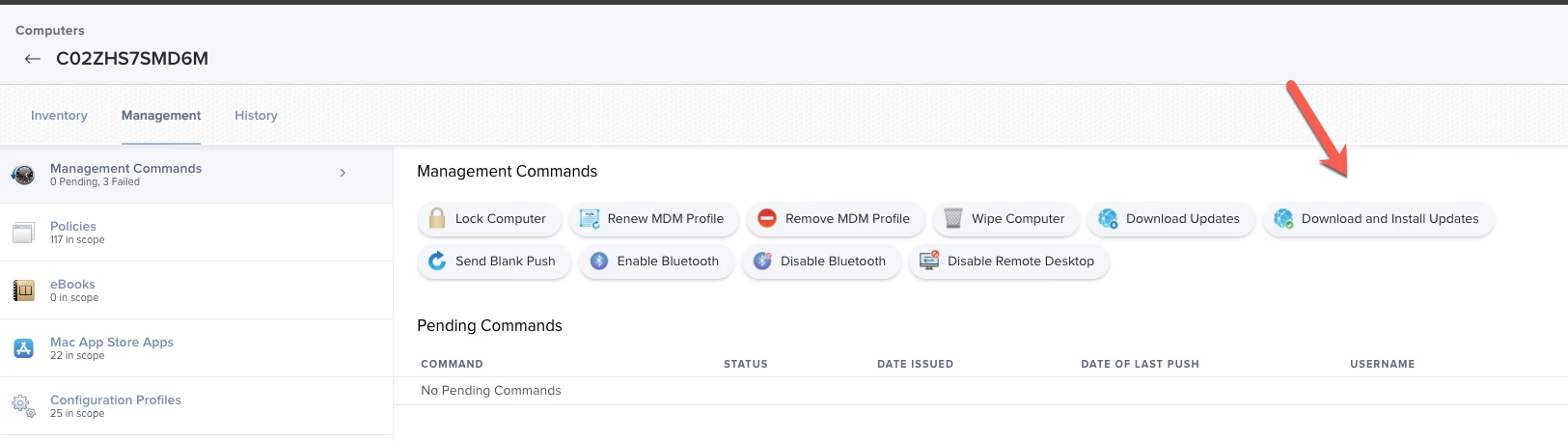
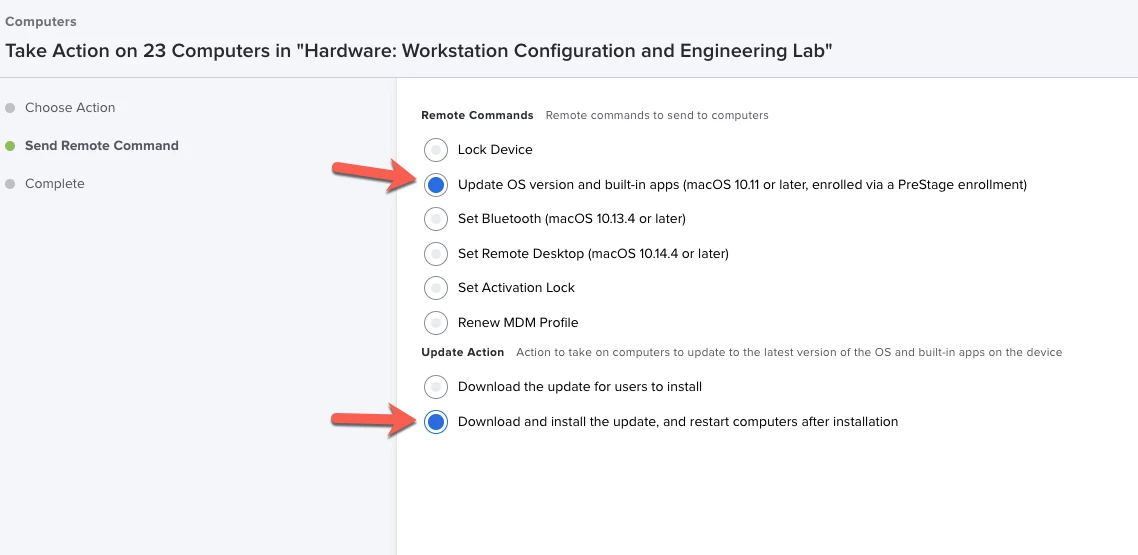
Can someone please share what process they are using for Apple Software Monthly Updates via Policy for Big Sur Security Updates. I am not able to do via two Payloads:
- Software Updates pointing to Apple Software Update server
or
- Files and Processes
- Execute Command
- softwareupdate -i -a -R
- Execute Command
So how is anyone getting Apple Security updates to their Macs? I have hundreds of devices and most are in labs so user intervention is not happening.