- Jamf Nation Community
- Products
- Jamf Pro
- Re: PPPC and every app known to IT
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
PPPC and every app known to IT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-31-2018 04:59 PM
I'm starting to get my head around this PPPC joke....
It appears I am going to have to create a PPPC profile for almost every application that does anything... for example, Photoshop and After Effects....
So, have I missed something that means I only need to deploy one profile? or am I doomed to installed a PPPC profile for every Application I want my users to access?
TIA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-01-2018 04:42 AM
Our solution has been to identify the critical/core apps that all of our users use on a daily or regular basis, and create a unique config profile for each of those applications/scenarios. You do have the option of having one large PPPC config profile, but currently there's no way to edit the config profile in jamf on the server side, and I wouldn't rely on their PPPC utility to go back and edit existing profiles. With that in mind, having individual profiles for each application makes it so that you can easily change something inside the profile without needing to rewrite the whole thing from scratch. Again though, I wouldn't do it for every application. Allow users to make the choice on non-critical apps, and provide an option in self service to reset their permissions if they accidentally choose the wrong option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-01-2018 07:45 AM
Having test users that can take screenshots of the PPPC prompts was very helpful at my org. At first I made a giant profile with everything, but over time as I've made adjustments or additions I've slowly split each app off into its own profile.
I agree with @float0n that you can't reasonably whitelist everything, so I focused on the core apps that we provision. Anything else is educating users as to what to expect. I also followed this suggestion of creating a self-service item to reset the TCC database if a user unintentionally clicks deny when they should have allowed something.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-01-2018 02:14 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2019 09:31 AM
I am also coming to the conclusion that every single app that has ever seen the light of day here will need a PPPC config created for it. This is not at all feasible. I don't know that I could ever do this because we do a lot of java development and our devs do things in bash, sh, zsh, and a few other shells. In my limited testing, I've seen prompts to allow the various shells to have access to various things. I hate to see what i'm going to have to do with homebrew!!! Today I had to figure out how to create a freaking PPPC profile for the Zoom Outlook Plugin. This will be a full time job just creating PPPC and approved kext profiles. It's all the background, support processes/apps, and plugins that will get you because you, as the admin, may never in a million years try each and every possible option within an app to discover the ones that trigger PPPC prompts, but the users might.
If a user gets prompted for something I have not seen yet and they click on Do Not Allow when they should have clicked Allow, will a PPPC profile installed afterward override that denial of access?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2019 10:55 AM
@AVmcclint In my testing anything that a user approves (or denies) can be overwritten by a PPPC profile. Camera and mic access are somewhat of an exception in that an MDM can't approve those for the user. So if they click Don't Allow (or even just ignore the pop up until it times out) you'll need to put something in self-service so the user can resolve the issue.
