- Jamf Nation Community
- Products
- Jamf Pro
- Re: Falcon Sensor - System Extension approval
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Falcon Sensor - System Extension approval
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-15-2020 08:31 AM
Hi all,
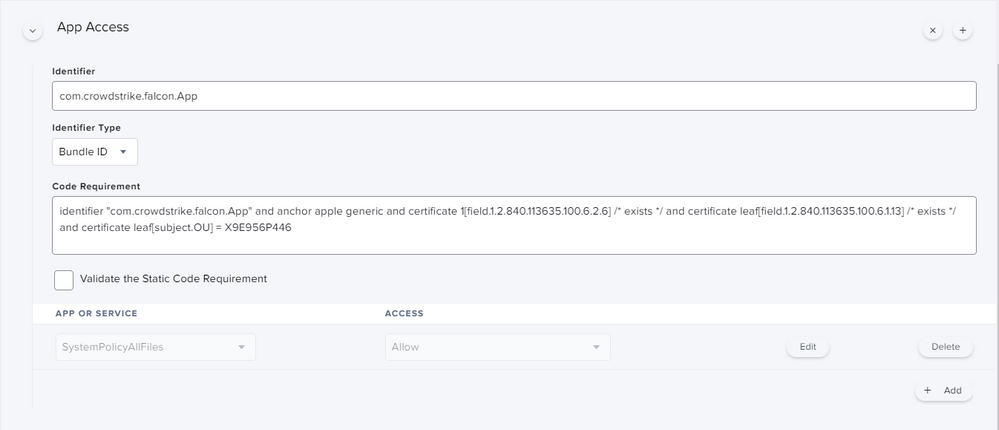
I'm actually using this config profile for pushing system/kernel approval and PPPC control.
Everything looks to be working except for the "System extension approval", it keeps asking for the approval.
It is actually working in macOS Catalina, but I'm not that lucky for macOS bigSur. Any advice?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2020 12:39 AM
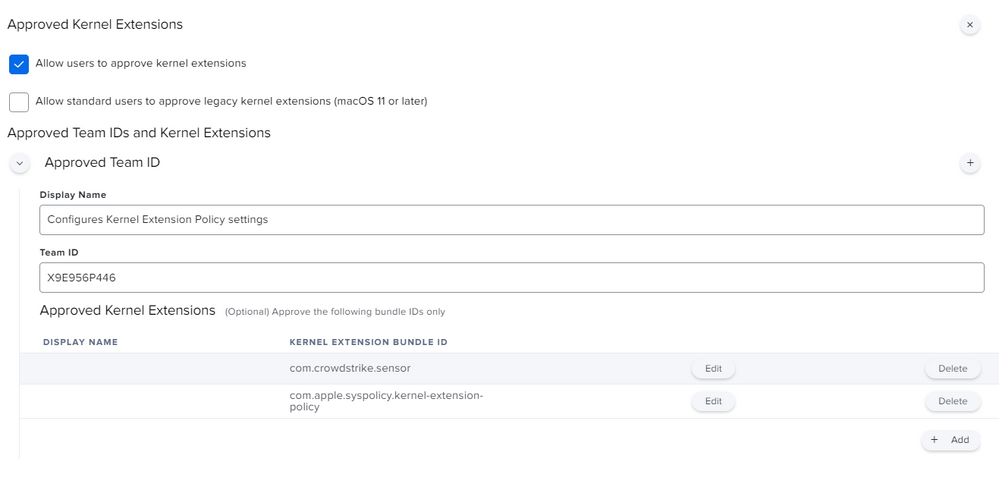
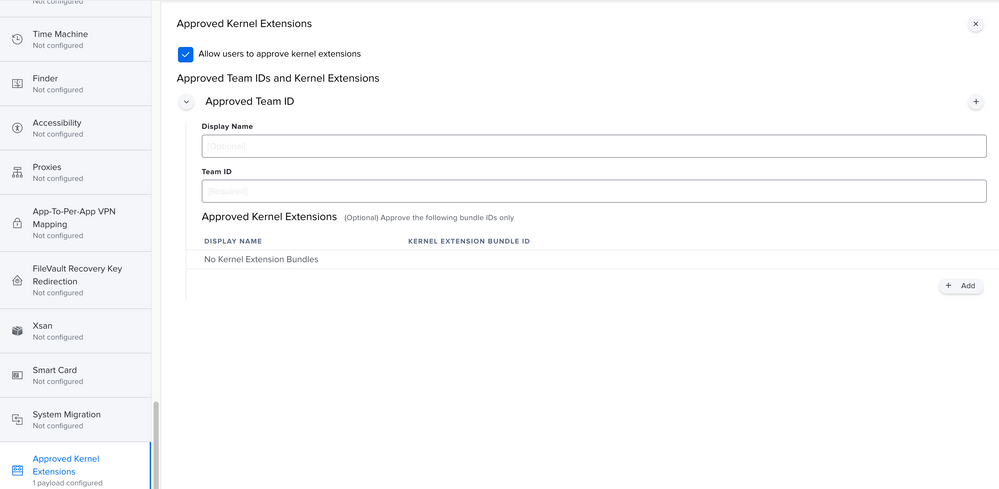
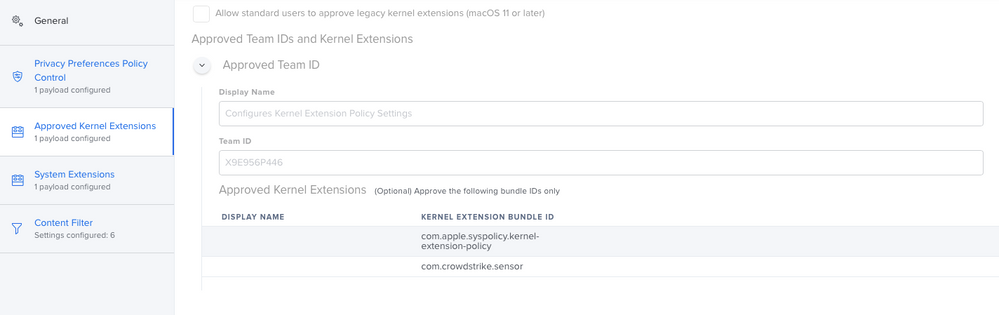
Hi @alessio.tedesco The message is about System Extensions but you showed the Kernel Extension section in the Jamf Pro setup of a Configuration Profile
Scroll down to the end in the sidebar and you will find System Extensions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2020 01:33 AM
Hi @dlondon ,
I'm sorry, attached the correct screenshot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2020 08:04 AM
@alessio.tedesco You are missing some System Extension options in your profile. Having said that, I don't have an answer for you but I'm actively working with both CrowdStrike and Jamf support right now. When I know more I'll post to the following thread.
