- Jamf Nation Community
- Products
- Jamf Pro
- Re: Renew Certificates
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Renew Certificates
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-15-2022 11:15 AM
Hey all,
Not sure if this is the correct place to post this but here we go:
Long story short - I'm new to Jamf (actually our whole company is).
Now we are trying to renew the "client certificate(?)" because employee's are losing connection to the VPN due to the cert being expired. Eventually this will become an issue for our employee's in other countries as they cannot come into the office to retreive a new one. At the moment it's only valid for a year (if that gives you an idea what I'm talking about)
I've seen a lot of people mentioning this issue but I haven't found a solution yet. We are in an on-prem environment using ADCS with Jamf. Feels like there should be a way to automate this? Is our configuration wrong somehow? Not sure why the Mac's are able to retreive these without issues when enrolling them but not renew them? Every suggestion on where to look are highly appreciated!
I would also like to mention that i'm not familiar with everything so please be patient with me if I'm using the incorrect terms to describe things - I'm simply asking because I want to learn and make life easier for our employee's (I'm not even in the infrastructure team)
Best regards,
Bullen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-15-2022 11:35 AM
The configuration profile that installs the certificate should renew just before a year is up. The exact time before it expires when it renews is up to your configuration, its a setting. This should update the certificate also. MacOS will notify the user before the configuration profile expires if it has not renewed for some reason.
If you have one of those people that insists on micro managing, you can change anything in the configuration profile and tell it to reinstall to all devices. I would not recommend doing this, but there are those people out there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-16-2022 09:48 AM
Hey!
Thanks for your reply.
I'm a bit confused as I don't understand all the magic behind the scene here. I'm told this was done by a consultancy firm and therefore we are lacking in knowledge internally.
The AD certificate is set to renew itself which i think is working just fine. However I have 2 certificates deployed within the same confprofile and one of them is in return after being deployed, creating another entry(certificate) in the keychain identified as the hostname of the device and therefore you have me, calling it a client certificate (part of a certchain perhaps?). As I said i'm not very familiar with certs and how the operate.
From what I understand this client certificate generated by those in the confprofile is used to access the wi-fi in the office together with using the vpn from home and once expired (valid for a year) they can't do any of it.
The only fix we have for it now from what I know is have them come into the office - jack their computer to our network and run the confprofile from self service to retreive a new one.
If you have a lot of knowledge in the area I would appreciate if you could break it down for me quickly with a few rows.
Best wishes,
Bullen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-16-2022 10:16 AM
I forgot one thing, my bad.
If you say this is a setting and that it should renew it, where would that setting be? Are we missing anything in our config?
If the client certificate doesn't renew, what could be the issue, any idea? I can only see renew certificate under the AD certificate section together with the amount of days before notifications should start popping up. (making the conclusion we are talking about the same thing here).
The certificate that issues this client certificate im talking about is under the Certificate only section and from what I remember there is nothing there about renewal. I've been brainstorming a bit and was wondering if this has something to do with Mac/Keychain.
I'm simply doing this for my own development and interest and I understand it might be impossible without knowing the environment to give me an answer. Luckily we are not that many Mac users yet and will most likely bring in the necessary knowledge soon. But it would be interesting to know the answer that's for sure.
Best wishes,
Bullen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-16-2022 01:44 PM
Not a good position to be in. Your company is using a consulting firm to set things up rather than maintaining knowledge by employing a Mac Admin. It makes things fun when stuff hits the fan. Let’s see what we can figure out.
The AD Certificate payload uses a CSR, and issues a certificate against whatever template it’s told to use. The certificates will renew with a new CSR 14 days before the certificate expires. It sounds like this is what you are seeing so all is well.
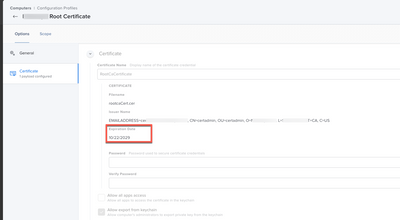
As far as the “Certificate” payload, that is a bit different. You would upload a .cer to JAMF to populate that payload. When JAMF deploys the configuration profile, it literally “copy pastes” the certificate it was given without changing any information including the expiration date. When its time to update a certificate deployed this way. Whoever manages that certificate needs to do the CSR stuff to get a new certificate and give it to you to upload in to JAMF. Once to upload the new certificate in to JAMF, you should see the option to redeploy the configuration profile which will update it on all Macs.
This is an example of a certificate we are deploying. If I need to update the expiration date which is off in 2029, I would need a new copy of the certificate to upload to JAMF. I don’t have access to get this certificate, it comes off of one of our app servers so that app support team would need to give me a new copy. I would edit this configuration profile, remove this certificate and upload the new one. Then tell JAMF to broadcast it. Doing this in a rollout is best, but that is for another time.
I am doing a bit of assuming on you using the certificate payload.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-17-2022 09:11 AM
Hey again,
I think I'm starting to get a hold this to some degree. Thank you for taking your time!
Today I was with a member from the infrastructure team and asked him to check the cert server.
It turns out that the template we use "issues a certificate against whatever template it’s told to use" didn't allow autoenroll neither did it allow read access.
Do you know what permissions should be checked on the template for it to speak properly with Jamf? We allowed both autoenroll and read now so hopefully the issue is fixed.
I have about 5 macs that are within the threshold (14 days) so hopefully i'll have an answer by tomorrow.
Also, is 14 days recommended?
I will post an update once i've been able to confirm if it's working or not, for any future noobies (like myself) encountering this issue.
Best wishes,
Bullen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-04-2023 02:00 AM
To ensure that the certificate server can issue certificates to Macs managed by Jamf, the certificate template used to issue the certificates should have the "Autoenroll" permission enabled. Additionally, the Jamf server and the Macs themselves should have read access to the certificate template in order to retrieve the certificates.
As for the 14-day threshold, it is a common practice to renew certificates well before their expiration date to avoid any potential disruptions in service. However, the exact threshold can vary depending on the organization's needs and policies. A 14-day threshold is a good starting point, but you can adjust it as needed based on your specific use case.
It is also important to note that some certificate authorities (CAs) may have different requirements and limitations for certificate renewals. It is recommended to consult the CA's documentation for specific requirements and best practices.