Hello JAMF Nation,
We are looking to update our passcode requirements to increase the amount of characters needed in a password.
- We are thinking to use the "Change at Next Authentication" option in the JAMF Configuration profiles for password requirements (see below)
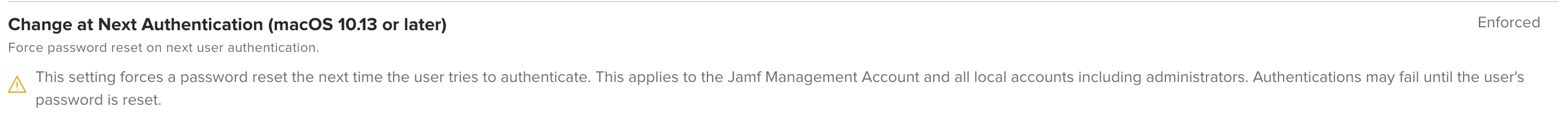
1. Is that the best option to require users to update their passwords to the new requirements? Or is there a better way?
2. Will the "Change at Next Authentication" run only once per machine?
3. Will this work for non-administrative accounts?
In addition, is it possible to view in JAMF password age/length for machines in our org? If not, is there a script that could be run to pull this info?
- Reason being that if we use the above method to update passwords on our machines, we have no clear indication that the user has actually updated their password and that it complies with the new password requirements since that is handled under a configuration profile and not a policy.
Thank you :D


