- Jamf Nation Community
- Products
- Jamf Pro
- Prevent or Restore MDM Profile Removal
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Prevent or Restore MDM Profile Removal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-27-2021 10:29 PM
Greetings.
My Company use JAMF Pro to manage our macbooks and they had policy that user must have admin access because most of them are Programmer and they must had full capability to their macbooks.
One day i found that if i delete MDM Profiles, i cannot restore it again unless i re enroll the laptop to JAMF. i already implement self heal script, but it doesn't work because JAMF binary still there and i still can use the command.
My friend suggesting for restriction access to "Profiles", but it can't help since our users must have access to this menu for testing or allowing their mobileconfig.
Is there any possibility to restore deleted MDM profiles automatically or prevent it to be delete withouth restricting Profiles Menu?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-28-2021 05:54 AM
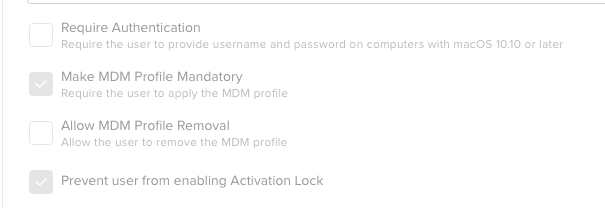
In your prestige enrollment, you will want to un check the box to prevent removal of the MDM profile. This will prevent even admins from removing it through the profiles pane in System Preferences.
This will not prevent admins from being able to run the commands in terminal to remove the MDM framework all together though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2021 05:58 AM - edited 07-28-2021 07:56 AM
I believe you are asking how to limit access to the Profile system preferences pane. This is doable, but a better option would be to make certain of your MDM profiles not-removable. However, this requires your Macs to be supervised and enrolled in Apple's DEP (Apple Business Manager). Do you know if you have ABM (and DEP) set up?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2021 06:47 AM - edited 07-28-2021 06:48 AM
@galihrengga if your users weren't enrolled via ADE, I created a script to limit admin user "sudo" permissions. This will prevent them from running commands like "sudo jamf removeMDMProfile" and "sudo jamf removeFramework". This also works on machines enrolled via ADE. (But I'm assuming that the settings @nelsoni mentioned above would be in place.)
#!/bin/bash
# Identify the username of the logged-in user
currentUser=`python -c 'from SystemConfiguration import SCDynamicStoreCopyConsoleUser; import sys; username = (SCDynamicStoreCopyConsoleUser(None, None, None) or [None])[0]; username = [username,""][username in [u"loginwindow", None, u""]]; sys.stdout.write(username + "\n");'`
# Create file named "standard" and place in /private/tmp/
touch /private/tmp/standard
# Populate "standard" file with desired permissions
echo "$currentUser ALL= (ALL) ALL
$currentUser ALL= !/usr/bin/passwd root, !/usr/bin/defaults, !/usr/sbin/visudo, !/usr/bin/vi /etc/sudoers, !/usr/bin/vi /private/etc/sudoers, !/usr/bin/sudo -e /etc/sudoers, !/usr/bin/sudo -e /private/etc/sudoers, !/usr/local/bin/jamf" >> /private/tmp/standard
# Move "standard" file to /etc/sudoers.d
mv /private/tmp/standard /etc/sudoers.d
# Change permissions for "standard" file
chmod 644 /etc/sudoers.d/standard
exit 0; ## Sucess
exit 1; ## Failure
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-19-2023 11:37 PM
https://github.com/mani2care/JAMF-Script/blob/main/Sudo_JAMF_removeframework_Restruction.sh
As you suggested i tried like this its works like normal admin users not the root user & when i use the sudo su and still i can able to run the removeframework also mdm profile still i can able to remove it manually. any other way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2021 11:50 AM - edited 07-28-2021 11:53 AM
If they are all admins they should have sudo access also. I don't think there is a way to restrict the JAMF terminal commands. If someone knows the JAMF removemdmprofile command there is not really anything you can do to stop them from removing the MDM profile as far as I am aware without messing with sudoers.
May want to consider managing suders as @bwoods suggested. Caution on removing your ability to run the sudo jamf removemdmprofile command incase you ever need to troubleshoot a device. may also want to restrict jamf removeFramework while you are at it. Be very careful messing with sudoers and only use visudo to modify sudoers or sudoers.d. Its best to mess with suders.d rather than sudoers itself.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2021 07:01 PM - edited 07-28-2021 07:11 PM
The script above only manages sudoers.d by the way. It also only affects the logged in user. If you have an IT account, you can continue running jamf binary commands with it. If you want to revert the changes made, simply run the script below.
#!/bin/bash
rm /etc/sudoers.d/standard
exit 0; ## Sucess
exit 1; ## Failure