tccutil reset Camera
tccutil reset Microphone- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-05-2019 03:32 PM
Has anyone installed profiles that don't work as configured? We have set one up with an Apple Event to allow access to MS Outlook, yet the user still gets the Allow/Don't Allow prompt .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-05-2019 05:10 PM
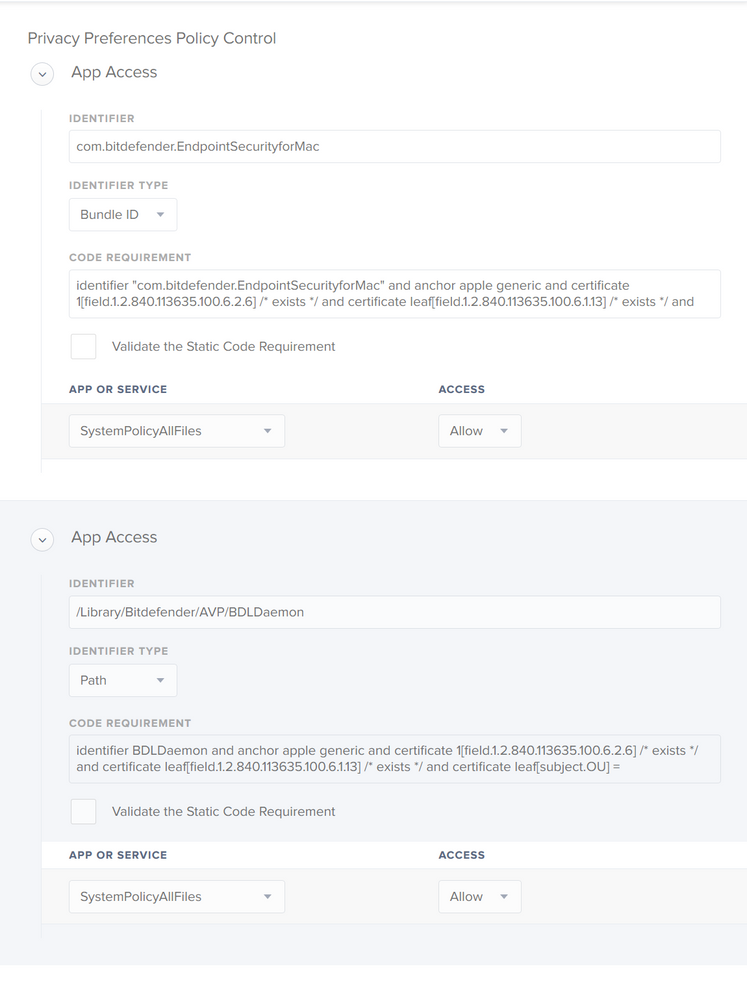
I had this problem with setting PPPC on BitDefender for full disk access. The solution was to provide the full path to the binary in the Indentifier instead of just the binary name, so we have 2 entries.
You also have to provide the PPPC profile with ALL the binaries that the app will be communicating with, refer to
Jamf Events Profile
Jamf PPPC Compendium
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-21-2019 03:59 AM
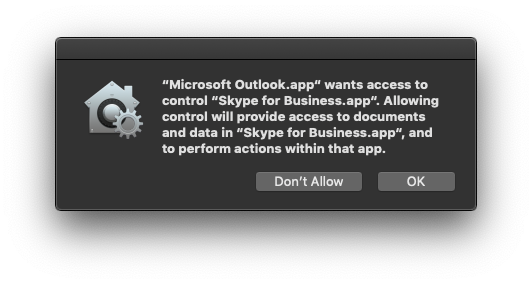
I'm just barely getting started with Mojave and it is already getting out of hand. I just upgraded a eager user's Mac to Mojave yesterday and within 15 minutes he was prompted for 5 different PPPC related actions! Including one to allow the Logitech driver to allow him to use the scroll wheel on his mouse! Then he sent me this screenshot:
Now we have to allow apps to access other apps? Has Apple given any official guidance on how to manage a Mac that runs more than Pages and Keynote? I don't have the time and resources to create PPPC profiles for each and every application and process and shell command that my users use on any given day. However if this is the only way to make sure the programs run the way they are intended, I can't afford not to create profiles either. What happened to the days when our Macs "just worked"?
This constant prompting reminds me of Windows Vista. Remember how well that was received?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-21-2019 04:42 AM
@AVmcclint I'm with you on that one....I have one or two that live on 10.14 and usually it's something like this at least once or twice a week. On top of that, we use over 110 unique software titles in the district, if not more. I wish there was something like a plist manifest that showed all the possible requests that a given software title could ask for built in the app and then I could whitelist the whole thing, removing ONLY specific ones that we specifically do not want to allow usage to. Something like this would remind me of "Manifest Destiny"...having a nice listing somewhere of what titles are requesting, instead of relying on emails from end users or searching forum threads for "PPPC and <fill in software title here>" or "TCC and <fill in software title here>"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-21-2019 09:02 AM
Out of curiousity, do you know which version of Outlook that is appearing on? I have not seen that one myself yet, but majority of my users are still on High Sierra. I've had to make profiles for several security related apps already (primarily Cisco related), but I have yet to see something like that. And I am fearing the day I do (although Skype will be gone soon)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-21-2019 09:32 AM
My user got the message using Outlook 16.16.5. Later I tried it on 16.23 on another Mac after I built the PPPC profile then I got the same error in reverse for Skype needing to control Outlook. I recreated the PPPC profile so it allows Outlook to control Skype AND so Skype can control Outlook - all in the same profile.
