- Jamf Nation Community
- Products
- Jamf Pro
- Pulse Secure 5.2.5 (Build 869) Deployment with Pul...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
07-05-2017
11:22 AM
- last edited
a month ago
by
![]() kh-richa_mig
kh-richa_mig
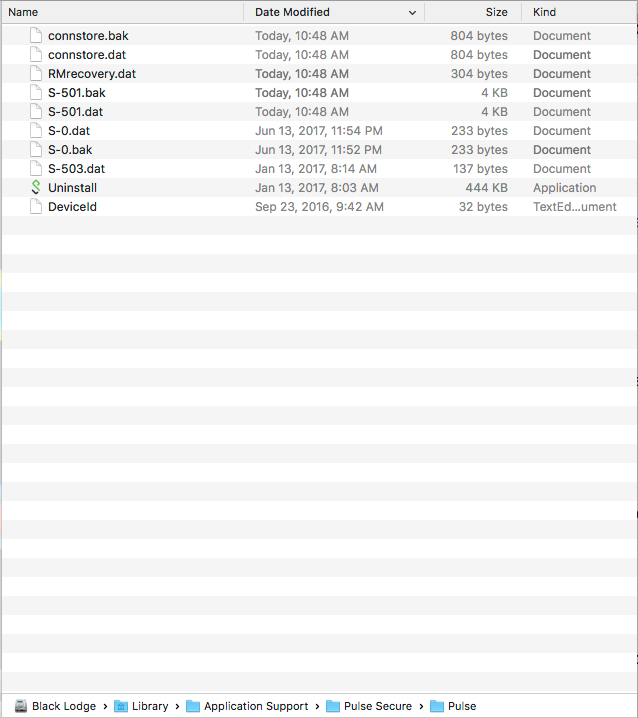
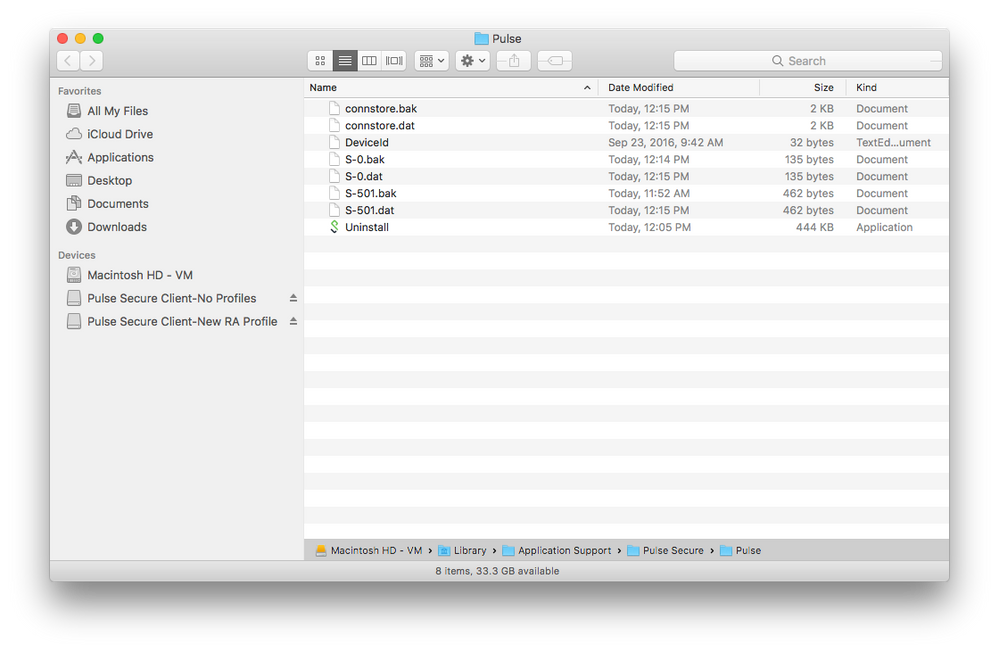
Greetings, all! In the past, I've used Composer to package Pulse Secure releases which would also contain the necessary connection profiles built-in. I am now in need of deploying Pulse Secure App Launcher to each macOS device for an upcoming MFA-related project. I looked in /Library/Application Support/Pulse Secure/Pulse/ and found the following files.
