Good Morning jamf Nation,
We are rolling out SentinelOne agent to Macs. I have the policy set, but I need some assistance with "pre-approving" the SentinelOne Agent kernel extension. The S1 setup guide gives a parameter to enter in the policy:
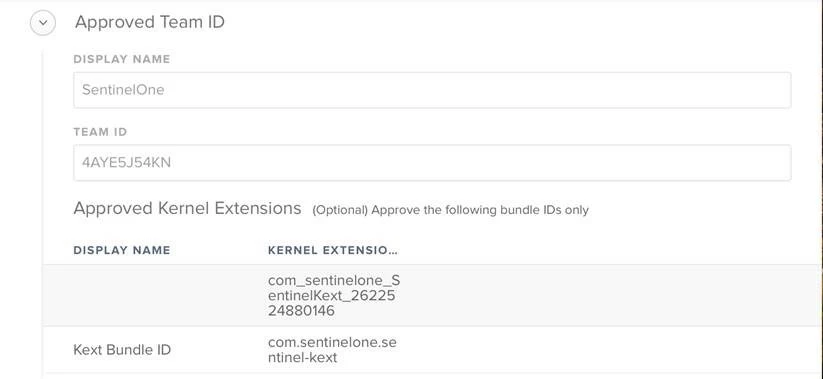
Kext Bundle ID: com.sentinelone.sentinel-kext
Developer ID: 4AYE5J54KN
I just don't know where to put the parameter. I tried copying and pasting it into Execute Command under Files and Processes, but that change doesn't 'approve' the agent. Based on the log file, it looks like it's trying to run the parameter, but then fails?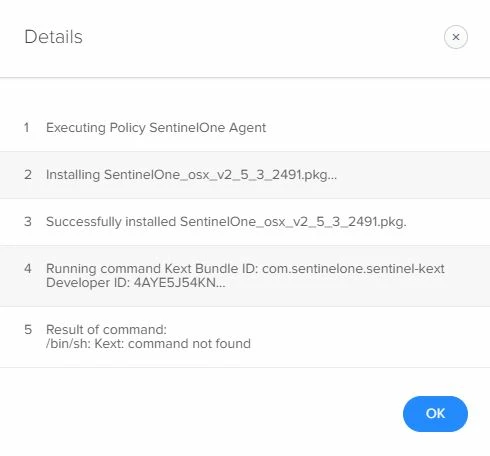
Any ideas?