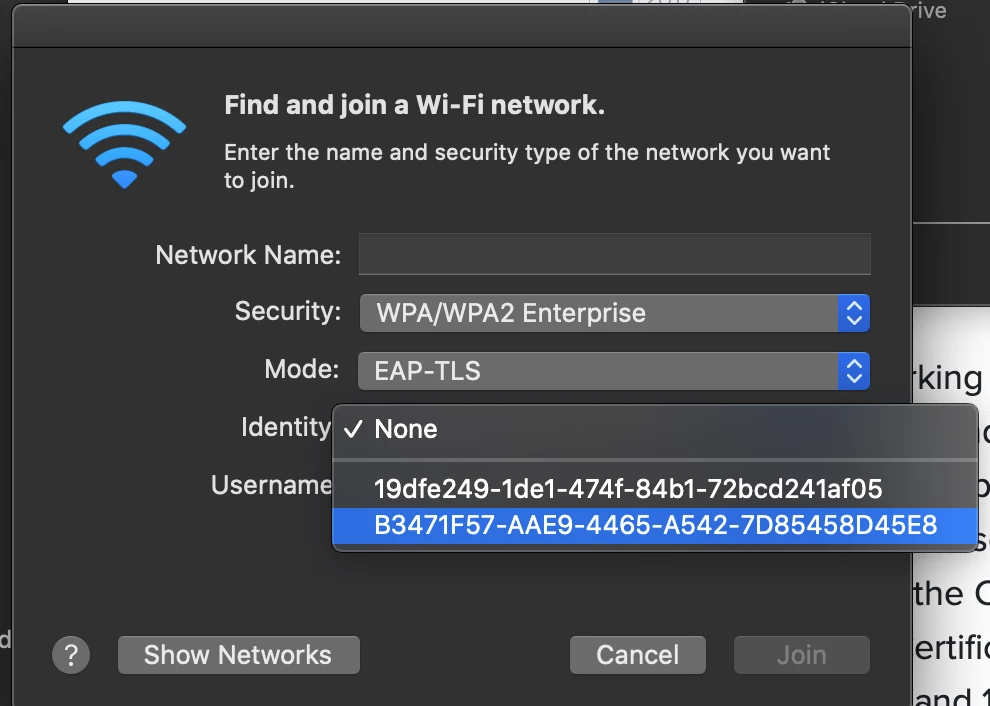
Hi Everyone,
In the JNUC 2013 Using 802.1x with the Casper Suite session it was talked about that it's possible to use Machine based authentication rather than individual user credentials. Has anyone had any success in doing this, and if so would be willing to share their knowledge. I'm very interested in doing the same thing. I can get the profile working with standard username and password authentication hard coded in the profile, but would like to make a profile that could be deployed without user credentials. Also I would like to not have to bind these machines to AD, so if anyone can confirm that this works as well that'd be great! Thanks again to Hopkins Public Schools for the great session!!!