Since users will already have a working instance of Pulse Secure, there's no need to push more over the network and have the same version re-installed. I would instead just like to modify their connection profiles and wipe these clean or simply include one specific one needed going forward. What are some of your thoughts on the various approaches that could be used here?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2017 12:34 PM
I think I've figured this out! I created two DMG files using Composer: one without any connection profiles and another with a new connection profile. Using a test virtual machine, I deployed a current build of Pulse Secure 5.2.5 (Build 869) which has two connection profiles.
Test #1: Two Connection Profiles
Step 1. To verify that the installation was successful, I loaded the LaunchDaemon, opened the Pulse Secure.app and confirmed that the two packaged connection profiles were present.
sudo launchctl load /Library/LaunchDaemons/net.pulsesecure.AccessService.plistsudo open -a /Applications/Pulse Secure.app/
Test #2: No Connection Profiles
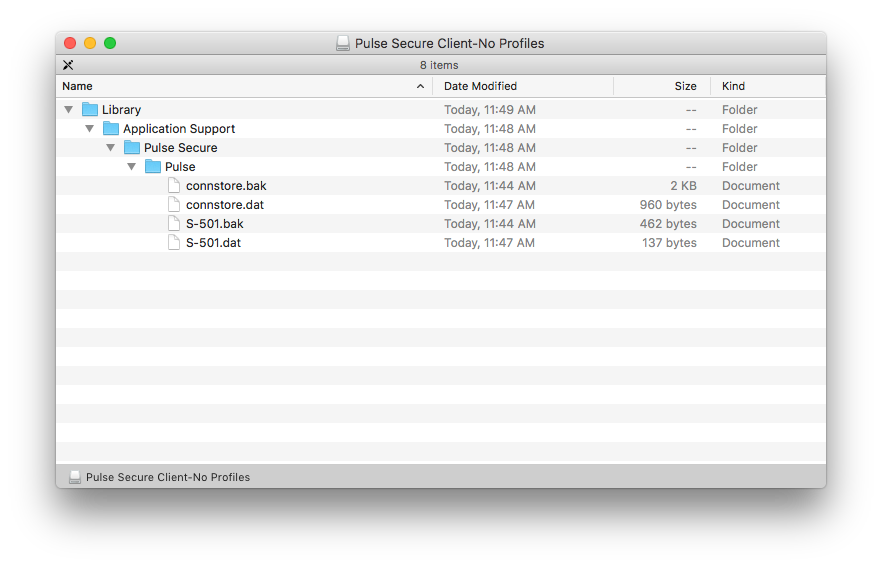
Step 1. Once the initial installation with two connection profiles was verified, I opened the Pulse Secure Client-No Profiles.dmg, copied the files in the ~/Library/Application Support/Pulse Secure/Pulse/ directory and copied them to the corresponding location, locally, overwriting the existing files.
Step 2. To verify that the copying was successful, I unloaded and then re-loaded the LaunchDaemon, opened the Pulse Secure.app and confirmed that the two packaged connection profiles were present.
sudo launchctl unload /Library/LaunchDaemons/net.pulsesecure.AccessService.plistsudo launchctl load /Library/LaunchDaemons/net.pulsesecure.AccessService.plistsudo open -a /Applications/Pulse Secure.app/
Test #3: New Connection Profiles
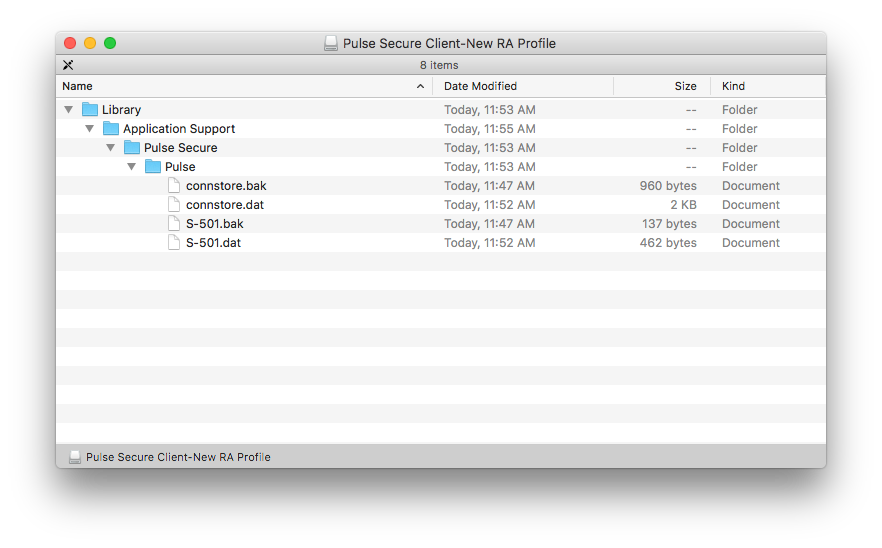
Same as above in Test #2 but referencing the Pulse Secure Client-New RA Profile.dmg containing the new connection profile.
