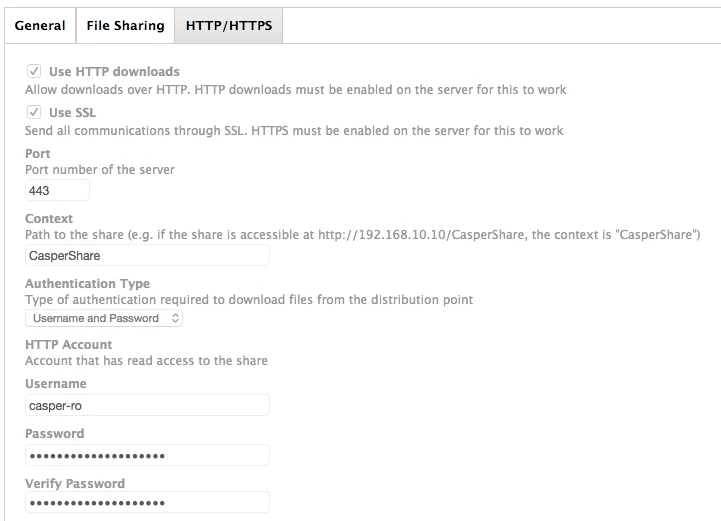
I'm trying to setup an HTTPS share to be used as a distribution point. The share seems to work fine when mounting it via the finder with https://servername/share. It prompts me that it's an unknown certificate, but once click ok, it mounts the share. The server is using a self signed certificate. I'm guessing that's where the hangup is when a client tries to download a package using that share. It appears as tho it is downloading in the progress bar in Self Service, but it eventually fails.
On the JSS, i have HTTP and SSL selected for the share, port 443, context is the share name, authentication type is certificate. I exported the self signed cert from the yosemite server and uploaded it to the JSS.
Any ideas?