- Jamf Nation Community
- Products
- Jamf Pro
- Re: AD-Certificate can't renew in Big Sur
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AD-Certificate can't renew in Big Sur
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-25-2021 07:46 AM
We have a big problem with our Big Sur machines that can't renew/generate a new AD Certificate.
Big sur machines receive correctly the initial certificate from AD during enrollment, ONLY the renewal feature does not work.
We have tried both on the local network and over VPN, same result. So it's not a VPN issue.
Works fine with our Catalina machines though.
All our machines are bound to AD. We are not using ADCS Connector.
Running Jamf Pro 10.26.1 on prem on a Windows server.
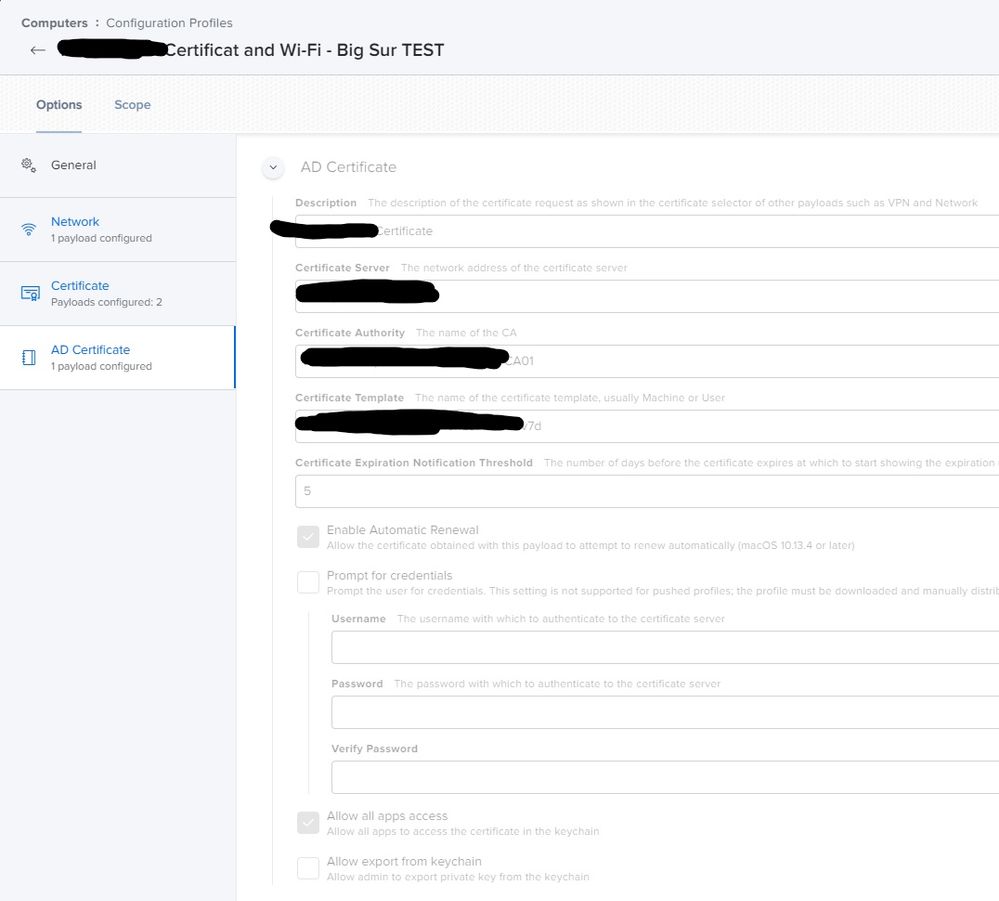
The AD-Cert is valid for 365 days and it set to renew 14 days before expire date.
For troubleshooting purposes, we created a new certificate template with 7 days of validation and automatic renewal is set to 5 days before expire date.
Unfortunately, we get the same problem as before. Works only on the Catalina machines.
