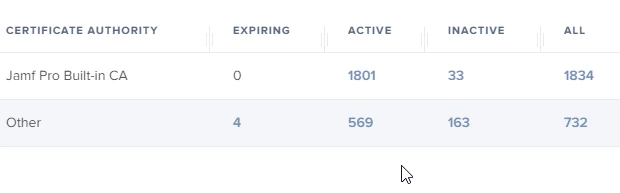
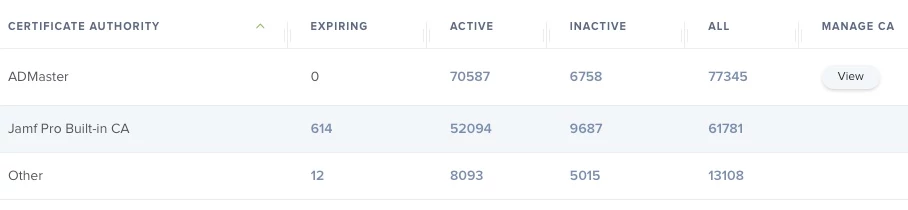
We are implementing a new TLS wireless network in a windows environment. I have the windows 2008 r2 running an enterprise Certificate Authority setup to auto-enroll windows laptops; all of which work great.
The problems are with trying to get our mac clients working with TLS:
I've created a .mobileconfig using Profile Manager in 10.8 Server with Network, Certificate, and AD Certificate sections configured. When I run the profile it prompts for a username and password when I did not enable that option in the AD section of profile manager. This should not be the case! The whole point of TLS is that the certificate is a machine vert and not user based certificate. What am I doing wrong?
After prompting for username/password the profile then fails to install and says "The Active Directory Certificate" payload could not be installed. The certificate request failed."
I am stumped trying to troubleshoot this. The mac client's console does seam to have any more info than was in the error message. On the CA I cannot find any event logging a failed request. In the Certifcate Authoirty snap the "failed request" section does not have my info.
I have enabled auditing on "Issue and manage certificate requests" but don't see my requests appearing in any event logs. http://technet.microsoft.com/en-us/library/dd772671(v=ws.10) Where should I be looking for information about why my request failed?