https://www.jamf.com/jamf-nation/discussions/37488/crowdstrike-configuration-profile-bigsur#responseChild210650
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2020 12:22 PM
CrowdStrike has a profile on their support site that includes all the setting needed PPPC/System Extension..... You have to sign it before you upload it but it is working for me...
C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2020 01:57 PM
Agreed ^ self signing the configuration profile worked for our institution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2020 11:26 PM
I decided to copy-paste without signing the profile to avoid dependencies, opened it in Notepad++ and managed to have it fully working both in Catalina and bigSur, I was just missing a part in the settings, thank you all!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2020 07:36 AM
@alessio.tedesco Glad you got it working. I'd love to see some screenshots if possible cause no matter what I've tried I can't get it to work.
Also couldn't hurt seeing what the profile looks like on a client in System Preferences > Policies as well.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
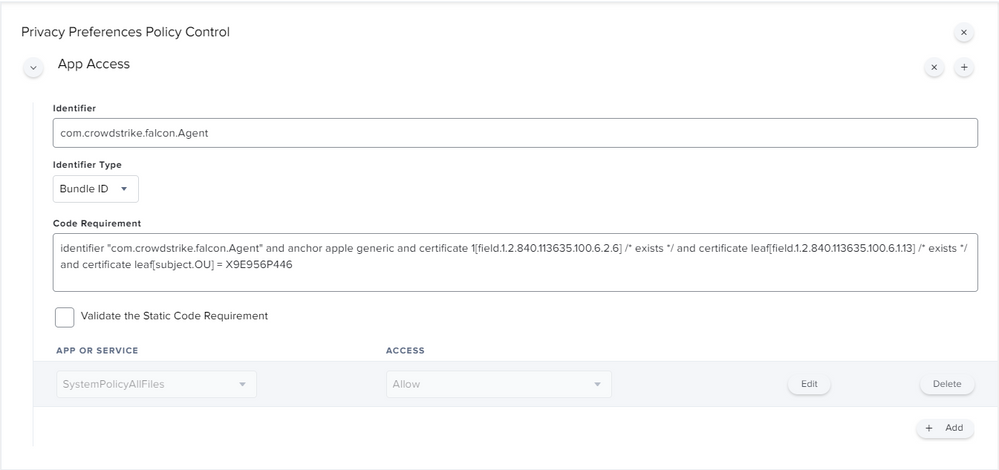
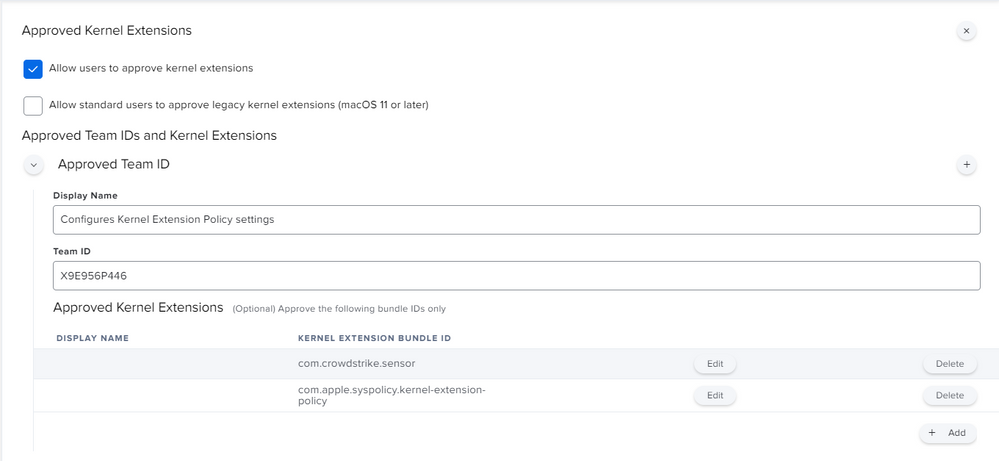
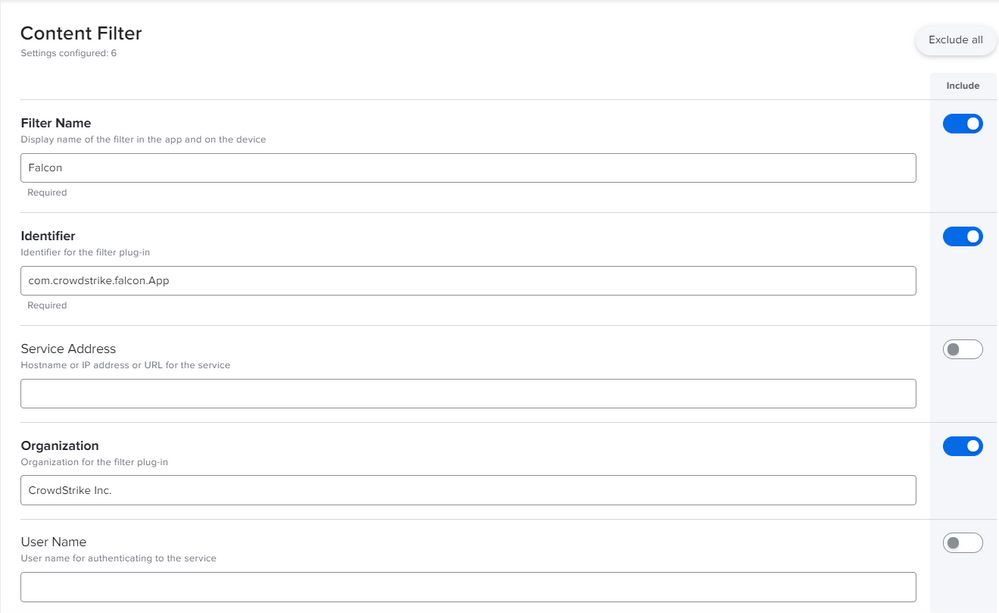
Posted on 12-18-2020 01:51 AM
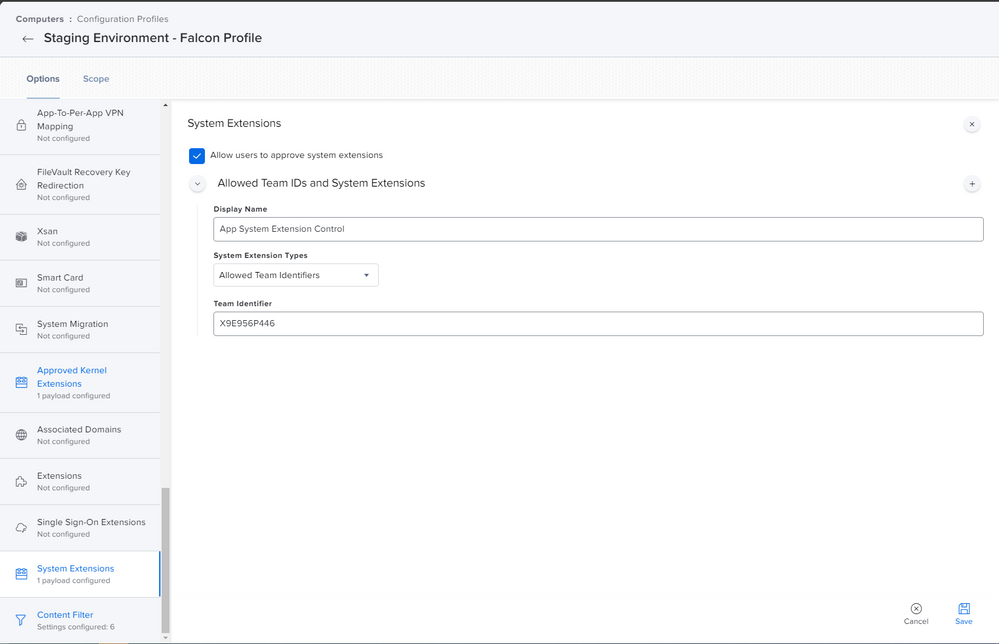
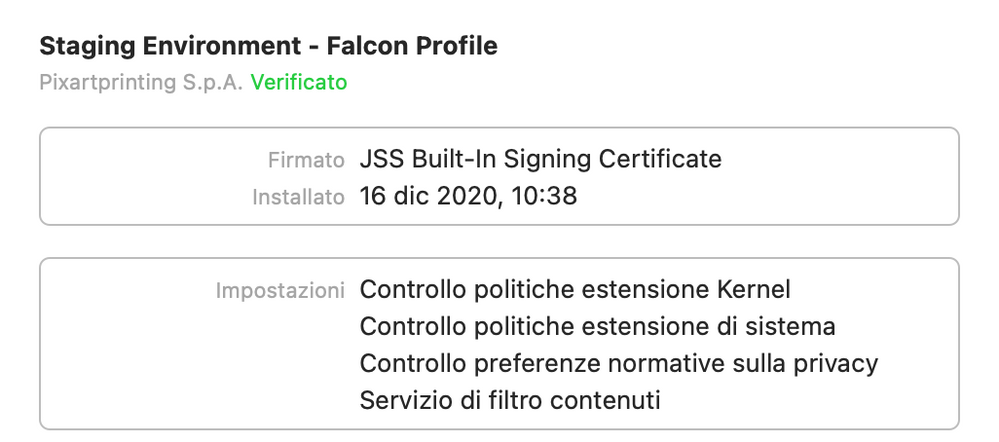
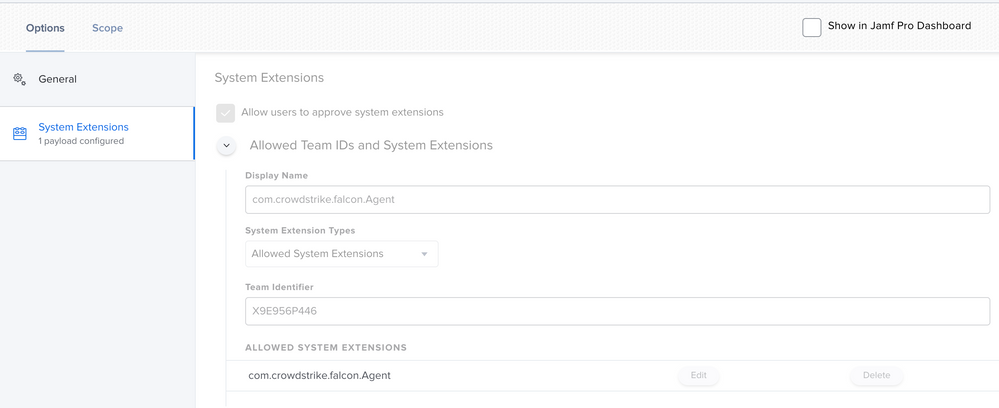
Sure @ubcoit ,
there you go!
