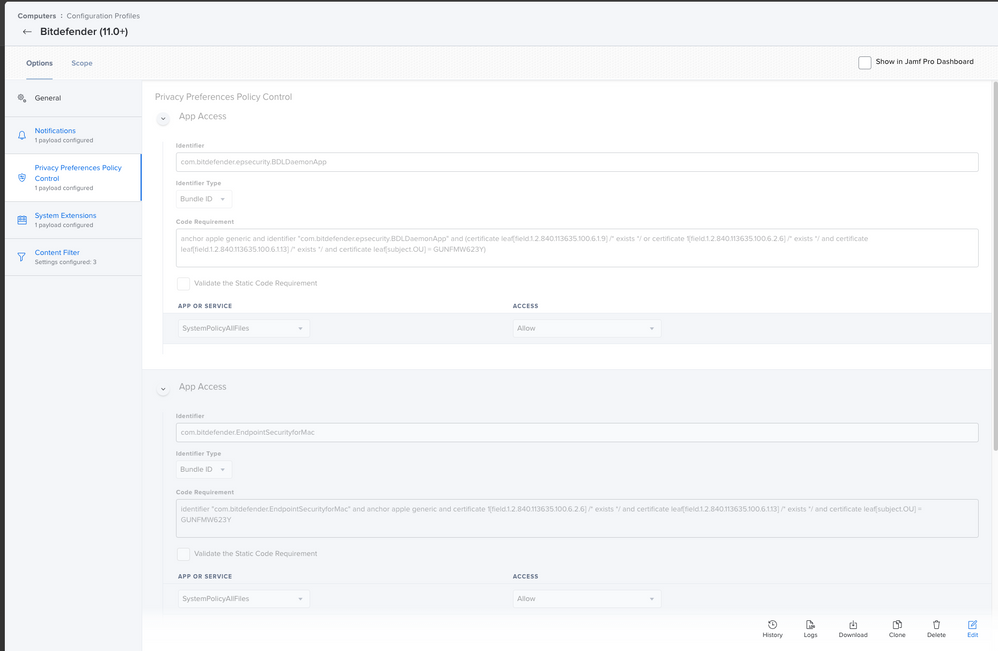
@cmasciarelli-L You probably did not checked Network Extension.
Use these screen-grabs as an example!
But you are going to hit a wall when it comes to the SSL Certificate.
In order to avoid that, disable the Content Control module and leave active only the Antimalware module.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-16-2021 06:53 AM
