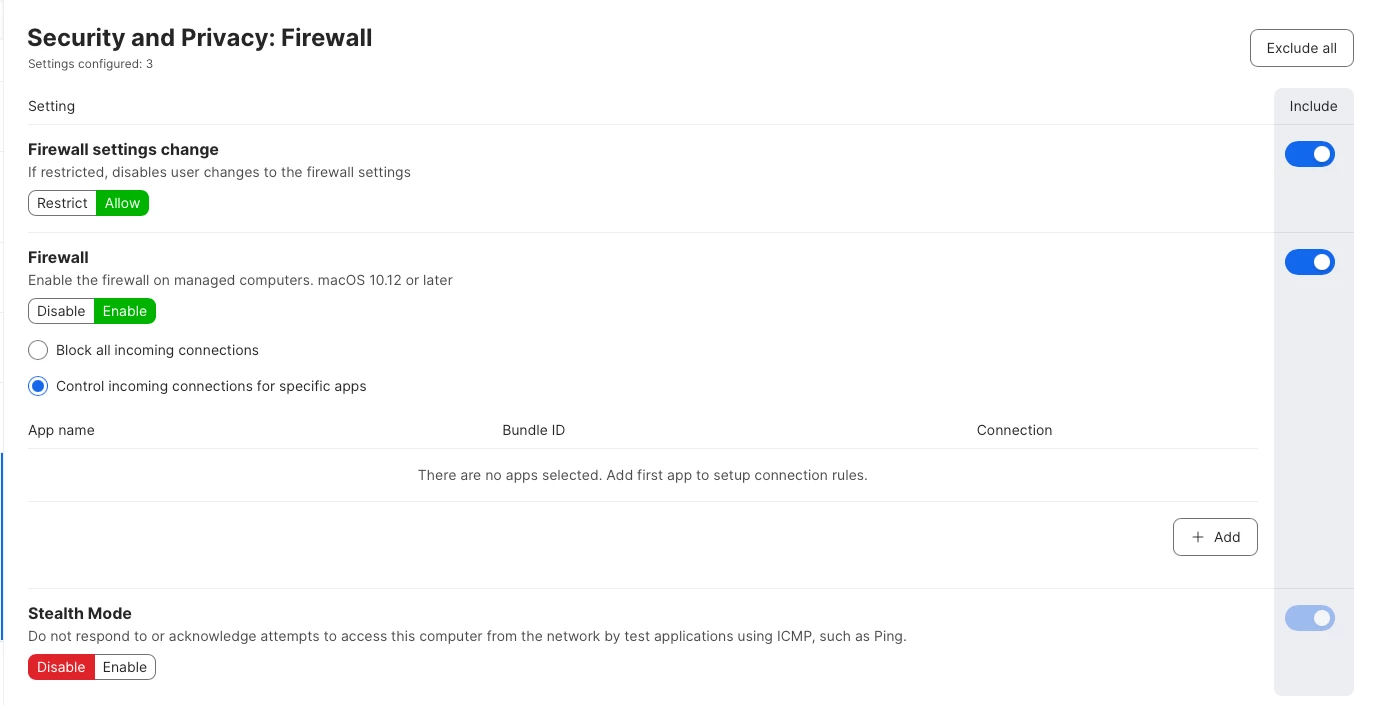
Hi, due to an Audit finding we are to enable the native macOS Firewall in our Mac estate consisting of about 150+ machines. I've created the config profile with the Firewall payload and it deploys and works with no issue, but we donot want stealth mode to block the ICMP protocol, as we need Ping and other network troubleshooting utilities that it provides. Also dont want screensharing blocked, as well as Airdrop. Any advice how to accomplish this please?
Question
Enabling macOS Firewall
 +3
+3Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.