This has been deployed through a configuration profile, kindly let me know if you need the text to be pasted here in a comment :)
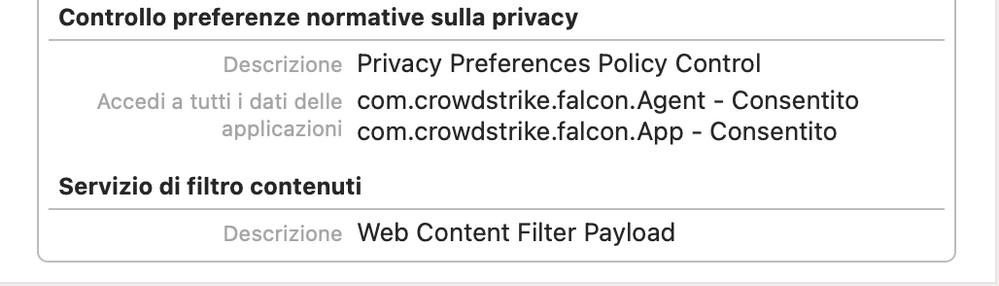
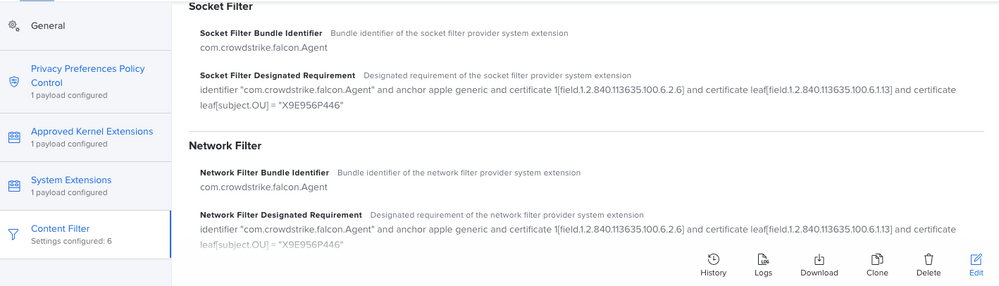
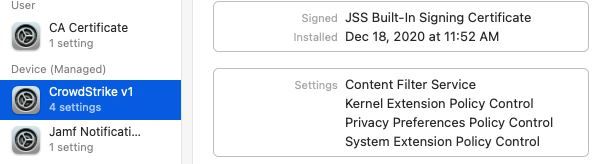
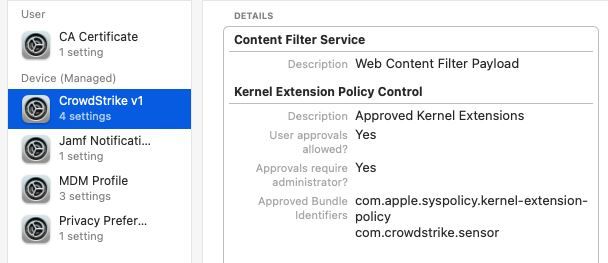
Attached all the screenshots of the policy:
Attaching how the policy looks like in System Preferences:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-18-2020 04:32 PM