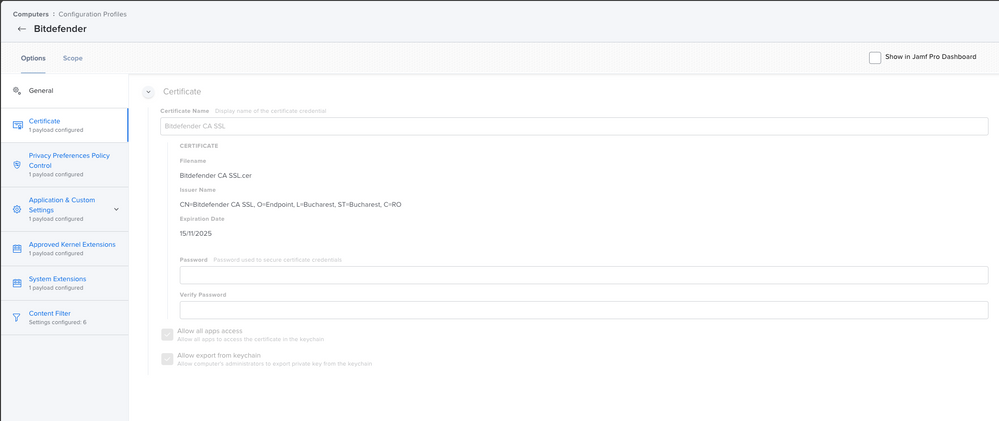
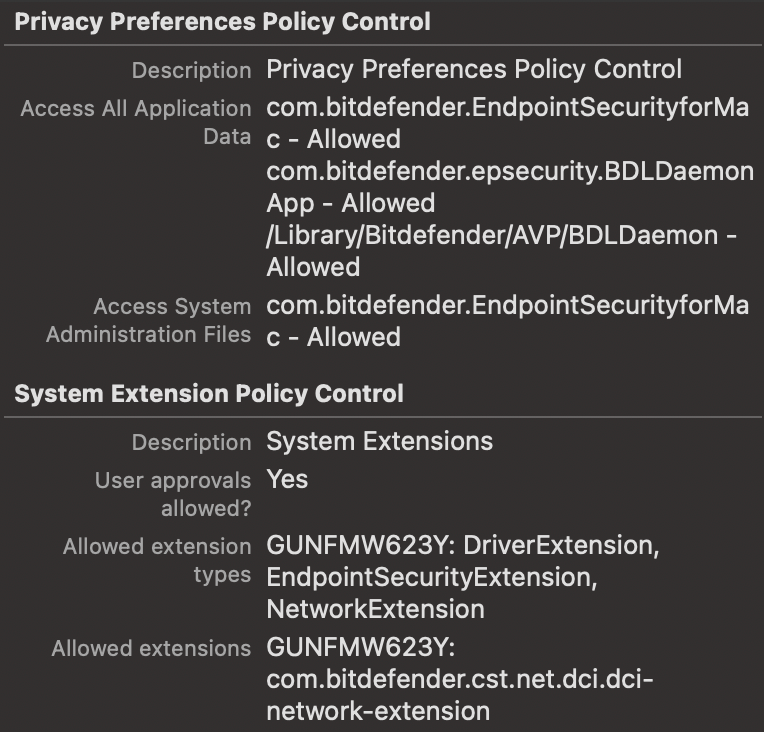
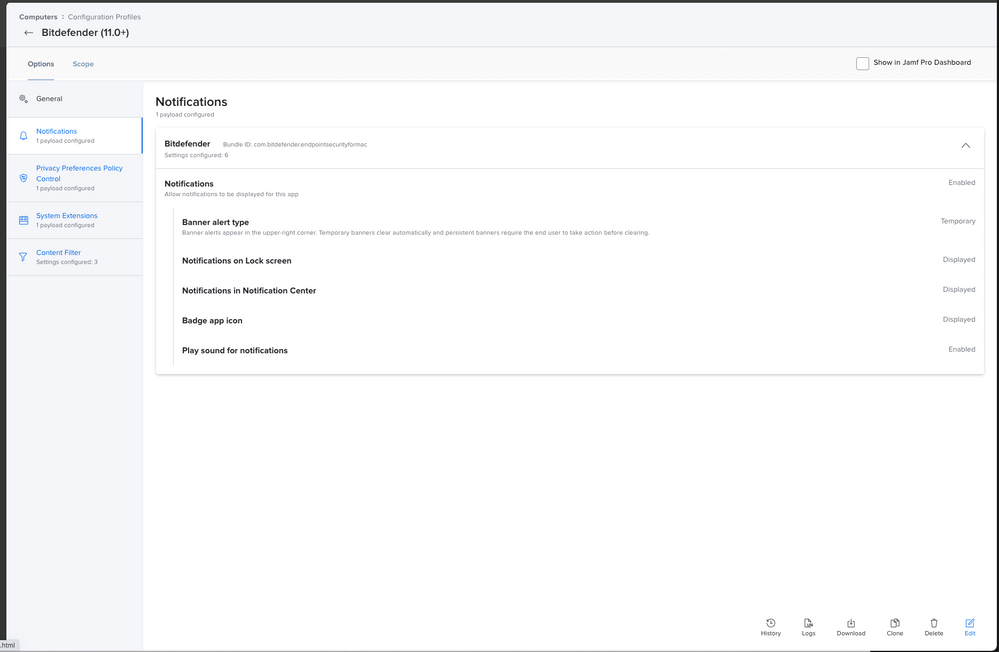
Use these, they are tidier and working (apart from cert of course), but don't forget these will work on Big Sur and Catalina if you have older clients then add Kernel Extension as well.
