- Jamf Nation Community
- Products
- Jamf Pro
- Re: RADIUS Deployment failing miserably
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RADIUS Deployment failing miserably
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
09-27-2016
01:27 PM
- last edited
3 weeks ago
by
![]() kh-richa_mig
kh-richa_mig
Does anyone have a script or can anyone point me in the correct direction for scripting a way to remove a ton of duplicate certs from my machines?
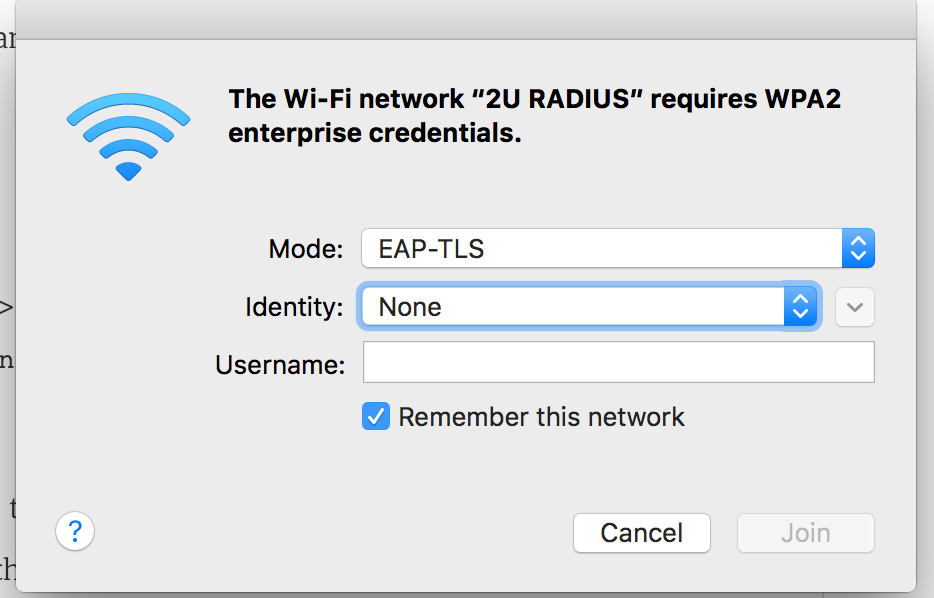
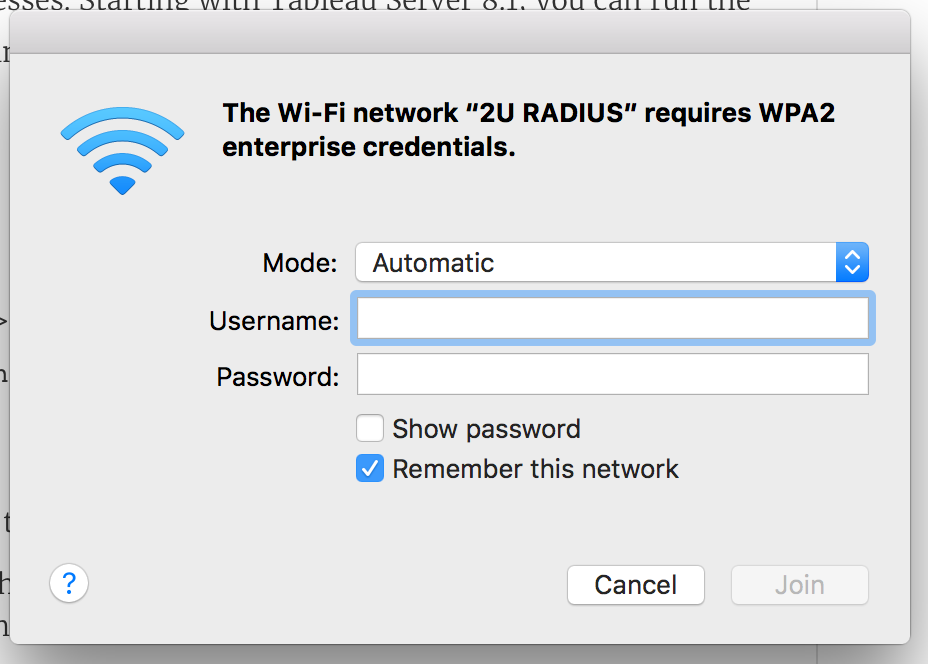
Deploying RADIUS has caused me a real headache, and somehow a bunch of my machines pulled a new cert every single time the configuration profile was modified or redeployed. Now, my machines are confused? They prompt the user to enter a username/password or to choose which cert to use when connecting to our RADIUS SSID. I believe this is being caused by the many duplicates, though I may be (probably) wrong.