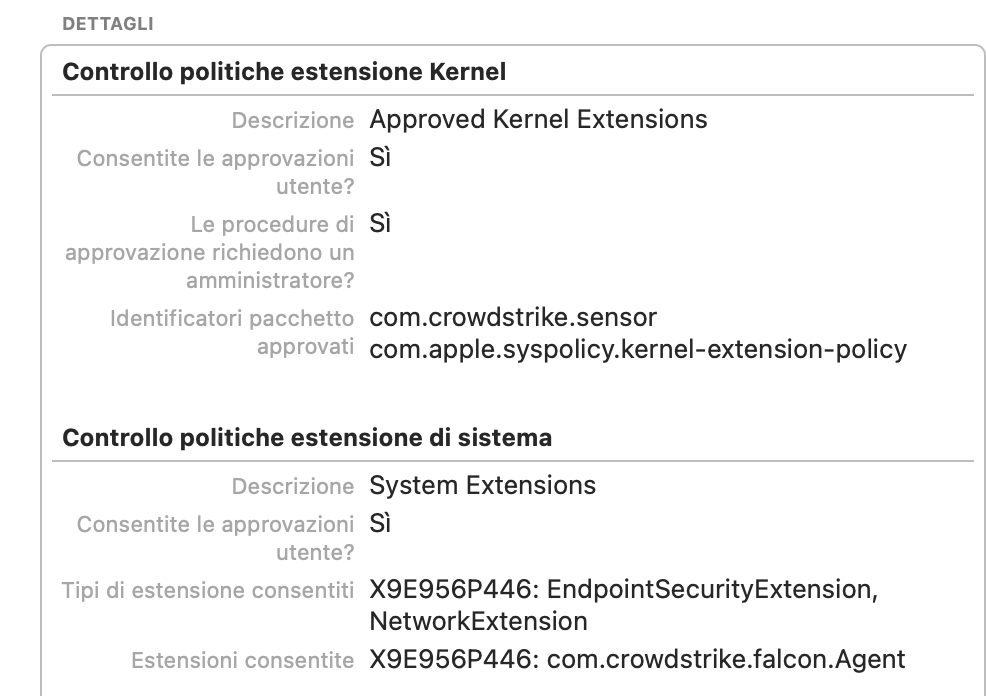
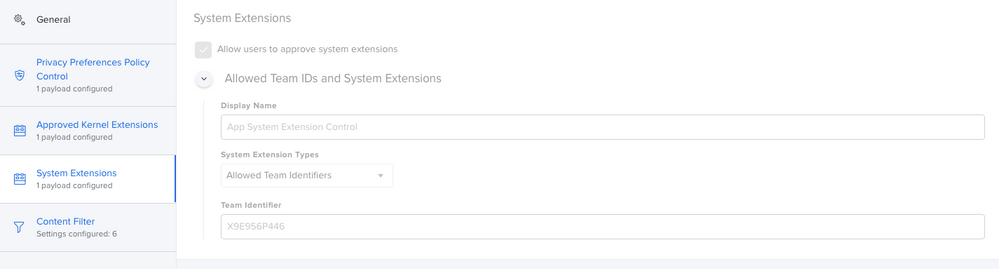
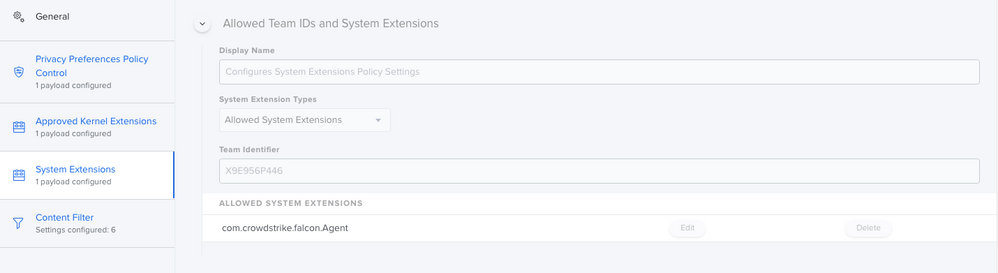
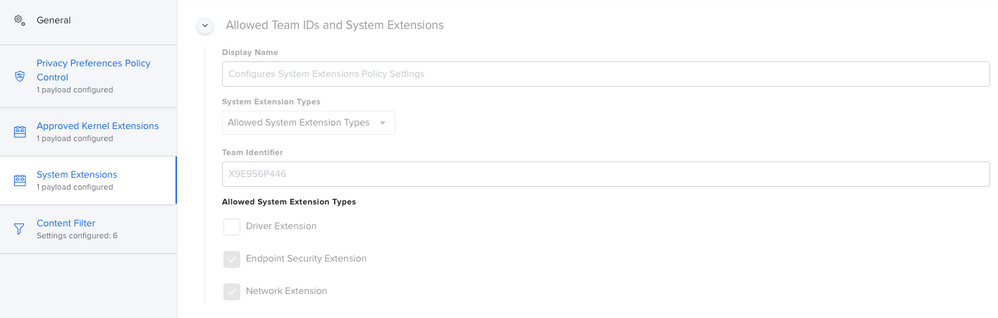
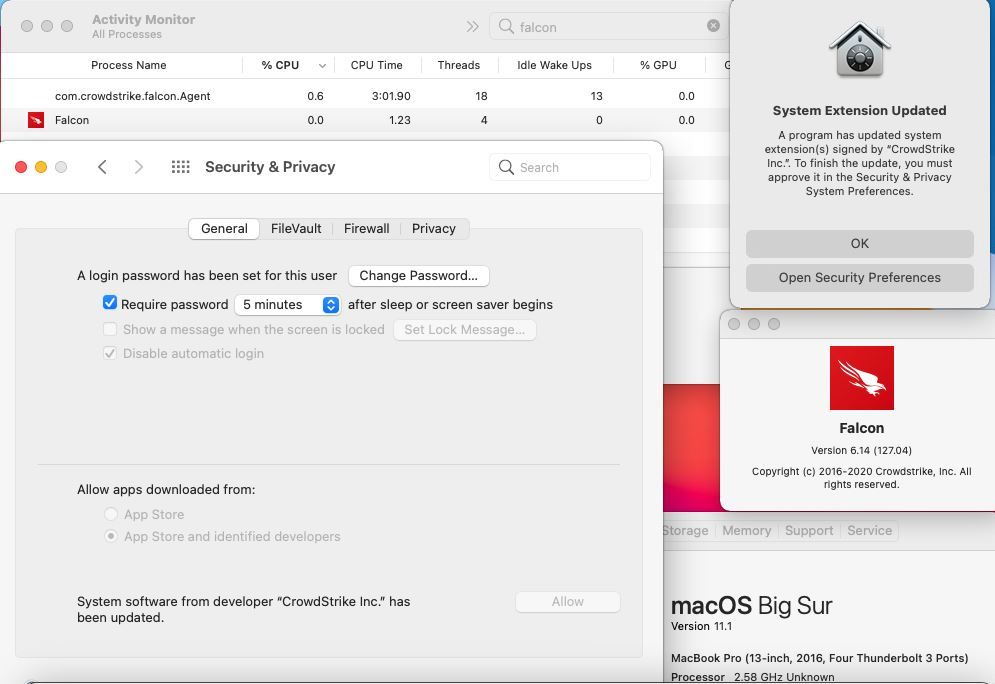
Thanks @alessio.tedesco Still no dice for me. I mirrored your settings, I believe, and other than some of the order of things which I can't seem to control, I don't think I missed anything. End result, CS is running but I get the update prompt in my last photo.