General
Notifications (Jamf Pro 10.27.0)
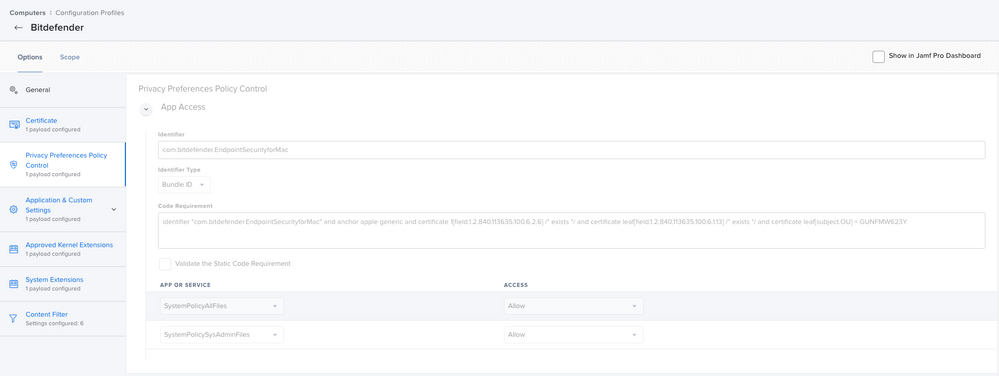
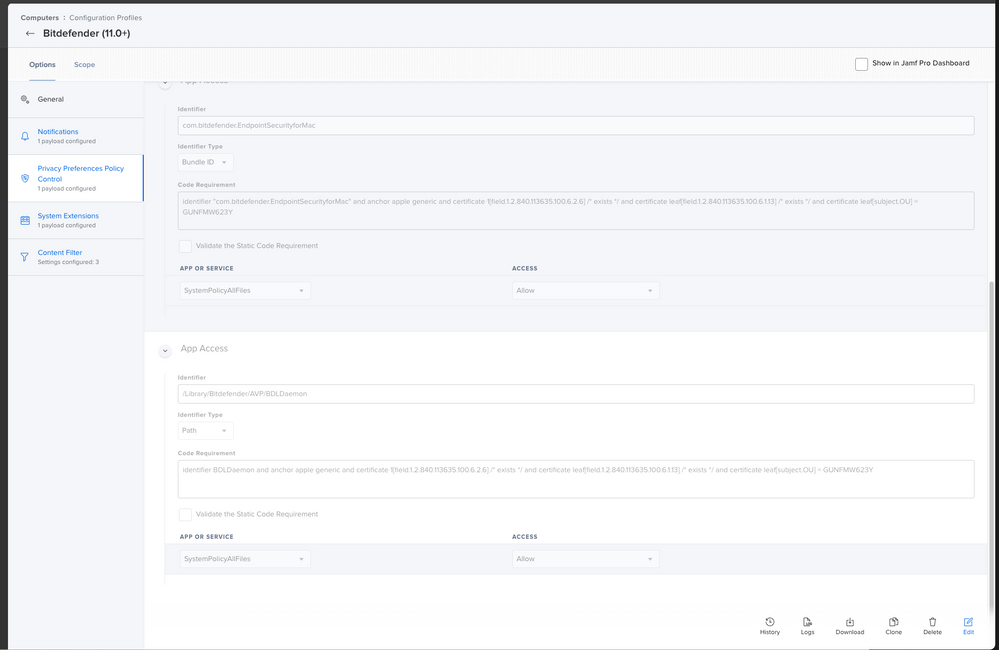
Bundle ID: com.bitdefender.endpointsecurityformacPrivacy Preference Policy Control
Identifier: com.bitdefender.EndpointSecurityforMac
Identifier Type: Bundle ID
Code Requirement: identifier "com.bitdefender.EndpointSecurityforMac" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GUNFMW623Y
APP OR SERVICE: SystemPolicyAllFiles
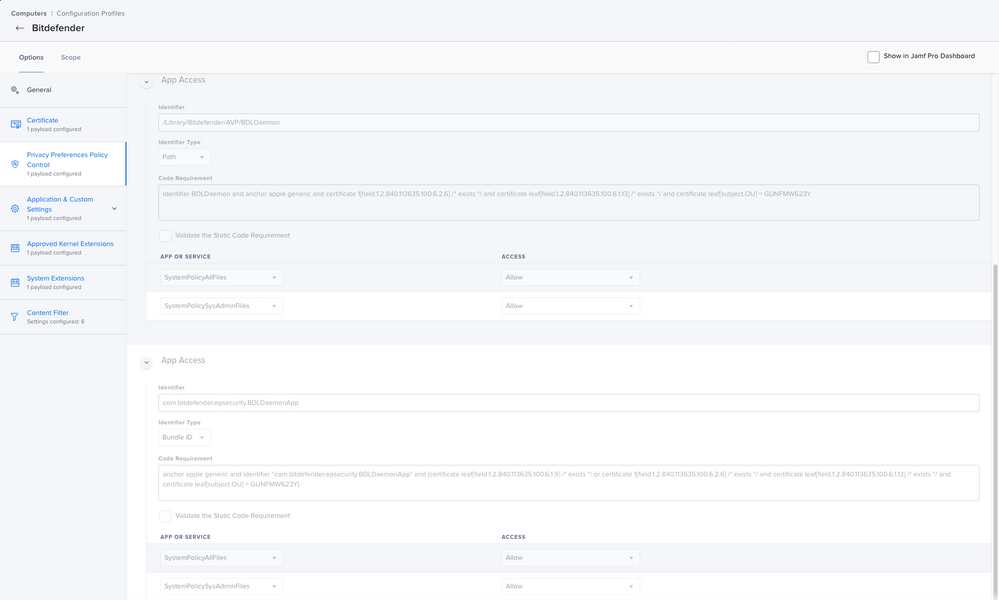
ACCESS: AllowIdentifier: /Library/Bitdefender/AVP/BDLDaemon
Identifier Type: Path
Code Requirement: identifier BDLDaemon and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GUNFMW623Y