Does anyone have experience with this?
I'd greatly appreciate anyone's input on this.
- Labels:
-
Jamf Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-27-2016 02:30 PM
The answer here lies in the security utility, which lets you manipulate the user's keychain and certificates contained therein. However, this is difficult, as the keychain needs to be unlocked or you need the user's password. That's not always feasible.
Practically, there's probably an easier solution here. Are you handing out the SCEP or AD Cert instructions in a configuration profile? If so, are you also handing out the WiFi settings in the same profile, or a separate one? If you send both in the same profile, you can explicitly tell the WiFi settings to use the certificate received from the SCEP request for authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-03-2016 01:56 PM
@kilodelta We are handing out the AD cert instructions in a configuration profile. So you're saying that putting out two configuration profiles, one for Wifi settings, and one for the cert instructions, could potentially resolve the issue that I'm experiencing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-03-2016 02:05 PM
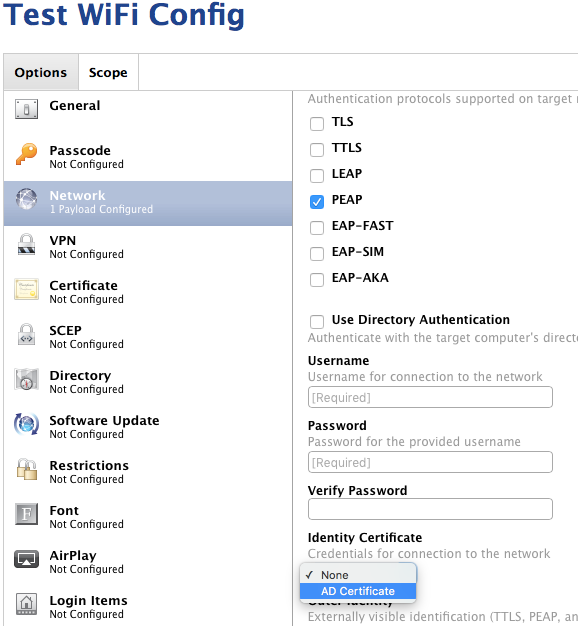
Yes, but the opposite of what you said - put them in the same profile. When you have both a certificate and a WiFi payload, and you choose a WPA2 Enterprise EAP type that supports certificates, you'll see an "Identity Certificate" drop down with the option of "AD Certificate". Selecting that will tell the Mac to use the certificate it requests to authenticate to the WiFi network.
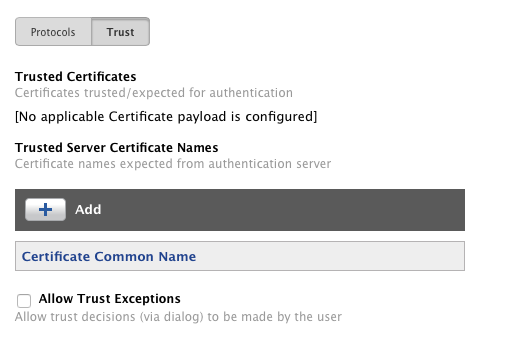
In a similar vein, be sure you configure upload the entire certificate trust chain for your RADIUS server under the trust tab. Failure to do so can cause clients to be prompted to trust the RADIUS server, even if the certificates it's using are otherwise explicitly trusted on the system.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-03-2016 02:28 PM
Yeah, they basically need to be in the same profile for the OS to automatically create an "identity" that links the certificate to the wireless configuration. You can use the security command as mentioned above to create an identity, but it's not a great option and can be finicky.