Since these above steps simply deal with local, non-Jamf based deployments, I will report back with a scalable enterprise solution using Jamf Pro :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-13-2017 10:39 PM
Eh, so things changed on my end and while we ended up going with no stored connection profiles (users populate this themselves through a web-interface) stored with the deployment, the packaging of the profile using Composer worked the best. The aforementioned script of unloading and loading the LaucnhDaemon was also key if anyone is looking to implement this within their own environments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2017 12:34 PM
I think I've figured this out! I created two DMG files using Composer: one without any connection profiles and another with a new connection profile. Using a test virtual machine, I deployed a current build of Pulse Secure 5.2.5 (Build 869) which has two connection profiles.
Test #1: Two Connection Profiles
Step 1. To verify that the installation was successful, I loaded the LaunchDaemon, opened the Pulse Secure.app and confirmed that the two packaged connection profiles were present.
sudo launchctl load /Library/LaunchDaemons/net.pulsesecure.AccessService.plistsudo open -a /Applications/Pulse Secure.app/
Test #2: No Connection Profiles
Step 1. Once the initial installation with two connection profiles was verified, I opened the Pulse Secure Client-No Profiles.dmg, copied the files in the ~/Library/Application Support/Pulse Secure/Pulse/ directory and copied them to the corresponding location, locally, overwriting the existing files.
Step 2. To verify that the copying was successful, I unloaded and then re-loaded the LaunchDaemon, opened the Pulse Secure.app and confirmed that the two packaged connection profiles were present.
sudo launchctl unload /Library/LaunchDaemons/net.pulsesecure.AccessService.plistsudo launchctl load /Library/LaunchDaemons/net.pulsesecure.AccessService.plistsudo open -a /Applications/Pulse Secure.app/
Test #3: New Connection Profiles
Same as above in Test #2 but referencing the Pulse Secure Client-New RA Profile.dmg containing the new connection profile.
Since these above steps simply deal with local, non-Jamf based deployments, I will report back with a scalable enterprise solution using Jamf Pro :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2017 12:55 PM
I've tried to copy those connection files on Windows for Pulse Secure and ran into problems with the pulse secure client creating a machine-based guid within the connection settings. What ended up happening was that when multiple users received laptops with the common connection files, users would find themselves being bumped off of VPN continually because the VPN controller was seeing it as multiple instances of the same machine, or something like that. Something to keep an eye out for since it may work the same way for Macs... the connection files are very similar between the two, comparing them side by side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2017 01:18 PM
@ndeal Agreed! I will be testing this thoroughly with some folks before an enterprise-wide deployment.
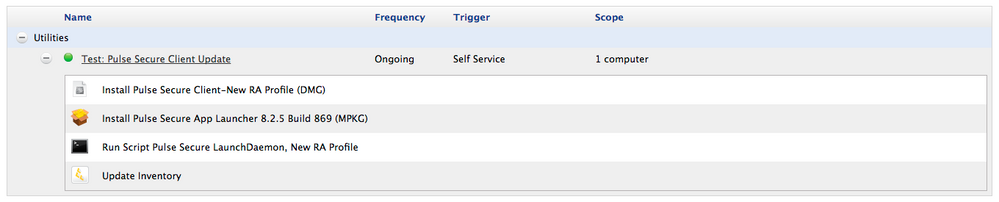
I've added a script (see below, nothing fancy) that handles the unloading, loading and opening of Pulse Secure after the DMG and App Launcher packages have been installed. Here's a screen capture of the policy as it stands in our Jamf Pro instance.