APP OR SERVICE: SystemPolicyAllFiles
ACCESS: AllowIdentifier: com.bitdefender.epsecurity.BDLDaemonApp
Identifier Type: Bundle ID
Code Requirement: anchor apple generic and identifier "com.bitdefender.epsecurity.BDLDaemonApp" and (certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GUNFMW623Y)
APP OR SERVICE: SystemPolicyAllFiles
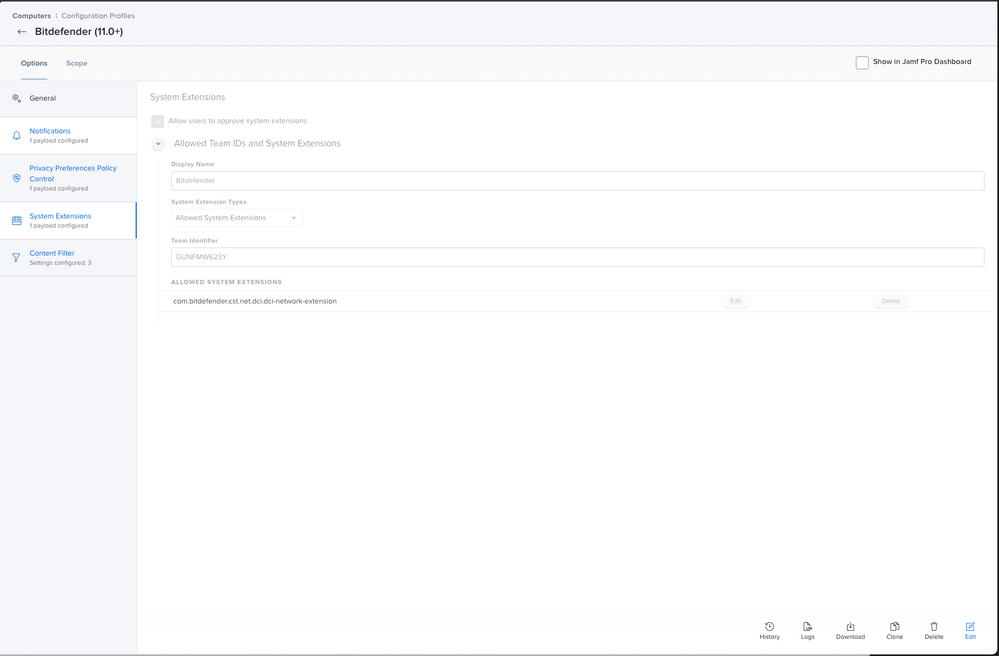
ACCESS: AllowSystem Extension
Display Name: Bitdefender
System Extension Types: Allowed System Extensions
Team Identifier: GUNFMW623Y
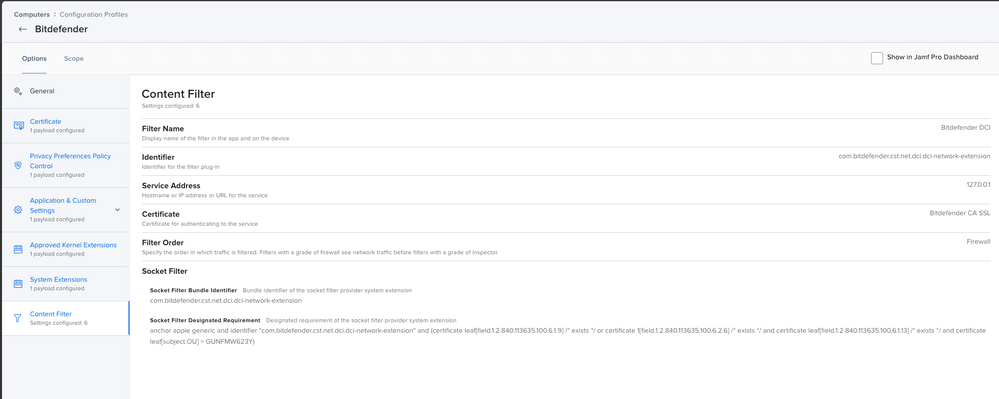
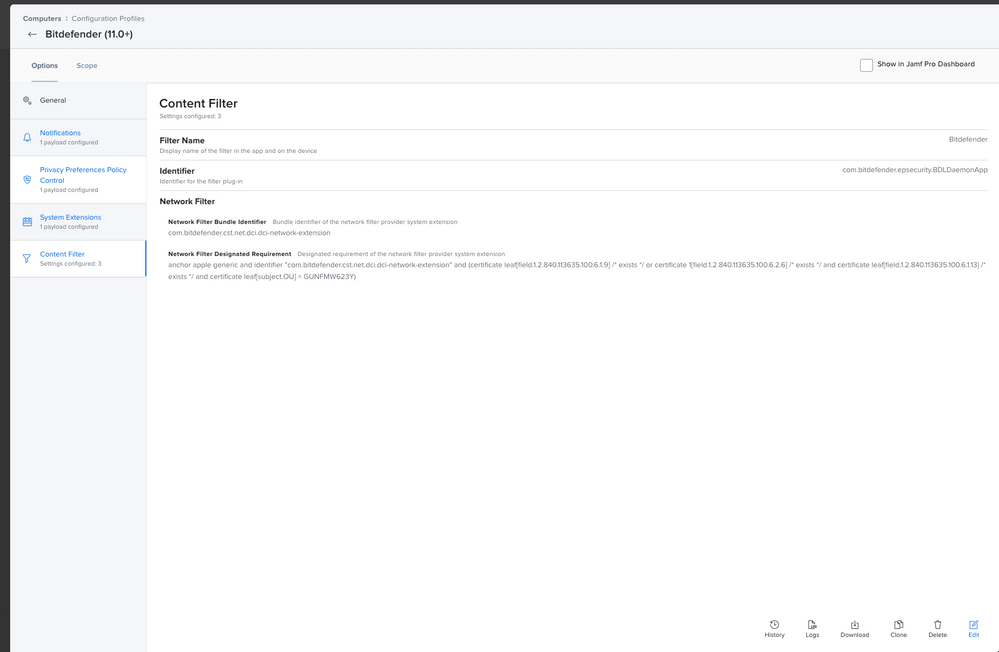
ALLOWED SYSTEM EXTENSIONS: com.bitdefender.cst.net.dci.dci-network-extensionContent Filter
Filter Name: Bitdefender
Identifier: com.bitdefender.epsecurity.BDLDaemonApp
Network Filter Bundle Identifier: com.bitdefender.cst.net.dci.dci-network-extension
Network Filter Designated Requirement: anchor apple generic and identifier "com.bitdefender.cst.net.dci.dci-network-extension" and (certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GUNFMW623Y)Hope this is helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-01-2021 06:52 AM
Has anyone tried generating a SSL cert as noted here (notably talking about iOS)?