Another thing about this that is highly annoying is that it is very difficult to replicate the alerts. Yesterday I had to build a profile to allow iTerm to access the drive. I tested the profile successfully, then when I quit iTerm it gave me a message that iTerm needed access to something, but I was in a hurry and didn't get a chance to take a screenshot or document exactly what it needed. I shut the mac off and figured I'd replicate the message this morning. I can't get the alert to come back up now and my user never saw that particular alert at all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-01-2019 10:35 AM
When writing one of these manually, where does one get the "code requirement"? I'm trying to write an allow for the NWEA secure testing browser.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-16-2019 08:30 PM
Found this chat that is 100% relevant to my current blocker.
More and more apps within our macOS Mojave 10.14.x are requiring this PPPC permissions just to install and run simple applications.
Should we (as a community) come up with a list and PPPC settings required?
Sorry, I can't contribute much to this list, as I don't know any PPPC settings required.
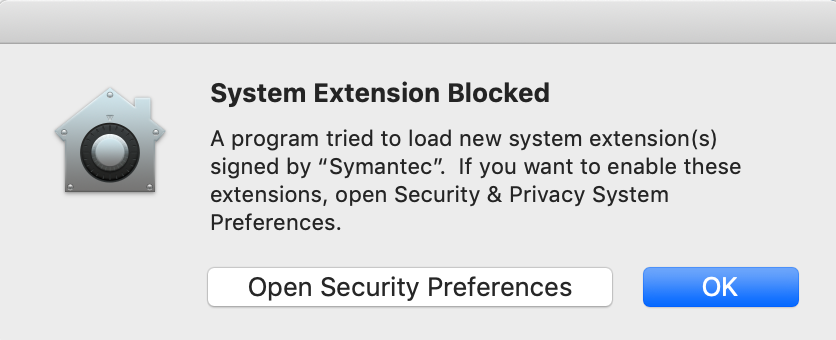
So far I am seeing the "allow" pop-up when installing:
Symantec DLP
McAfee ENS 10.6.1
DisplayLink v5.1
Parallels Desktop
Junos Pulse Secure
FireEye
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-17-2019 06:37 AM
@Bernard.Huang What pop-ups are you seeing for Symantec DLP? Our org uses that service, and we've never encountered a PPPC permission warning, so curious as to what you saw. My org made Mojave available in self-service about a month after release with a set of PPPC profiles that whitelisted our core apps. We've never included DLP b/c we never got a warning.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-17-2019 05:23 PM
We're definitely seeing Symantec DLP PPPC pop-ups.
We are installing Symantec DLP v15.0 onto Mojave 10.14.2 and beyond.
I also notice for McAfee ENS, when we install 10.2.3, there is PPPC.
When upgrading from 10.2.3 to 10.5.9, there was no PPPC question. I suspect it is because it is already allowed.
When upgrading from 10.5.9 to 10.6.1, there was the PPPC question again.
For ALL these applications, I would love to know what app name it is kicking off, that is triggering this PPPC.
Then I can get on with creating the .mobileconfig file to cater for them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-17-2019 05:52 PM
Hi @mlizbeth
I'm reading your screenshot.
Could you share how you got the Code Requirement information = identifier "com.bitdefender.EndpointSecurityForMac" and anchor..... ?
And what is this Code Requirement field used for?
Update
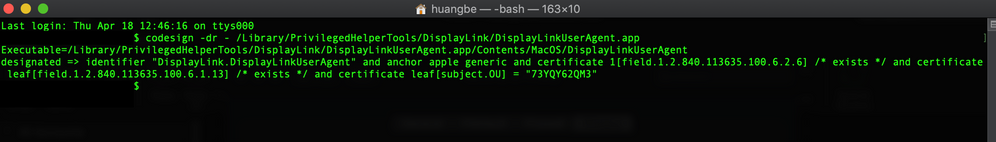
I got it. Some more research show if I put in codesign -dr - /path/to/app , then the Code required will show.
Example:
codesign -dr - /Library/PrivilegedHelperTools/DisplayLink/DisplayLinkUserAgent.app
Executable=/Library/PrivilegedHelperTools/DisplayLink/DisplayLinkUserAgent.app/Contents/MacOS/DisplayLinkUserAgent
designated => identifier "DisplayLink.DisplayLinkUserAgent" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] / exists / and certificate leaf[field.1.2.840.113635.100.6.1.13] / exists / and certificate leaf[subject.OU] = "73YQY62QM3"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-17-2019 07:24 PM
@AVmcclint - I'm with you on this PPPC bs.