PPPC
Kernel Extensions
System Extensions
Content Filters
Client Profiles Pane in System Preferences
Prompt and other information
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-19-2020 06:34 PM
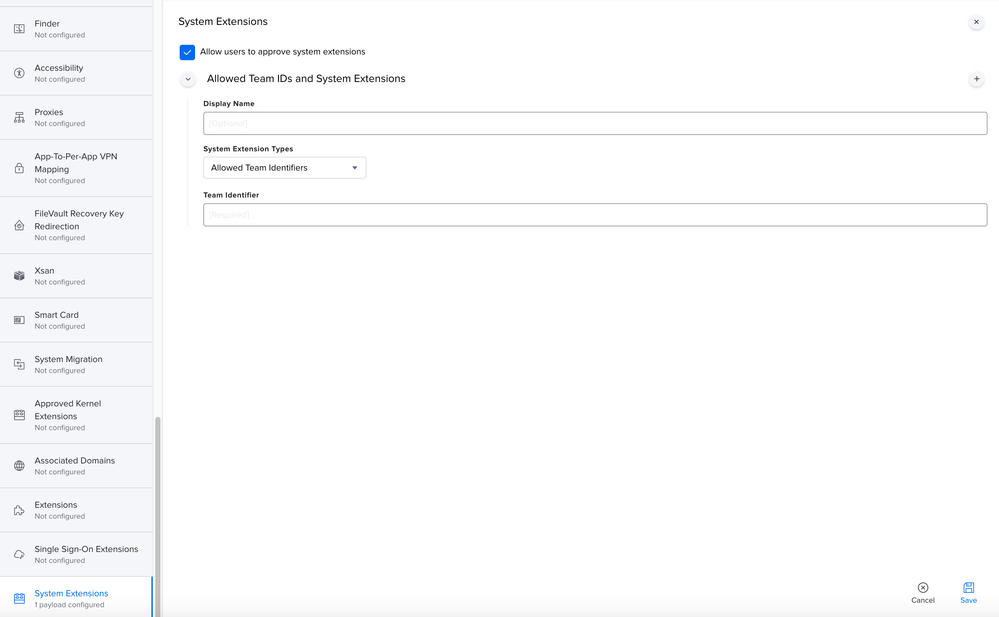
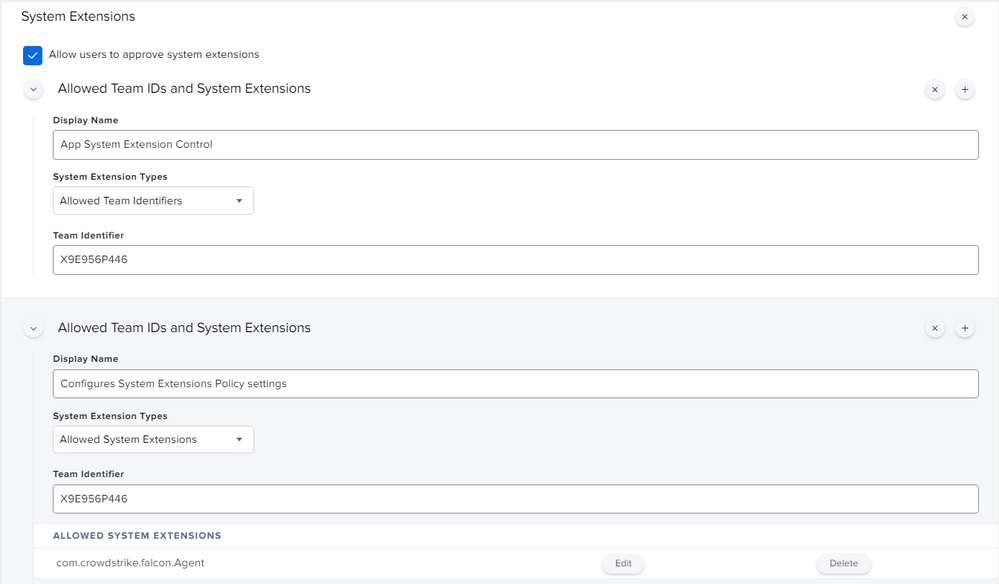
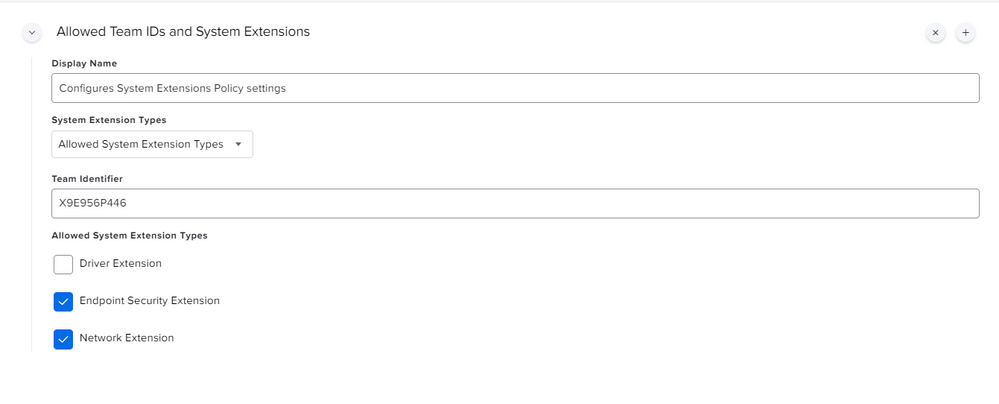
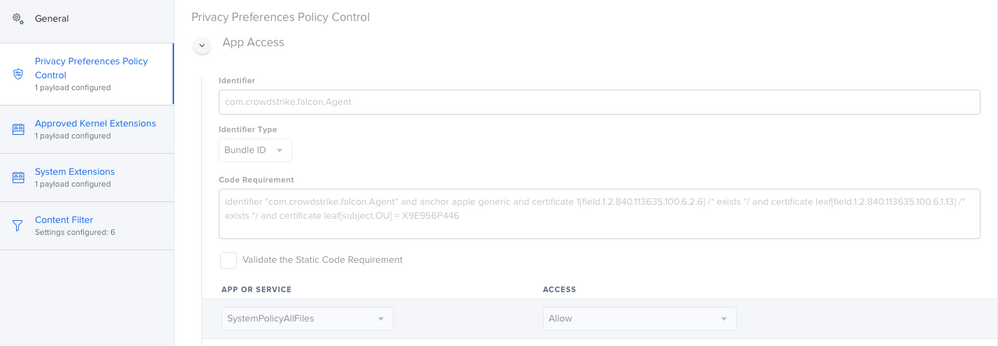
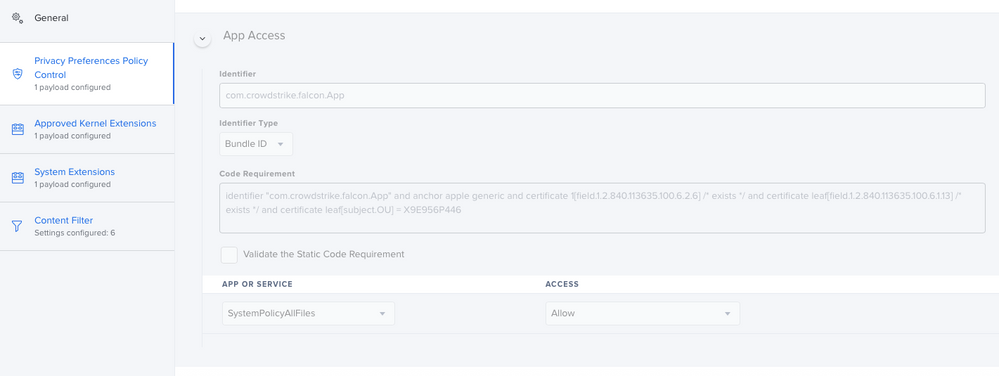
So i've been doing a lot of work with version 6.14. First thing ... split up your profiles! Make the PPPC it's own, the KEXT it's own, the SysExt it's own and so on... Trust me, your Apple Silicon macs will eventually thank you. I've attached how the System Extension payload should look.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-14-2022 06:46 PM
Hello
What criteria are you using for pushing sys ext vs kernel extensions? or are you just pushing all policies PPPC,sys ext, kernel ext, etc.. to all machines?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2022 07:52 AM
I've got smart groups for our machines, per OS back to 10.13 and assign each smart group as per what needs what.
System Extensions
10.15.x
11.x.x
12.x.x
PPPC
10.14.x
10.15.x
11.x.x
12.x.x
Content Filter
10.15.x
11.x.x
12.x.x
Kernel Extensions
10.13.x
10.14.x
10.15.x
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2022 08:51 AM
