Greetings.
My Company use JAMF Pro to manage our macbooks and they had policy that user must have admin access because most of them are Programmer and they must had full capability to their macbooks.
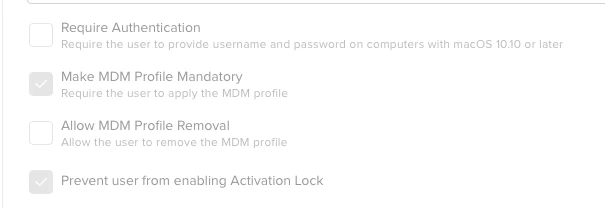
One day i found that if i delete MDM Profiles, i cannot restore it again unless i re enroll the laptop to JAMF. i already implement self heal script, but it doesn't work because JAMF binary still there and i still can use the command.
My friend suggesting for restriction access to "Profiles", but it can't help since our users must have access to this menu for testing or allowing their mobileconfig.
Is there any possibility to restore deleted MDM profiles automatically or prevent it to be delete withouth restricting Profiles Menu?