I have a further question. If a user does dismiss the question and not allow the application to run properly, is there a way to get this question back?
I have a few users already stumbled when macOS Mojave ask for permission.
Since they don't have admin rights, I have to push out admin rights, then manually uninstall the application. Then reinstall the application via Self Service again, then the PPPC pop-up will happen again, now we can select Allow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-18-2019 03:31 AM
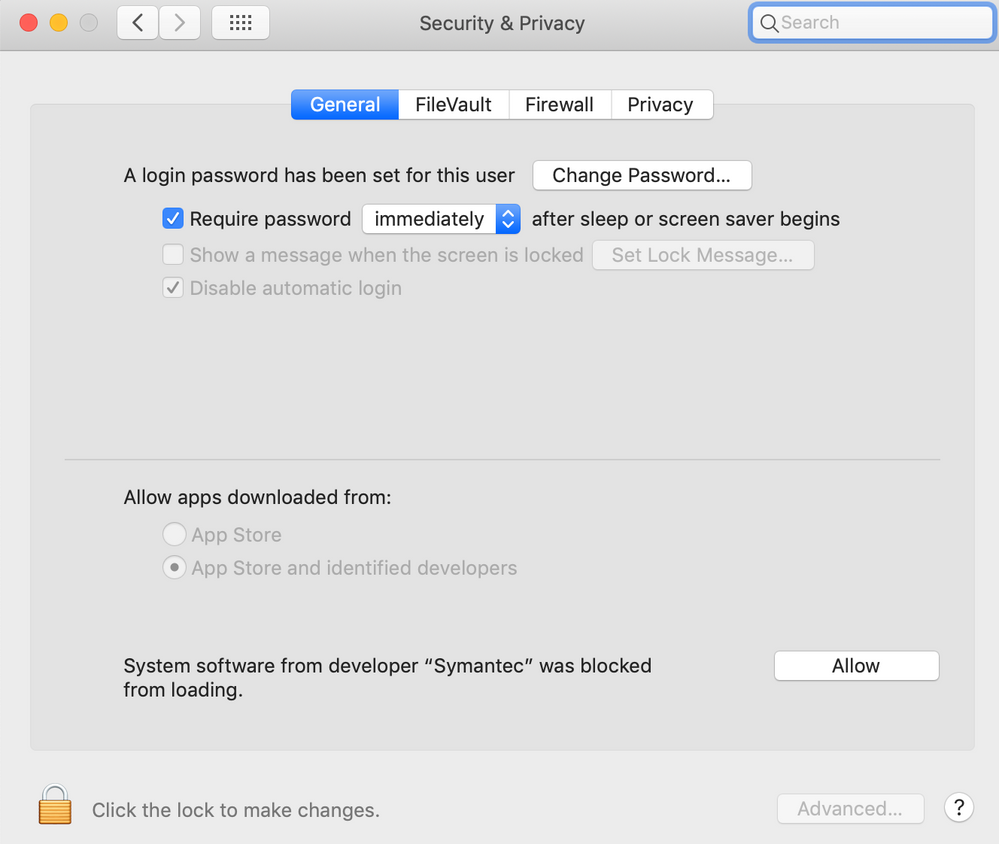
I have found that if an app requests access to the camera or microphone and the user disallows it, they can go into System Prefs > Security > privacy and change the settlings for Camera and Microphone even if they aren't admins. That's all I've been able to confirm though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-18-2019 06:50 AM
@Bernard.Huang Ah ok, yes that's a screenshot to approve the DLP kernel extension. And we definitely have a kernel extension whitelist profile for that, but that specific warning is not PPPC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-18-2019 04:44 PM
Thanks for clarifying.
Sounding like an amateur now.... What's the difference between Kernel extension and PPPC?