Awesome, thanks so much for this info. I have smart groups for each OS as well, will scope it out as you have done. Last question, does the Processor type matter as in Intel or M1? When creating and scoping these smart groups
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2022 09:06 AM
I don't believe CPU type makes a difference but I do have smart groups per Intel/M1 for these just for more control and who knows what's happening tomorrow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-14-2021 03:21 PM
Hey @franton, best practices question here. I've been lumping ALL of the kernel extension payloads into one profile and ALL of the system extension payloads into another. Do you have discreet profiles for each extension or do you also group them?
TIA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-14-2021 03:31 PM
Do you guys have it working? We had it working with the CS provide profile in December 100% sure, but now we are seeing a few different OS notifications saying CS has been updated please approve
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-15-2021 01:03 AM
I actually have it working with macOS bigSur, noticed that using the same profile for both Catalina and bigSur broke for Cata.
We don't have M1 chips yet so I can't test, but yes, I suggest to split profiles by macOS version
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-15-2021 05:04 AM
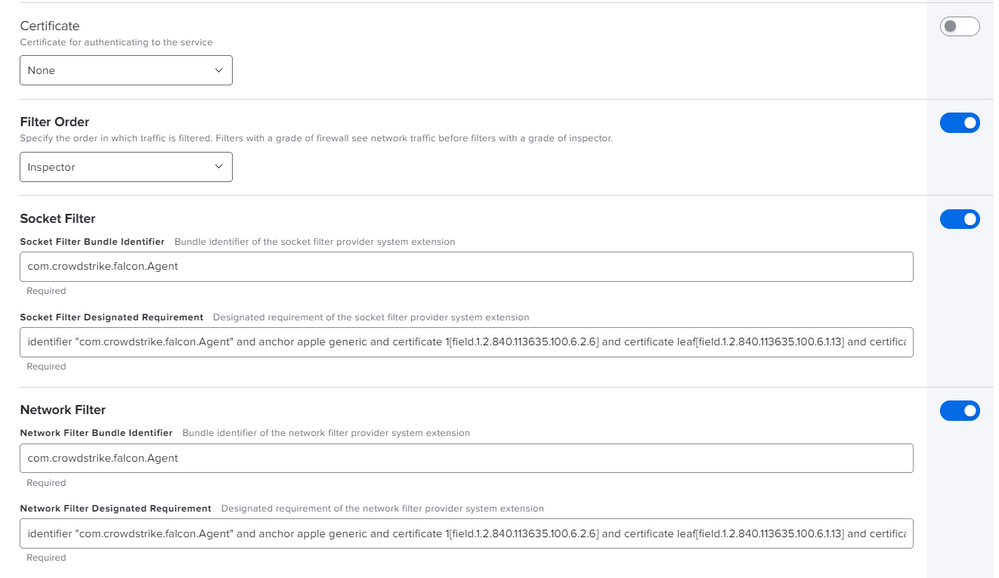
I believe you need to further modify the provided .mobileconfig.
