- Jamf Nation Community
- Products
- Jamf Pro
- Re: The upcoming Bindpocalypse...thoughts, fears, ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
The upcoming Bindpocalypse...thoughts, fears, plans, ideas?? To NOMAD or not to NOMAD?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-02-2022 04:39 PM
Calling all Jamfers (not sure if that's a word for all Jamf Nation members, but it is now haha),
Ok, so like a lot of mac admins out there I've had my share of AD binding breaking in the past, but the information making the rounds regarding "bindpocalypse cve-2021-42287" seems pretty scary. I know that Apple has been encouraging mac admins to get away from AD Binding for a while now, but here's the thing...it has worked really well in terms of being easy and mostly reliable for enterprises, esp. those that like my situation (K-12 public school) have mac labs and not a whole lot of mobile devices (laptops). It has been an easy way to allow AD users to authenticate and mount their network home folders.
There's NOMAD and Jamf Connect...I deployed NOMAD a year or so ago when we were having some binding and there for login issues. It was ok, but I didn't love it. The issue of what happens when users change their AD password on one NOMAD iMac what happens when they try to log into another one? I can't recall the specifics but I think it was cubersome. Also the mounting of network home folders was also an issue--that again I recall had a solution but it wasn't as neat and clean and easy as AD Binding has been--emphasis on has been.
FYI: We don't have Microsoft Azure, our AD is local. Going to Azure is not something that is in the cards for us at this time and honestly we don't have a need for it. I mention this because I know that NOMAD doesn't always play nice with local AD binding.
I'm sure you can all relate to the following: 1.) end users don't like change 2.) change is a pain to implement because of the learning curve (and that's assuming there are no glitches or end user error) 3.) replacing a relatively smooth process with one that requires more steps is something you only do if you don't like yourself :-)
All of that said, does anyone know if the Bindpocalypse is still set to collide with the world of AD Binding on Oct. 11th? Has Microsoft made any statements? Will it be limited to Domain Controllers running specific versions of Windows Server?
If anyone has an extremely clear, step-by-step guide to configuring and deploying NOMAD (that hopefully addresses AD password changes, mounting of network home folders, and other miscellaneous issues), I would be forever grateful. :-)
Please share your thoughts and experiences, suggestions and ideas, and whatever else you might want to contribute!
Thanks in advance!!! :-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2022 06:22 PM - edited 10-02-2022 06:24 PM
The only real reason to bind macOS is in a lab environment. CVE or not, there will be another CVE eventually because the fundamental basis on how binding is done will never truly ever be secure. Apple doesn't want you to do it, even Microsoft is slowing sunsetting the process for PCs. Between not being able to sync FileVault passwords, the fact macOS cannot read GPO, the fact you would still need a background admin which in most cases is a shared password, and accordingly not secure, not to mention if anyone travels with their laptop, they still need VPN to get to your on-prem AD instance (which itself is a security concern). Besides - with the "id" command even a standard user can scrape your directory information (looking at you, Sony). You may not need Azure now, but you will -- the writing is on the wall to that AD is going away in favor of certificate based management. You can't let your users desire for nothing to ever change get in the way of good security practice.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2022 06:57 PM - edited 10-02-2022 06:59 PM
@mcrispin Thanks for your excellent points on security! We have 3 imac labs in our school and that has been the major driver of keeping AD binding for now.
I do wholeheartedly agree with your points on security and the eventual sunsetting of AD binding across the board, even with PCs. I also agree that we can't let end users reluctance hold back necessary innovation and change.
But as I learned long ago, end users gotta log in and when they can't or can't easily and reliably log in--torches will be lit and pitchforks will be hoisted :-)
That's why I'm looking for a solution that is easily deployable, reliable, and provides end users with a smooth login experience.
One of the challenges of IT is that if something major goes wrong in terms of security (Sony) it's our fault, but if end users are frustrated with intermittent issues that impact their workflow (logging in, printing, etc) we will certainly feel the heat from that as well. It's always a balancing act.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-03-2022 07:17 AM
If your domain controllers are patched, you're good for now. The Oct 11th change shouldn't cause you a problem. Many AD environments are already operating with PacRequestorEnforcement enabled and binding is still working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-03-2022 07:31 AM
As @cbrewer said, AD should be fine. There was a previous update that broke something, but it has been patched. See Jamf Blog: https://www.jamf.com/blog/bindpocalypse-2022-an-update-to-cve-2021-42287/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-03-2022 09:30 AM
@cbrewer We're running Windows Server 2016 Standard and we've installed patches, however when I looked in the windows registry to confirm the status of PacRequestorEnforcement I don't see it listed in the specified location.
From what I've seen online it should be here and look like this:
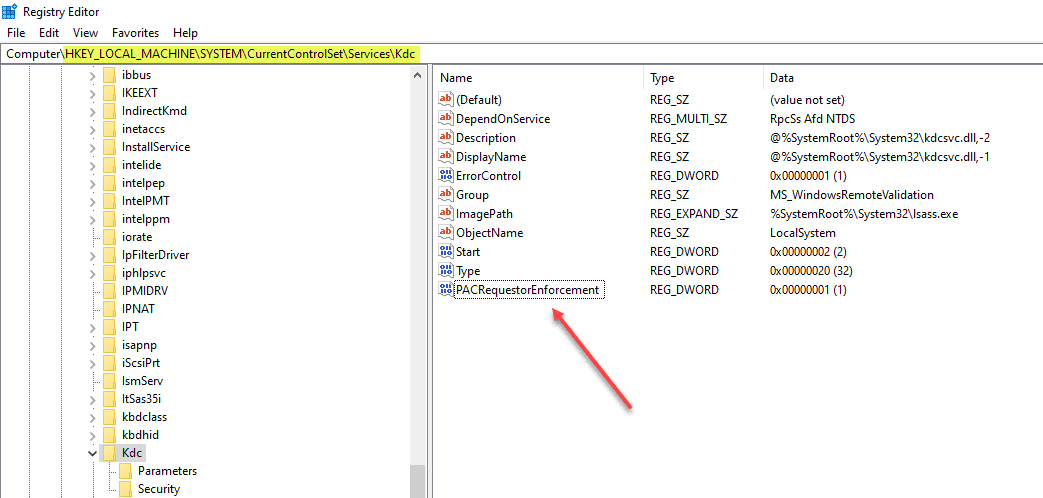
So I have to wonder if I've got it or not and what it's enforcement status is...