https://www.bitdefender.com/support/creating-security-certificates-1217.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-09-2021 09:29 AM
Anyone had success with this? After a few rounds of emails back and forth with BitDefender - they've advised that the end-user must manually trust the cert which is frustrating. Certainly, there must be another way?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2021 11:57 PM
Anybody is having issues with installing the latest packages from Bitdefender using Jamf Pro? they have now a pkg for intel Macs and another one for M1 Macs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-06-2021 04:19 AM
I've also hit this issue - Thankfully we don't actually make use of Content Control which got me wondering why the hell it was showing as a loaded module even though it's disabled!
I did a reconfigure on the client and it's now not showing the Content Control in the BEST main window.
I then created a new Package for Mac OS deployment without the CC module in there and noticed that the download URL differed from the original one I was using.
I've now updated the installer script in Jamf Pro to use that installer and hope it removes this prompt :)
I know it's not ideal if you do use CC but may provide some help for those who don't use it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-09-2021 04:21 AM
Do you folks have any ticket numbers that can be referenced for the SSL cert trust issues? I'm going to log a ticket about this too, and it would be worth adding additional weight.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-09-2021 04:43 AM
@remus
Thanks for that . The additional path to the BDLDaemon was what I was missing from my CCCP. Funny how Bitdefender doesn't provide that info but tells you everything else to go into the CCCP. /shrug
Thankfully, we don't seem to be suffering from the SSL cert trust issues some are having.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-09-2021 06:39 AM
For anyone experiencing issues on Monterey a couple changes are needed.
Note: I have been able to deploy the SSL cert without Bitdefender reporting errors, though it's not appearing in Keychain access so I am not sure if it's actually present on the machine.
In my PPPC payload I added the following for good measure
Identifier: com.bitdefender.networkinstaller
Identifier Type: Bundle ID
Code Requirement: identifier "com.bitdefender.EndpointSecurityforMac" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GUNFMW623Y
App or Service: SystemPolicyAllFiles - Allowed
And with that I added more to my System Extensions Payload:
System Extensions
Allow users to approve system extensions: True
Display Name: Bitdefender
System Extention Types: Allowed System Extensions
Team Identifier: GUNFMW623Y
