We are having an issue with Secure Tokens.
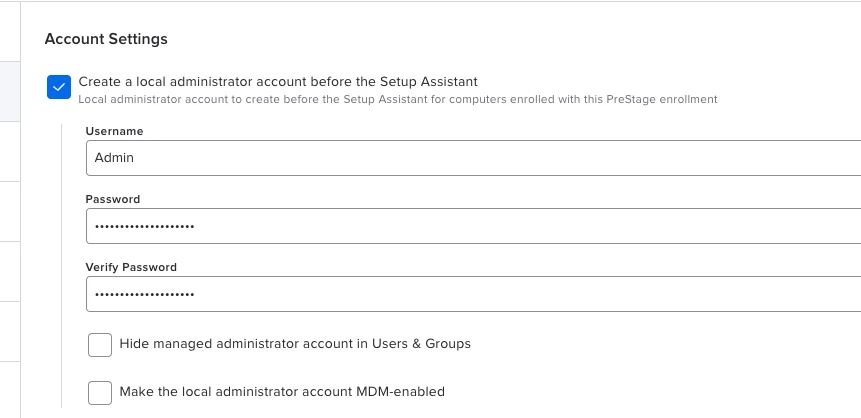
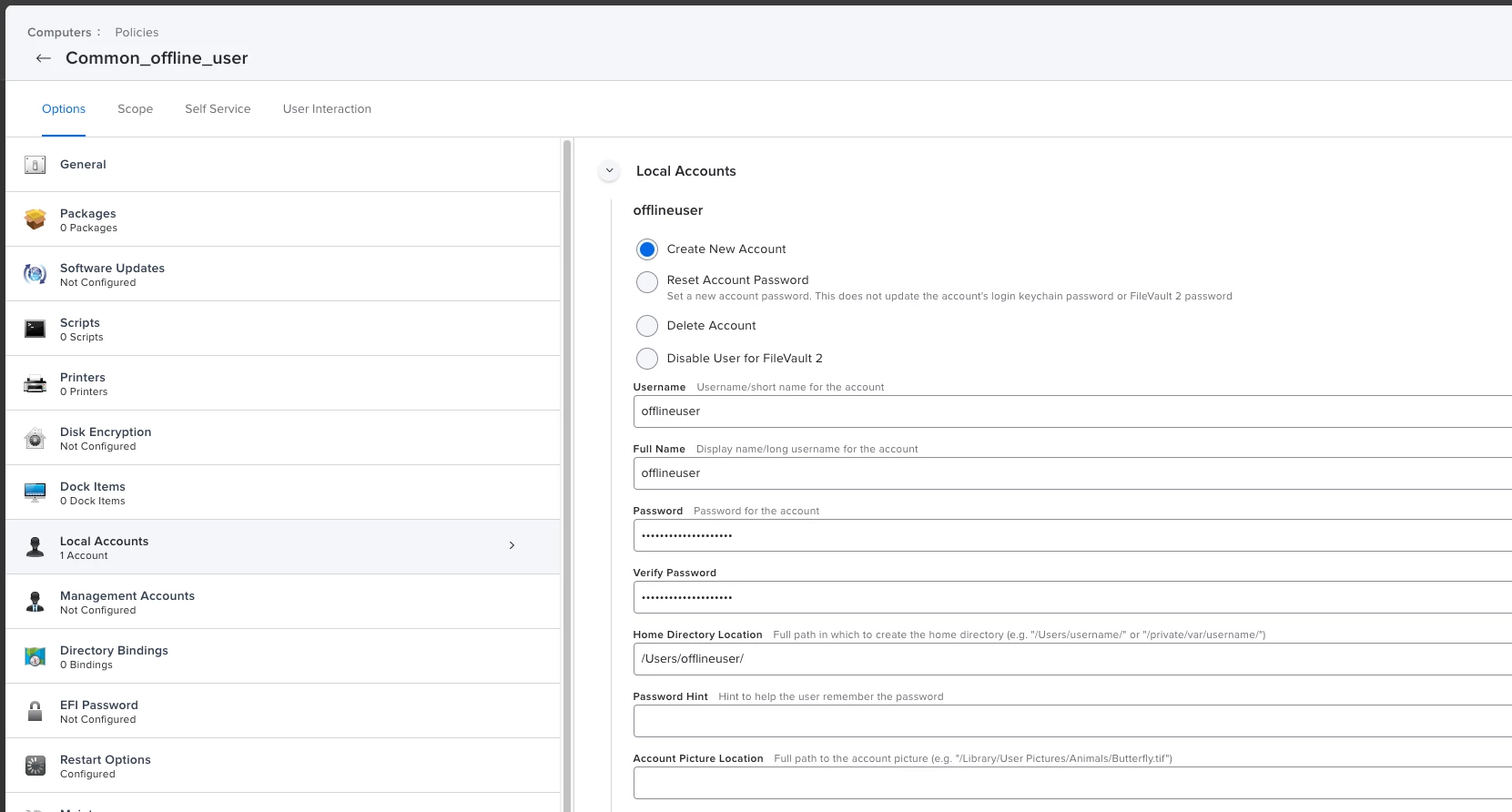
JAMF creates an admin account by default, which is created before setup assistant and almost always the fist account we log into. From my understanding, the fist logged in account is the one that gets the secure token. However, in many case (not always) a generic standard account we push through policy is the one that gets the token. This causes issues with running updates and changing passwords. I am able to resolve it through a series of terminal commands but wondering what is causing in the first place. I originally thought it was an issue with Catalina but am still seeing it currently with Ventura.