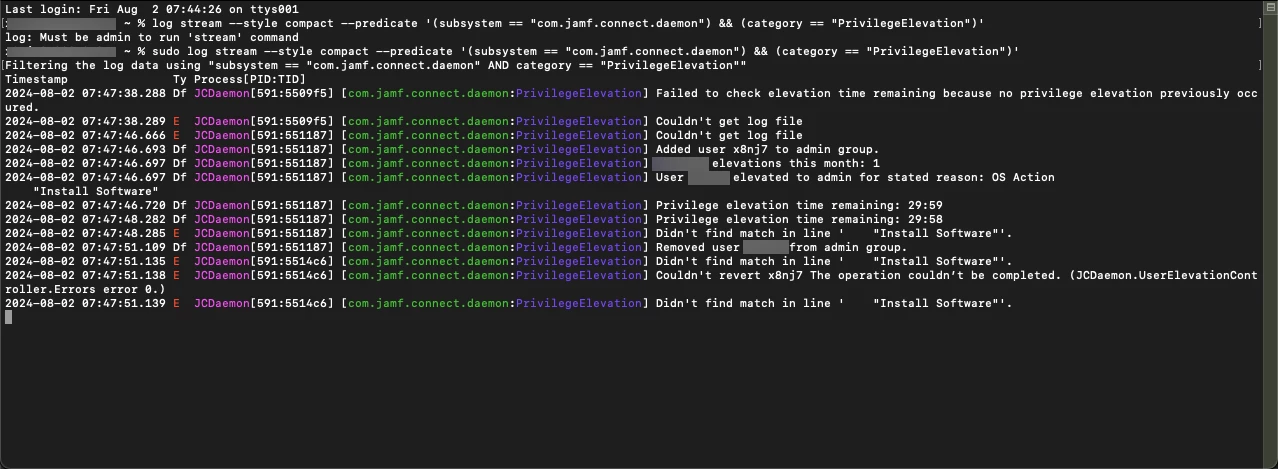
I finally was able to enable the Elevate Privileges option in the Jamf Connect menu and it seems to be working ok. How can I audit who has used it, when, and why?
I saw the documentation about possibly seeing up a SIEM to receive that information, but I'm not sure I know how I would do that. We use Rapid7, and I feel like there's a way but might take a bit of work. Is there any other way to gather that information just so we can see who's using it and why? I tried the log stream command in the documentation just to see what information it showed but it didn't seem to do anything and just sat there at a blinking cursor. I checked Azure's sign-in logs and nothing of note in there either unless I was looking in the wrong place. Security needs me to remove local admin rights from all computers, but we still need to allow our devs to install things for their job and we don't want to be buried under a bunch of requests to remote in and use admin credentials to install simple plug-ins and stuff.