Allowed System Extensions: com.bitdefender.cst.net.dci.dci-network-extensions, com.bitdefender.networkinstaller
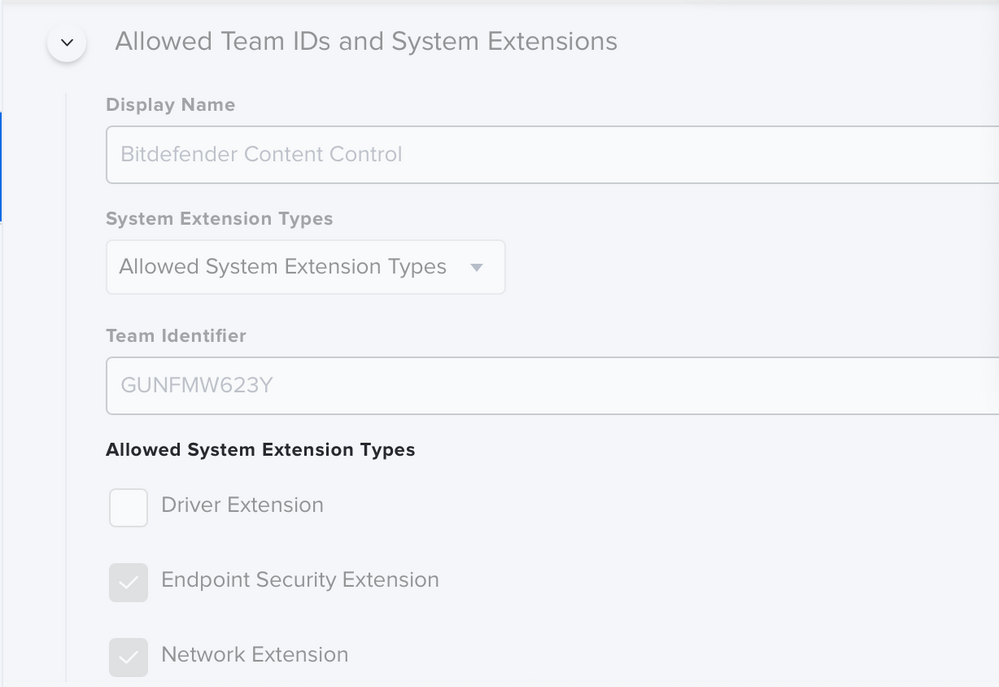
Allowed Team IDs and System Extensions
Display Name: Bitdefender Extensions
System Extension Types: Allowed System Exception Types
Team Identifier: GUNFMW623Y
Allowed System Extension Types: Driver Extension, Endpoint Security Extension, Network Extension
The rest of the policies such as Content Filter can stay the same as above.
Additionally, if you are on Bitdefender 7.2.4.20013, with Monterey (and presumably with Filevault enabled), you need to upgrade to version 7.2.6.20020 or newer otherwise the app crashes repeatedly.
The only way I was able to uninstall 7.2.4.20013 was by removing my BD Configuration Profiles, rebooting, uninstall, pushing the profiles back, and installing the new version.
After all of these steps I get a happy Bitdefender with all features working and no crashing. It's also 'configless' on install, as in the user doesn't have to accept any sort of prompts whatsoever, nor enter any passwords.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-09-2021 11:29 AM
Hi guys,
I'm at Monterey and I followed all the steps mentioned before here and I got a smooth setup without any user prompts (thanks @seraphina )
I exported Bitdefender CA SSL from keychain and deployed to some macs and Bitdefender shows "Your mac is safe" but when I try to access some websites I got an error saying that the site certificate is not trusted... 😕
Sites like google.com doesn't give us errors, but some sites like app.feedz.com.br
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-09-2021 11:46 AM
I do not get any certificate errors when visiting this site.
I don't think this issue is related to your Bitdefender certificate, but just in case, how are you deploying it?
app.feedz.com.br certificate issuer is from Cloudflare, and the Root CA is Baltimore CyberTrust Root, which is included in the macOS System Certificates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-24-2022 11:40 AM
The issue might be related to how the certificate was generated. How have you generated the certificate.pfx, @seraphina?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-22-2022 09:45 AM
Hi everyone, just wanted to update this thread, in case anyone was stuck with Bitdefender 7.6.xxxxx.
Bitdefender introduced an app downloader that would install the correct version for you based on your architecture. I have updated my script on GitHub and it seems to be working nicely. Don't forget to set $4 and $5 in your policy.
Also, someone at Bitdefender has finally put all the documentation for deploying BD with Jamf Pro all in one place and can be found here be careful with the cert steps, there is a step missing.
