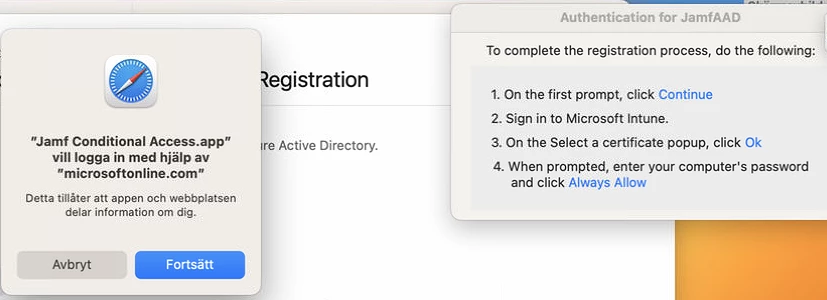
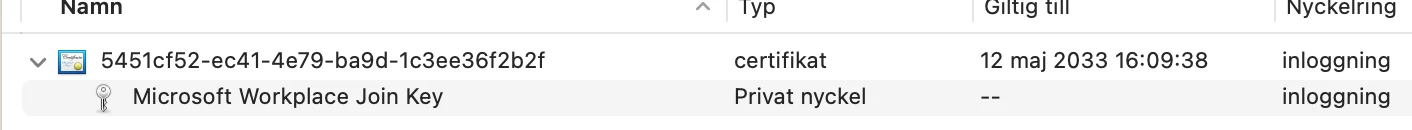
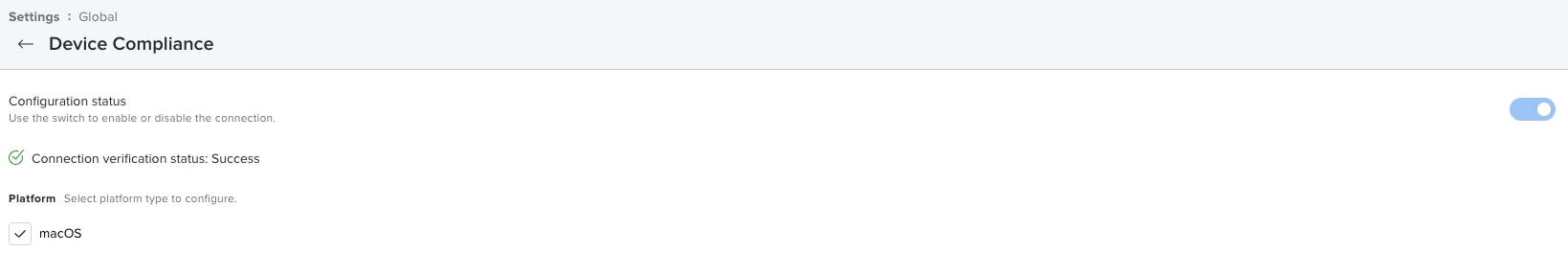
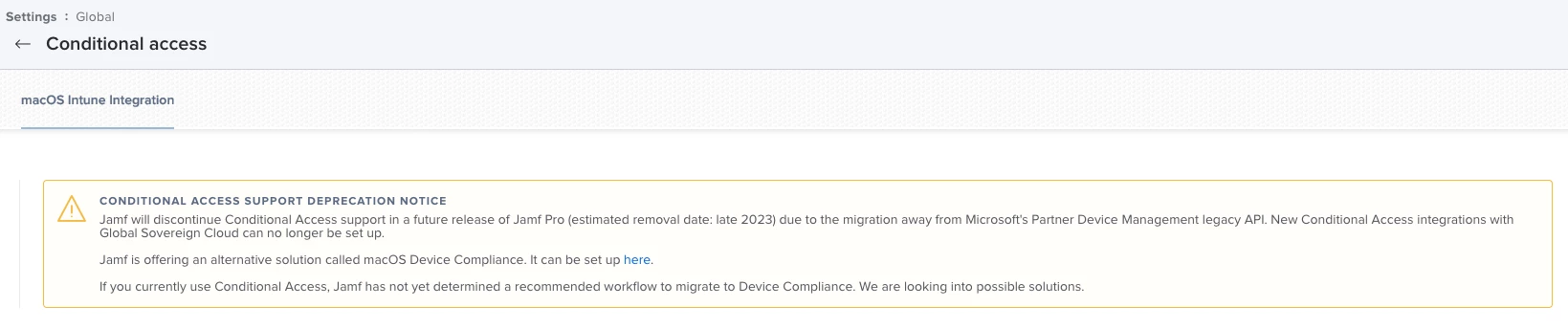
If any of you are tired of your users receiving jamfAAD pop-ups, I would highly recommend transitioning to device identification using certificates. This method of conditional access allows you to control conditional access directly from your Jamf Pro server. Access is simply determined by the presence of your certificate. (This does require your users to have E5 licenses)
The certificate is deployed via configuration profile...so no more manual registration either. Perfect for zero-touch deployments. To stop the pop-ups unload or delete any launchAgents related to the jamfAAD Agent.
You can read more about this process here.