I'm asking from the perspective of how to automatically allow it. For Kernel extension or PPPC, don't I need to set up the Privacy Preference Policy Control just the same?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-18-2019 05:45 PM
@Bernard.Huang User Approved Kernel Extensions arrived with High Sierra 10.13.4, Privacy Preferences Policy Control arrived with Mojave 10.14. They're different things despite both being things a user has to visit the Security & Privacy panel in System Preferences to approve if you don't get your configuration profiles right.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2019 07:06 AM
@Bernard.Huang This is a good post on kernel extension whitelisting
They're similar in that users have to explicitly approve access to enable them (or an admin with an MDM can whitelist), but they have separate profile payloads. Kernel extension approval is for a (hopefully) rare type of app that requires some process to work at the kernel level of the OS, so things like antivirus, virtualization, or other security apps. PPPC is going to be more common in that any app that wants to access data from another app, or user data like photos will get a permission prompt.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2019 05:22 PM
Wow, my mind is blown! Thanks @sdagley & @sshort You guys make me look like a complete amateur. And in a good way, I am learning a lot.
I shall get this whitelisting started.
This is a good post on kernel extension whitelisting really is a great article.
Wish me luck in getting all the kernel extensions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2019 06:11 PM
Hi all,
Just find out how to find out all Kernel Extensions and their team Identifiers.
This is from page
https://technology.siprep.org/getting-the-team-id-of-kernel-extensions-in-macos-10-13-and-higher/
So the line is
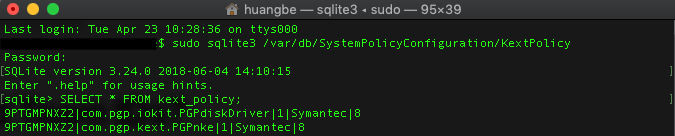
sudo sqlite3 /var/db/SystemPolicyConfiguration/KextPolicy
SELECT * FROM kext_policy; Here's an example of the output I got
Sorry to have taken the focus away from PPPC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-14-2019 08:20 AM
Hey,
Just wondering whether anyone has had success with Adobe After Effects? I'm trying to pre-approve its access to control Finder but it's not working. I noticed that when I run codesign on the After Effects app, the output from the 'designated =>' field has no bundleID in it. All the other pre-approvals in my config profile have a bundleID listed in the code requirement field and they work perfectly. Am I missing something?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
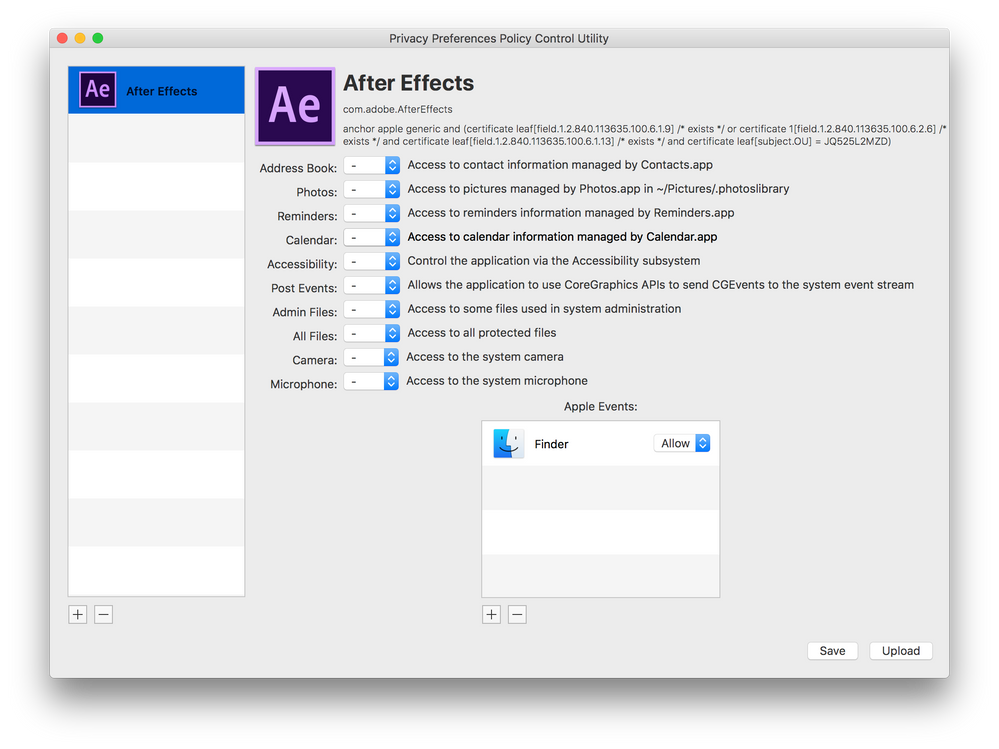
Posted on 08-14-2019 08:43 AM
I was able to solve the After Effects approval by using the Privacy Preferences Policy Control Unit App to build out the PPPC.
