Here's the scenario: We connect to our internal Sharepoint site (sharepoint.company.com) and click on an Office document that opens in the appropriate Office 2016 app. As the program launches we're prompted to login to the sharepoint server. We login as needed. The document opens and all is right in the world. The problem we're having is that later if we go to another internal server (someotherserver.company.com) that requires us to login, we immediately get a popup that asks to use a keychain item. This is problematic because not all our *.company.com servers are tied into AD and kerberos. The different servers may have completely different IDs and/or PWs. I looked in my keychain and found the item in question and it is specifically tied to the sharepoint.company.com server. If I delete that keychain item and go to someotherserver.company.com we're no longer prompted to use a keychain item.... until we login to sharepoint through an Office app. Adding to the problem is the fact that this keychain item is not even named something that the end user could possibly know what it was tied to. It generates helpdesk calls. We just flat out don't want or need this "function".
Is there a way to stop this from happening?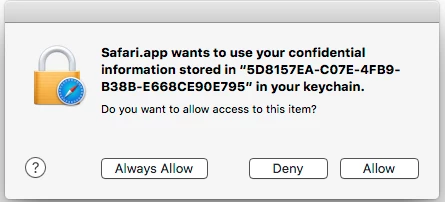
Question
Office 2016 and Sharepoint keychain item
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.