We have generated a sysdiagnose file from a catalina and big sur machine and sent it to the jamf support. Without any luck so far.
Someone else who has encountered the same problem with Big Sur?
- Labels:
-
Configuration Profiles
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-25-2021 08:08 AM
I havent seen cert renewal issues yet per se, but I have noticed that Big Sur isnt trusting my internal root AD cert at deployment time.
All my managed Macs get both a root and an intermediate cert via packages/scripts (not profiles) at enrollment time. I have torn the package open and there is nothing wrong that I can find.
However, all my Mojave and Catalina Macs trust both my root and intermediate certs with no issues.
macOS 11.2 will be out relatively soon (in public beta now).
Update - my initial issue is resolved. Replacing packages with profiles allows my Big Sur test Macs to trust the root cert automatically.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2021 05:01 AM
@Gonzalo we see the same behaviour on our machines. Renewal works fine on Catalina machines but not on Big Sur :(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2021 06:09 AM
@Gonzalo This is probably an Apple bug. Have you opened a ticket with Apple?
@dstranathan Big Sur no longer allows trusting of root CA's without a user entering their password. So using packages/scripts to install certs to the System keychain no longer works unless you do it with a logged in user and that user enters their password. The supported method is to use certificates, but as we all know, that doesn't fully trust those certs which is why you were probably using a script.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2021 06:48 AM
@patgmac I have not opened a ticket with Apple yet, but will probably do it now :)
I just saw the following in the latest release notes from Jamf Pro Beta 10.27, so maybe Jamf is on it?
We are now releasing Jamf Pro 10.27.0 beta 2! This release contains some new enhancements to Computer Device Certificate Renewal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-26-2021 08:06 AM
Not sure, I would post in the beta board to get confirmation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-01-2021 02:45 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-01-2021 05:29 PM
@Gonzalo We pay $17k a year for the privilege of opening tickets with Apple. 🥴
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-02-2021 06:10 AM
@Gonzalo Feedback Assistance is one option, getting the expensive support that @patgmac mentions is another one. But have you tried whether 11.2 fixes this? I think it removes some of the excessive restrictions of Bif Sur.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-03-2021 05:53 AM
But have you tried whether 11.2 fixes this? I think it removes some of the excessive restrictions of Bif Sur.
@mschroder Still broken in 11.2 :/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-03-2021 09:49 AM
@user-TWQHooQpVh I'm confused why you're advising disabling SIP in this instance. How does that fix certificate renewal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-03-2021 10:12 AM
My enterprise support rep also reminds me to use AppleSeed too (https://appleseed.apple.com/sp/help/faq)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-12-2021 12:43 PM
@Gonzalo have you had any updates on this issue?
I'm still seeing it, too. Jamf also still lists it as known issue PI-009786
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2022 02:04 AM
Just started to see this issue myself. However one of the devices is on Catalina. What method of updating are people using given auto renew is not working? I can use our ADCS Connector if all else fails, which was setup as a POC, but this only helps get on out vpn, I never got the connector to work for internal Wi-Fi.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2022 08:22 AM
Was there ever a resolution to this issue? I have many clients not renewing AD certificates, and I see no evidence in the ManagedClient.log that they ever try to renew. I can see the initial certificate enrollment just fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-24-2022 11:04 AM
Confirmed this is still an issue and an open PI yet.
PI103872 - PI-009786: Computers with macOS 11 fail to renew the certificate when Enable Automatic Renewal is selected in the AD Certificate payload of a computer configuration profile.
Our Jamf support contact said there is no workaround and directed us to engage Apple support. We did simply invoke a 're-push' the Config Profile manually and verified devices were receiving a new cert with an updated date/timestamp.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-25-2022 08:59 AM
Yeah we started a case with Apple and they said it's a known issue, but didn't provide any further detail. For now we have moved authentication to a predefined username and password while we explore replacements for NPS.