The last two sections don't have the bundle id string defined and instead show "StaticCode" and you need to add X9E956P446 so they look like this:
<string>bundleID</string>
<key>X9E956P446</key>Worked on Catalina as of this week.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-20-2021 04:05 PM
@philburk I have all my kexts, SysExts and other profiles all split apart for better scoping.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-20-2021 04:08 PM
@franton Thanks, I figured as much. It makes sense, especially if SysExts/kexts are no longer needed. This would avoid the potential for removing the all of the payloads when only one needs removing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-17-2021 02:35 PM
How are you guys suppressing Falcon Notifications prompt? I see no one talked about this on any other threads.
You guys are getting a prompt to approve or deny Notifications for Falcon?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-16-2021 04:20 AM
@danny.gutman You can use the BundleID com.crowdstrike.falcon.UserAgent to configure notification. It is the BundleID of the Falcon Notification.app located in the Falcon.app /Applications/Falcon.app/Contents/Library/LaunchServices/Falcon Notifications.app
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-21-2021 11:50 AM
Here's my problem - I have two different profiles, one for Catalina, one for Big Sur. The Catalina profile has KEXT, and the Big Sur does not. Everything is fine and working smooth, except when I upgrade from Catalina to Big Sur. Then, at log in, I get the prompt that system extensions were blocked from launching. Anyone tested the upgrade and figured this out?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2021 06:07 AM
How are you guys taking the XML provided by CS and importing it to Jamf Pro?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2021 07:26 AM
@Jason33 it's recommended to deploy the system extension profile to Catalina and above to avoid this. The profile should exist before the system extensions are activated and this was the best way we accomplished this for clients upgrading from Catalina to Big Sur.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-24-2021 04:41 AM
@jtrant doh! You're right! Thanks for the guidance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-22-2021 10:02 AM
I think I found a solution for the "System Extension Updated" pop-up. The configuration profile with all your (good) settings for Crowdstrike needs to be run again. This is very simple solution, but implementing it is the tricky part...
This is how I've done it, looks ugly and it's not that clean, if someone finds another better way to run a configuration profile after policy to install Crowdstrike is run, please share it.
1. Create/modify your post install script for Crowdstrike .pkg installer to include: (this has to be after you run falconctl license ID and falcontctl load)
if [ $? -eq 0 ]
then
mkdir -p /Library/Application\ Support/JAMF/sample_folder
touch /Library/Application\ Support/JAMF/sample_folder/crowdstrike
/usr/local/bin/jamf recon
fi2. Create an Extension Attribute (in Settings) that checks if file exists and use this script:
#!/bin/sh
if [ -e /Library/Application\ Support/JAMF/sample_folder/crowdstrike ]
then
echo "<result>True</result>"
else
echo "<result>False</result>"
fi3. Create a smart group that checks if the file exists using that new Extension Attribute you created and setting the value to true.
4. Duplicate your good Configuration Profile for Crowdstrike and scope it to this new Smart Group.
I'm still testing it but looks like is doing the job...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2022 08:29 AM - edited 01-30-2022 08:31 AM
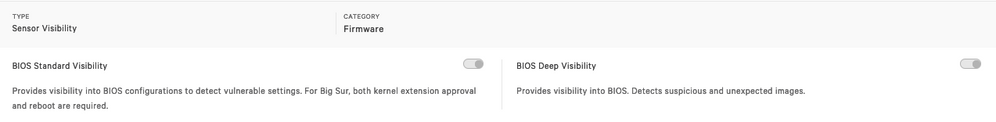
I have an answer for those like me who got here with a Google search. If you have the "System Extension Updated/Blocked" window (first it's a lie, it's a legacy kernel extension), it's because the BIOS Standard Visiblity is enabled on a Falcon policy. This will not only show up at the sensor installation (on Big Sur and above), but at every sensor update going forward. Note that whatever the end user does, Falcon is still running and working. It just won’t gather firmware data until the kext is approved and the computer rebooted.
The popup won't show up on M1 computers because this firmware analysis feature doesn't seem to exist.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-07-2022 01:33 PM
Thanks Jeremyb, this is definitely the answer I was looking for...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-01-2022 01:43 AM
FYI - We are running Crowdstrike at my organisation and we've just been informed that the BIOS visibility settings for any Mac running at T2 chip should be disabled
See extract from Crowdstrike email:
BIOS Visibility is not supported on M-series Apple Silicon (M1)-based Macs.
BIOS Integrity Check is not supported on Macs with T2 chips - which at this point is the vast majority of Mac hardware.
Given the limited percentage of Mac hardware that can take advantage of BIOS Visibility, we no longer recommend to customers that this feature be enabled on Macs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-01-2022 08:10 AM
The BIOS stuff requires a KEXT to work period, no matter the device type or OS. That's the reason it should be disabled as the functionality isn't exposed via system extensions.
The CS guys on mac admins slack highly recommend disabling it, and we've had zero issues since doing that at my org.