- Jamf Nation Community
- Products
- Jamf Pro
- Re: Enterprise Always On VPN Solutions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Enterprise Always On VPN Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-06-2017 10:08 AM
Does anyone have any recommendations for “Always On” VPN solutions for Macs? We currently use Pulse Secure (by Juniper Networks) for our Windows machines but Mac's aren't supported. We are looking to do certificate based authentication with that “Always On” VPN solution.
- Labels:
-
Configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-06-2017 10:21 AM
We actually use Pulse Secure in our Mac environment and it works very well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-07-2017 06:58 AM
Does it work with certificates? We use it with our Macs but we need it to work with certs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-07-2017 07:01 AM
It does. We use an MDM SCEP-issued identity cert in combination with a local hash file.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-07-2017 07:07 AM
Does it work with certificates? We use it with our Macs but we need it to work with certs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-07-2017 07:45 AM
We are in the middle of testing out Netmotion, having issues with the machine certs to work though. We use Junos Pulse for our normal VPN solution though. And it seems to work just fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-07-2017 05:21 PM
We are currently using PaloAlto GlobalProtect and it has pre-logon "always on" once certificate and user SSO are authenticated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-13-2017 08:51 AM
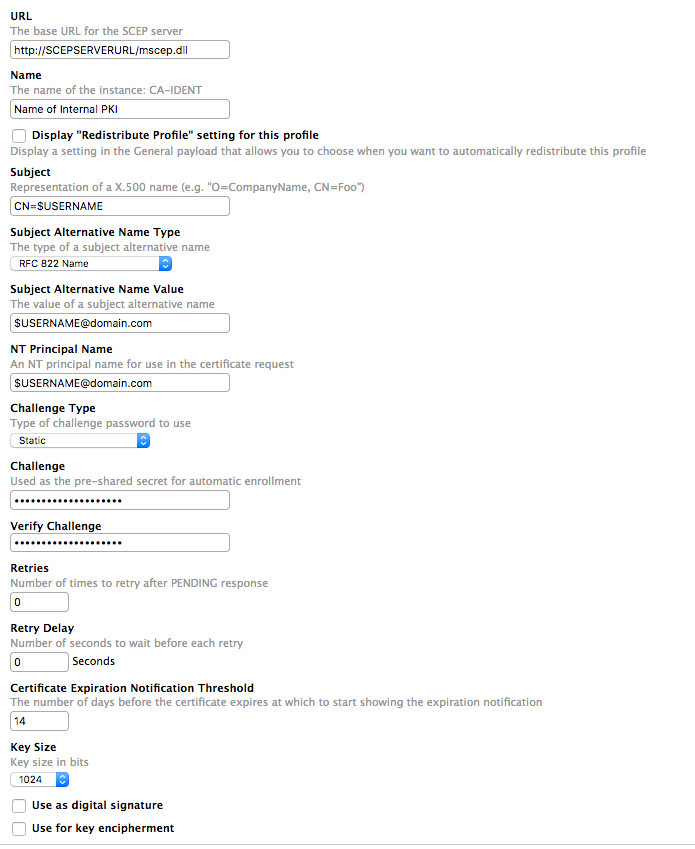
@AdamH Can you provide any other details in how you got that setup and working? I'm assuming you used the SCEP payload in JAMF, are there any specific SCEP settings you can provide? I'm want to pass this information onto our systems engineering team. Any info would be much appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-13-2017 09:00 AM
Sure...
The SCEP setup in Casper is pretty straight forward. It is mostly reliant on your Internal CA/PKI and your SCEP server.
The payload itself will generate an identity certificate in the users keychain that is named after their User Principal Name.
When Pulse authenticates, it will be checking for that identity cert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-25-2017 01:01 PM
We are using NetMotion, as another post mentions, with Macs, iOS and Android and have it working with a combination of client certificate plus user ID/password credentials for 1+ factor authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-29-2017 03:06 PM
Anyone using GlobalProtect know how to configure so that a new user can login with their Active Directory credentials at the login window? I am finding that GP lock network access until the user is authenticated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2017 09:55 AM
@jason.bracy We are currently running into the same issue and the only work around Palo Alto is providing us with is this article they have on their KB since 2013: https://live.paloaltonetworks.com/t5/Management-Articles/GlobalProtect-Requests-System-Keychain-Access-on-Mac-OS-X/ta-p/53332
I would love to hear any other feedback on how anyone on this site has done a true zero touch deployment on Global Protect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2017 11:06 AM
We didn't need to give access to the keychain. Pre login just accesses it since no user is logged in there is no prompt and we have not had any issues. Our issue was that we did not have an internal proxy configured. Once we did that it started working correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2017 11:50 AM
@jason.bracy How are you guys using GP? Are you guys using cert based authentication or username/password? We currently are using cert based but it still prompts users to access their keychain unless we exclude the PANGPS file in access control. I've tried scripts to add the file but have not been successful which means we would have to manually touch all the Macs we have in our environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2017 12:02 PM
We are cert based pre login and then username/password once a user logs in. We looked at cert based for users, but that prohibits local user accounts from having network access as they don't have a cert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2017 01:17 PM
Global Protect. I am wrestling with adding the a cert for the app to use pre-login. The idea of doing this on every machine https://live.paloaltonetworks.com/t5/Management-Articles/GlobalProtect-Requests-System-Keychain-Access-on-Mac-OS-X/ta-p/53332 is silly in the enterprise.