#!/bin/sh
launchctl unload /Library/LaunchDaemons/net.pulsesecure.AccessService.plist
launchctl load /Library/LaunchDaemons/net.pulsesecure.AccessService.plist
open -a /Applications/Pulse Secure.app/
open -a "/Library/Application Support/Pulse Secure/PulseApplicationLauncher.app"
exit 0- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2017 01:27 PM
Nice. Do you mind if I ask what MFA solution you're implementing/testing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2017 01:31 PM
@ndeal Unfortunately, I am unable to disclose that! In terms of the above workflow, the MFA that we're going with doesn't really impact the system administration side of things. Our infrastructure folks are handling the majority of the MFA piece :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2017 01:32 PM
Got it, no worries!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-06-2017 02:36 AM
Have you seen this thread?
Using "jamcommand" to import your connections might be a cleaner solution to this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-06-2017 06:56 AM
@Chris Thanks for the link! I did read over that but don't have a .jnprpreconfig file to work off of. After combing through the provided thread, it appears that it is just a basic text file with the connection profile details used by an organization. Would you (or anyone else, really!) be willing to share a sample of what this .jnprpreconfig looks like?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-06-2017 11:53 AM
We currently use an AutoPKG recipe to build a payload-free Pulse Secure installer. The pkg-wrapped DMG that you download from the licensing center is unpacked, added to a package root and the following postinstall script runs:
#!/bin/bash
# Install Pulse Secure
/usr/sbin/installer -dumplog -verbose -pkg PulseSecure.pkg -target /
#
# Applying VPN configuration file
"/Applications/Pulse Secure.app/Contents/Plugins/JamUI/jamCommand" -ImportFile "vpn.pulsepreconfig"
exit 0Here is the jnprconfig we use. I believe some of the variables came from a jnpr export on the MAG and/or a generated conn.dat file on a test box. Hope this helps.
schema version {
version: "1"
}
machine settings {
version: "8"
guid: "aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa"
connection-source: "preconfig"
server-id: "AAAAAAAAAAAAAAAAA"
}
ive "aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa" {
friendly-name: "VPN"
version: "5"
guid: "aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa"
server-id: "AAAAAAAAAAAAAAAAA"
connection-source: "preconfig"
factory-default: "true"
uri: "https://vpn.domain.net"
connection-identity: "user"
connection-policy: "manual"
}- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-06-2017 01:54 PM
Awesome, thanks @mrben! I believe the connstore.dat file located in the /Library/Application Support/Pulse Secure/Pulse/ directory needs to be modified and then the launch daemon unloaded/re-loaded. This appears to work fine on my test box (virtual machine) but I am curious what effect this would have on a larger deployment. Obviously, I'll test this myself before a production scaled deployment but I was wondering what your experience has been with populating that connstore.dat with default values. I did notice that when the launch daemon is re-loaded, that those values in the .dat file become machine-specific and are no longer defaults originally specified in the the below section. So perhaps the concern over the generic default values is a non-issue. Wondering what your thoughts are on this.
schema version {
version: "1"
}
machine settings {
version: "23"
guid: "aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa"
connection-source: "preconfig"
server-id: "AAAAAAAAAAAAAAAAA"
}
ive "aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa" {
friendly-name: "<ProfileName>"
version: "12"
guid: "aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa"
server-id: "AAAAAAAAAAAAAAAAA"
connection-source: "preconfig"
factory-default: "true"
uri: "<CompanyLink>"
connection-identity: "user"
connection-policy: "manual"
}FWIW the friendly-name and uri fields are the two that are specific to our organization and the ones that have, in turn, been modified to work in our environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-13-2017 10:39 PM
Eh, so things changed on my end and while we ended up going with no stored connection profiles (users populate this themselves through a web-interface) stored with the deployment, the packaging of the profile using Composer worked the best. The aforementioned script of unloading and loading the LaucnhDaemon was also key if anyone is looking to implement this within their own environments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-14-2018 02:38 PM
Question is it possible to import a jnprconfig that lists multiple urls? I have success with one but not two.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2018 02:29 PM
@sepiemoini
DNS Enries are overriding or not coming to client mac machine when connecting to pulse secure
Posted: Less than a minute ago by rastogisagar
It seems when we are trying to connect Pulse Secure VPN to JAMF Enrolled MACBOOK , there we are not getting DNS server entries, we checked in local client machine DNS entries where we can see local ISP provided DNS server enrtries . Any idea why its overriding or do Pulse secure need to do something. Right now I have just push Pulse secure agent via jamf policy. Do i need to so something more
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2018 03:17 PM
@ndeal our pulse secure have to do the configurations for pulse secure VPN be compliant to JAMF MDM.
They are asking for server url and viewer url. I know about server url but i am not aware about viewer url. Any idea please