In the Apple Events section, click the add button and select Finder.
Bonus: If you are deploying Wacom drivers, you need to allow the tablet in Illustrator. To do that, select Apple Events, add button, Other. navigate to /Library/Application Support/Tablet/WacomTabletDriver.app.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-14-2019 11:25 AM
Years ago I stopped trying to ‘fix’ the changes Apple makes to the UX. Educating the users is going to be easier in most cases (scroll wheel direction, dock location, etc). Yeah, there are still things that we try and manage, but less and less each OS release. 😕
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-19-2019 09:34 AM
@mscheffler where you able to figure out how to allow the NWEA Testing Browser?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-19-2019 09:59 AM
@dsweigart Our tech guy at the high school was able to get it working, but we're not fully compliant with all of NWEA's wishful thinking on things they want disabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-23-2019 12:35 PM
@SCADtom Love the "bonus" tip.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-13-2020 01:44 PM
I am experiencing challenges with this and the following apps:
Zoom
VirtualBox
PPPC is new to me and I don't even know where to start.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2020 01:42 AM - edited 07-23-2021 10:07 AM
I can confirm @SCADtom Method working on 10.15.X.
May I add the following:
Make sure you build the PPPC Profile with the same Adobe Package(s) you are creating/uploading from the Adobe Admin Console.
Manually Creating PPPC Configuration Profiles:
As noted by @bernard.Huang codesign -dr - /path/to/app will help with creating PPPC Profiles manually on Jamf if not using the PPPC Utility to automate the tasks.
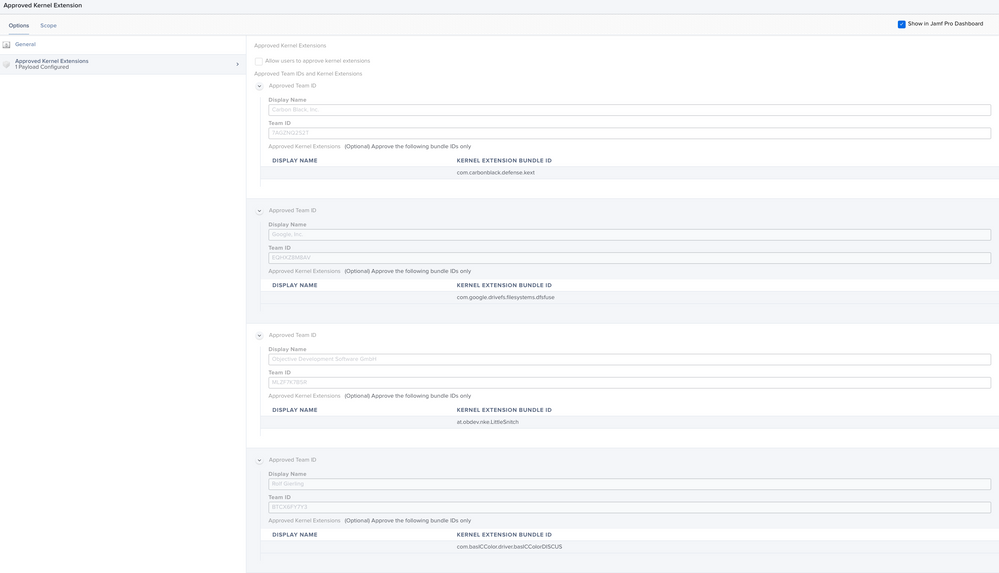
Kext Configuration Profiles:
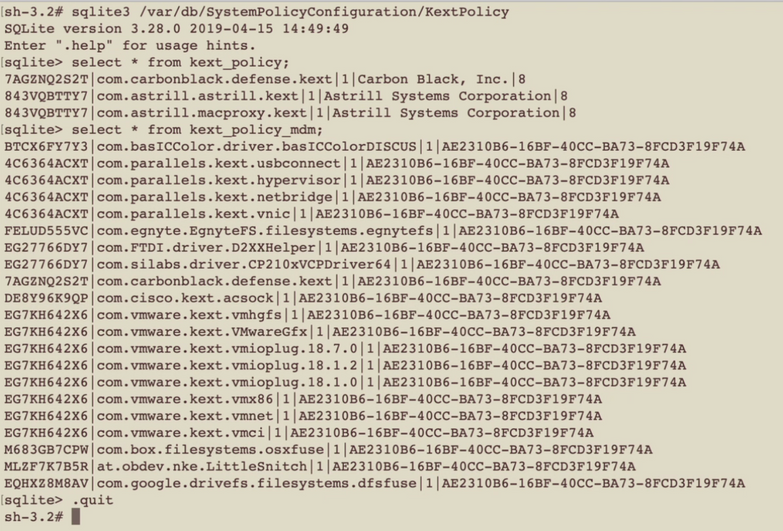
Keep in mind that Kext(Kernel extensions) are different than PPPC configuration profile. To verify kernel extensions, run this to look at the KextPolicy database on your system:
sqlite3 /var/db/SystemPolicyConfiguration/KextPolicy
To view approved KEXTs in the sqlite3 database:
SELECT * FROM kext_policy;
This should show what KEXTs have been approved on your Mac. You can proceed to enter Team Bundle/ID on Jamf.