This imports a cert (if I know the secret word) and gives the app permissions I need. The sudo can be dropped when sending the command with JAMF Pro.
sudo security import /path/to/cert_gp-ao-client.p12 -k "/Library/Keychains/System.keychain" -P s3cr3tW0rd -T /Applications/GlobalProtect.app/Contents/Resources/PanGPSI hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-24-2017 09:28 AM
@chris.hansen What you need to do is deploy the your company's Root.CA cert to the user login keychain, once you do that it should not prompt for a admin username and password. Where I am having issues is doing that via script since we do not have Jamf in our environment the script part is failing for me. I was able to test this out throughly on my test machine and exporting the cert from the System keychain to the user login keychain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-24-2017 11:01 AM
We use Pulse on our Mac as well. We are looking at moving to Cisco VPN to take advantage of the native VPN client in Mac OS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-06-2018 06:08 AM
Has anyone been able to use configuration profiles to setup Pulse Secure? Or is there another method that can be used to have it setup to use certs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-12-2018 08:45 AM
@Izrae Could you share how you got this working. My Mobility client is not even seeing my VPN profile. And the Netmotion documentation is pretty bad.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-05-2019 09:46 AM
Is there a way to set this up without a Client on the macs we currently have it setup on our windows environments via Group policy and it works fantastic. Wanted to know if anyone has setup Open VPN on the macs without a Third party Application.
Thanks In Advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-06-2019 04:00 AM
Posted: Yesterday at 5:46 PM by CorpIT_eB Is there a way to set this up without a Client on the macs we currently have it setup on our windows environments via Group policy and it works fantastic. Wanted to know if anyone has setup Open VPN on the macs without a Third party Application. Thanks In Advance.
The OpenVPN system normally uses its own proprietary protocol and therefore as such the built-in Mac (or iOS) VPN clients cannot talk to it. There is an official OpenVPN client for both Mac and iOS which you can install. The iOS one does support pushing a mobileconfig profile to configure it but as far as I can tell the Mac OpenVPN client does not. If it were to work on a Mac it would be via the 'Custom SSL' option which is what you use for iOS devices with OpenVPN.
On the Mac there are some third party compatible VPN clients - that is compatible with OpenVPN servers, the leading example is Tunnelblick. However again non of these support mobileconfig profiles. :( I spoke to the author of Tunnelblick about adding this capability but he was not interested in doing this.
If you want to use a VPN system which does not need a VPN client to be installed on Macs (or iOS) then your choices are limited to L2TP, Cisco IPSec or IKEv2.
The nearest solutions for OpenVPN would be one of the following approaches -
- Use the (paid for) OpenVPN Access Server to generate a pre-configured OpenVPN client installer
- or as we do, use a Tunnelblick config file that uses the same (client) certificate for all Macs but also uses unique username and passwords for each user, we can then automate installing the Tunnelblick client with the same config file and each user has to enter their own unique credentials
By the way there is a stupid and massive bug in the JAMF profile for pushing Mac VPN settings. It lists the wrong types of VPN for both 'per app' and 'normal' VPN connections. The iOS profile is correct and fine. This renders JAMF almost unusable for pushing Mac VPN settings as far we are concerned. This bug is well over a year old probably a lot more than that but despite there being an acknowledged PI for it it still has not been fixed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-06-2019 06:50 AM
@jelockwood thank you for that post I appreciate all that information. Has anyone attempted or even try to configure Always On VPN via SSL?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-06-2019 07:06 AM
@CorpIT_eB Last time I checked Apple's documentation the following were supported for VPN on Demand aka always on.
Cisco IPSec, IKEv2, (Various enterprise SSL VPN systems including Cisco AnyConnect, Juniper Pulse, SonicWall) and in theory Generic SSL VPN systems.
Other than being one of the above the additional requirements are that the authentication is using certificates and does not use username and password authentication.
So I am confident it would work with Cisco AnyConnect, Juniper, SonicWall, etc. along with Cisco IPSec and IKEv2. I am also confident it will not work with OpenVPN or Tunnelblick on a Mac but should work with OpenVPN on iOS.