- Jamf Nation Community
- Products
- Jamf Pro
- Re: SEP 14.3 network filter blocking VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SEP 14.3 network filter blocking VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-17-2021 07:42 PM
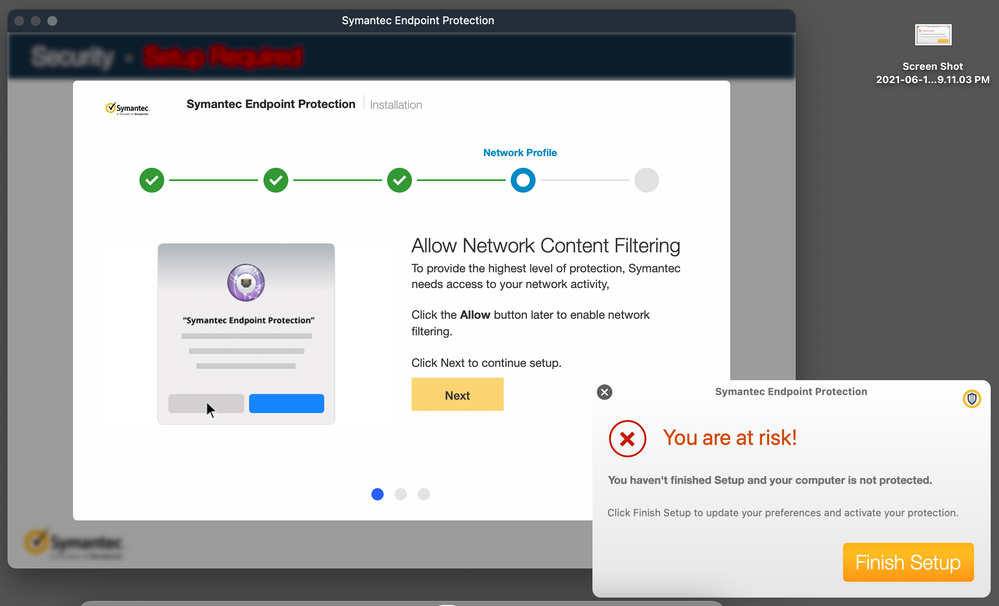
I tried rolling out SEP 14.3 RU1 MP1 (14.3.3580.1100) to Catalina and Big Sur Macs, but we've hit a wall on some. Some users are experiencing an issue where once the Network Content Filter is installed (we whitelist via config profile it so they shouldn't get the "allow" pop-up) they cannot connect to the built-in VPN. Removing the network filter returns the machine to normal operation. We have also seen it on some devices not on our domain and with no VPN that it take a long time to download a large file like Xcode for example with the filter active.
Has anyone had this issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-17-2021 09:41 PM
Same here. We are testing version 14.3.1100f3585, and I can not make it working with no user's manual activation. Yes, SEP is not working if bypassing Network Content Filtering. Yes, Network Content Filtering breaks internet outside access. We also do allow-listing Broadcom developer ID via config profile, but manual "fix" pop-up keeps happening
Our SEP rep says it is known issue, and fix is coming in next release, but no ETA. Big Sur is about a year old, and there is still no working SEP version. Same with native M1 support. Sorry to say, but very poor Mac platform support. Honestly, we see no benefits using SEP but only spending tons of our hours/$ on betta-testing for Broadcom, opening support tickets, providing testing results, logs, screenshots, etc. Unfortunately, SEP is part of IS Security requirement, wish it changes soon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-20-2021 06:56 AM
Hi,
I currently have the this known issue also with the latest SEP and Big Sur - the content filter bug that hangs the entire network on the computer.
I was wondering if anyone managed to get a response from Broadcom with a solution,
or at least a way to diagnose and prove what exactly causes this problem (wireshark or anything else…)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-20-2021 11:25 AM
My environment is affected by this too with the latest SEP and Catalina but not Big Sur, probably because I currently don't allow 3rd party kexts in Big Sur in my managed environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2021 06:25 AM
@dng2000 How do manage to stop the 3rd party kexts?
does it change the way SEP works?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2021 10:10 AM
@gurduv Sorry I mixed things up causing confusion. To clarify:
On Intel-based Macs, I didn't do anything special other than not allowing older versions of some security software to install on Big Sur. It's just newer versions of some security software that the vendors updated specifically for Big Sur that no longer has kexts. To answer your 2nd question, it doesn't change the way SEP 14.3 RU1 and newer works because those newer versions no longer use kexts as far as I'm aware.
On Apple silicon Macs, I don't automatically allow any kexts or reduce security mode. How well that will work remains to be seen because my environment isn't officially supporting M1 yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2021 10:57 AM
@dng2000
Do you use any similar config profile setup like recommended by Symantec?
https://knowledge.broadcom.com/external/article/176222
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2021 11:11 AM
@mhasman Yes. I tweaked mine by having the kernel extensions payload in a separate configuration profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2021 11:50 AM
@dng2000 Thank you David! I did the same config profile. Still, when SEP 14.3 is installed, there is Network Content Filtering prompt happening
)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-22-2021 10:15 AM
The manual "fix" pop-up appears in my environment too. As for the NCF, when allowed via config profile, the setup screen still appears but it just automatically activates NCF without prompting the end-users to allow or disallow. That's how I remembered it when I was testing it prior to implementation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-22-2021 02:15 PM
Thank you, David!
What is your implementation best practice? Do you inform users do not panic when seeing those scary security notification messages, and put to documentation what steps they should follow, themself?
Asking because our enterprise takes security very seriously, and I definitely do not want to deploy anything which creates hundreds security issue report calls to support. IMO not the best experience for users opening their new Macs for first time...
With SEP 12 and Catalina, we have full setup happening in background. I wonder configuring the same with SEP 14 and Big Sur, but still struggling, testing
I appreciate any recommendations
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-25-2021 06:25 PM
In my environment, we educate our end-users with screenshots to ensure they know what to expect. I temporarily relaxed enforcing SEP Network Security NCF due to problems it caused with duplicates (i.e. SEP Network Security 1) so I have to educate my users to expect that pop-up screen and explain why they're required to respond to it and allow Network Content Filter manually.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-28-2021 03:26 PM
Check that one:
https://knowledge.broadcom.com/external/article/176222
There is CP attached, but you still have to add System Extensions payloads. Seems like Network Content Filtering part does the job. I created CP by that instruction, and now SEP activation is happening by itself in background, no user action required
I would recommend do not edit existing CP but create the new one
Still prefer SEP version with no Network Content Filtering. Broadcom rep says it's coming with RU2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-28-2021 10:57 PM
@mhasman They have two more days...