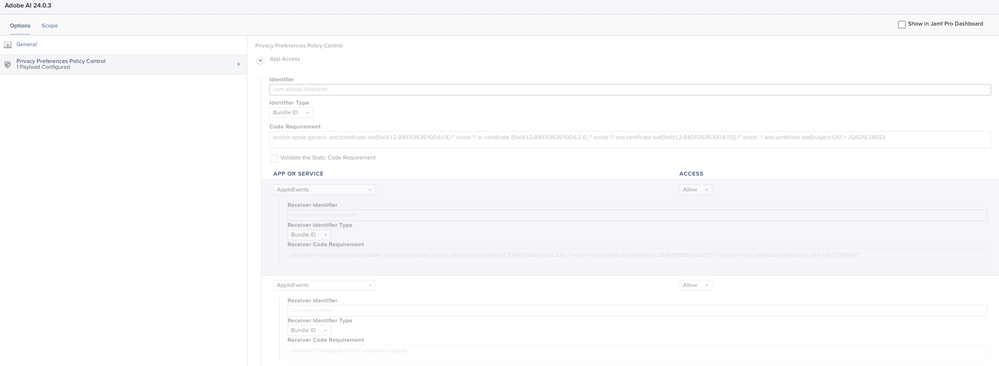
I recommend creating a profile for each application and I know this sounds like a lot of work but this will make it easier for future management and explicit for when troubleshooting or making changes.. Make sure to append the version of the Adobe package after just in case you are running different versions or have to service multiple versions in the future for scoping. I have attached a few examples.
Hope this helps anyone having issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
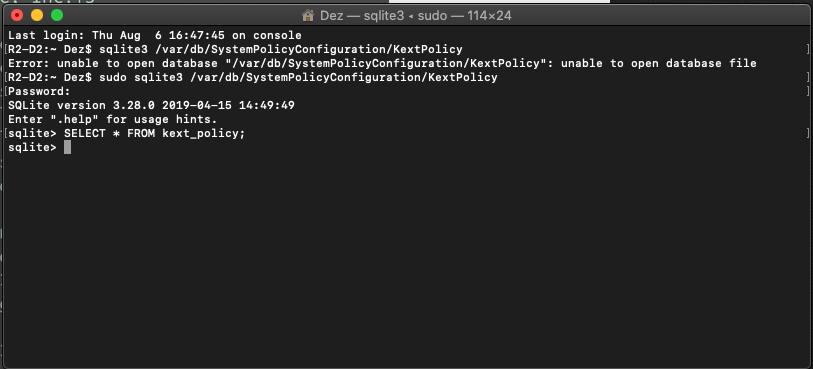
Posted on 08-06-2020 01:53 PM
I tried that command in Terminal @MikeyJAP and this is what I got, any ideas? This is on my VM as well as my Macbook.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2020 05:13 PM
Try SELECT * from kext_policy_mdm;.
https://donmontalvo.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2021 02:59 PM
Thanks @donmontalvo , the kext_policy_mdm; will work with BigSur.