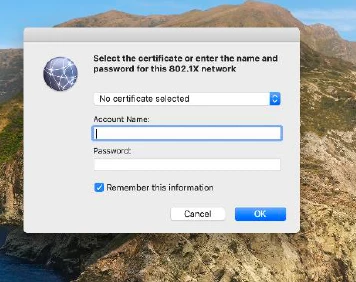
Hello,
So we are configuring ISE in our environment and we cant use scep to automate it because security wont let us open the ports down to the internal scep server. so i just setup the config profile and added our ISE certs etc... the issue is the user are prompted the first time to choose the cert it is always the second cert in the list and it only happens the one time they choose it and they are good going forward... my question is there a way to have the user not have to choose the cert maybe a script that we can run after the config profile is pushed down ?