Here is what I did and what worked for me:
openssl req -new -days 1825 -nodes -x509 -subj '/C=RO/ST=Bucharest/L=Bucharest/O=Endpoint/CN=Exmple Bitdefender CA SSL' -keyout example_rootca.key -out example_rootca.pem
md5 -s 'creatRandomPassword' # don't forget to set this password as the package uninstall password in Control Center.
MD5 ("creatRandomPassword") = 044dacc2110efade537fce97710af1cd
openssl pkcs12 -export -inkey example_rootca.key -in example_rootca.pem -out example_rootca.pfx
Enter Export Password: 044dacc2110efade537fce97710af1cd
Verifying - Enter Export Password: 044dacc2110efade537fce97710af1cd
I hope this helps.
Best,
Kamal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-22-2022 09:50 AM
Hi everyone, just wanted to update this thread, in case anyone was stuck with Bitdefender 7.6.xxxxx.
Bitdefender introduced an app downloader that would install the correct version for you based on your architecture. I have updated my script on GitHub and it seems to be working nicely. Don't forget to set $4 and $5 in your policy.
Also, someone at Bitdefender has finally put all the documentation for deploying BD with Jamf Pro all in one place and can be found here be careful with the cert steps, there is a step missing.
Here is what I did and what worked for me:
openssl req -new -days 1825 -nodes -x509 -subj '/C=RO/ST=Bucharest/L=Bucharest/O=Endpoint/CN=Exmple Bitdefender CA SSL' -keyout example_rootca.key -out example_rootca.pem
md5 -s 'creatRandomPassword' # don't forget to set this password as the package uninstall password in Control Center.
MD5 ("creatRandomPassword") = 044dacc2110efade537fce97710af1cd
openssl pkcs12 -export -inkey example_rootca.key -in example_rootca.pem -out example_rootca.pfx
Enter Export Password: 044dacc2110efade537fce97710af1cd
Verifying - Enter Export Password: 044dacc2110efade537fce97710af1cd
I hope this helps.
Best,
Kamal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-18-2023 12:14 AM
Thanks for sharing your script. I am still stuck with this Bitdefender SSL trusting issue. I have tried everything but no luck. I would like to try your script. Please help me with the script, for $4 I will set it to my Jamfpro URL and what should I set for $5?
Also, should I just attach this script alone in the policy or I should attach the package and the script together in the policy?
Thanks
Joy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-18-2023 01:18 AM
Hi Joy,
$5 is the ID for the downloader app.
When you configure a package in the Bitdefender Control Center, a unique URL is generated. In the Control Center, find the package download URL, which should look something like this https://bitdefender.example.com/Packages/MAC/0/abcdEf/setup_downloader.dmg, where in this case "abcdEf" is the package ID. The ID is case-sensitive.
Good luck,
Kamal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-18-2023 01:43 AM
Hi Kamal,
Thanks for the update.
In the policy, should I include the package as well or just the script?
Thanks
Joy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-18-2023 02:46 AM
Hi Joy,
In the policy, you should include two things. The package you should make first contains the certificate, then the script to run after the package. The script downloads the installer package from the server, so there is no need to repackage the installer. Also, this script is for version 7.6x and later.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-18-2023 04:00 AM
Hi kamal,
You are more supportive than Bitdefender support, appreciate it. I have read many articles but seems like only you got it working, congrats.
I have tried a lot of ways but couldn't get the SSL installed on BigSur and above. I hope it works this time with your magic script but just want to make sure I am doing it right.
Steps in my head to do:
1. Download the macOS Downloader (which is for both Intel and M series)
2. Star the composer
3. Drag the setup_downloader.dmg and installer.xml in /Users/Shared
4. Copy the certificate.pfx in /Library/DeployCert
5. Close the composer and create a PKG or DMG
6. Add the package to a policy and the script and make the script to run after the package.
So this should install the Bitdefender and the SSL should be enabled, correct?
Incase if I missed anything or if the order of doing it is wrong, could you please help me with it?
Thanks
Joy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-18-2023 04:31 AM
Are you on the MacAdmins Slack? If so, find me on there, I will do my best to help.
Kamal