- Jamf Nation Community
- Products
- Jamf Pro
- Re: Firefox and company certs (again)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Firefox and company certs (again)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-10-2016 04:40 AM
I have completely given up on trying to use CCK2 to configure Firefox. The directions are vague and the author admits that it doesn't work with the Mac version any more. The major problem is that we have company CAs that are already imported into the System Keychain but Firefox is deliberately built to NOT read that System Keychain (there are many threads about this on mozilla forums and bug reports). Manually importing all the certs is NOT an option. I needed to automate this. I did a lot of research and found that if I import any certs or CA certs into Firefox on my Mac and then copy the cert8.db file to a user on another machine, that will work. The problem is trying to push the file to the target location because of the random folder name of the Firefox profiles across computers. I ended up putting a copy of the cert8.db file (with 777 permissions via Composer) into /Users/Shared/ and then wrote a script to copy it to the current user's firefox profile folder. The hard part was working out how to fit a wildcard into the command. Here's the script I use:
#!/bin/sh
# this script relies on a copy of cert8.db that has the full company cert supply in it to
# be placed in /Users/Shared/ then it copies to the logged in user's firefox profile.
#variable for storing the current users name
currentuser=`stat -f "%Su" /dev/console`
# must quit Firefox before replacing the file or else the data inside the file will be overwritten.
pkill firefox
# it doesn't do any good to try and copy a file to a location that doesn't exist and relies on random naming.
# I had to specify /bin/cp because apparently Apple aliases cp to "cp -i" and that changes the way it works?
if [ -e /Users/$currentuser/Library/Application Support/Firefox/Profiles/ ]
then
/bin/cp -fv /Users/Shared/cert8.db /Users/$currentuser/Library/Application Support/Firefox/Profiles/*/
fi
# deletes the source file when done.
rm /Users/Shared/cert8.dbSo far the script works from Self Service, but I have seen if a user has multiple folders within their Profiles folder, it only copies to 1 of them and not the other. I'm just glad Safari and Chrome know to use the certs from the Keychain.
- Labels:
-
Scripts
-
Software Distribution
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-10-2016 06:19 AM
@AVmcclint - Where did you read that CCK2 no longer works on the Mac? I'm still using it (with ESR) as of 45.2.0esr... haven't tested against 45.3.0 yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-10-2016 06:21 AM
https://mike.kaply.com/2015/01/13/cck2-what-now/
And the instructions are very vague anyway.
With AutoConfig, things are quite simple (at least on Windows and Linux). The output of the CCK2 Wizard is a zip file that can be unzipped in the same directory where the Firefox executable is located. It puts all the necessary files in the right places and you can immediately start Firefox and see your customizations. Things are not so good on Mac starting with Firefox 34. AutoConfig is broke right now due to the new Apple signing requirements. We’re investigating the best way to fix that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-10-2016 06:37 AM
Ahhhh... ok, that. I think that's rather old info.
Greg Neagle has an AutoPkg recipe that generates a pkg installer that installs Firefox with your autoconfig.zip. Works great. Just create an override, put the autoconfig.zip in the same directory as the override, and run.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-10-2016 06:38 AM
While less than user friendly, cck2 does work and is the basis of our package including carts developed in July of this year.
If it helps, I can answer questions about what we did.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-10-2016 06:46 AM
My biggest problem with it is that once I have the AutoConfig zip/folder, I have not been able to figure out WHERE the components are supposed to go. The directions say to put it in the same folder as the Firefox executable. One way to interpret that is to just put it in /Applications (doesn't work). Another way to interpret it is to put it into /Applications/Firefox.app/Contents/MacOS/ (doesn't work there either) But even then, is it the AutoConfig folder that needs to go somewhere or is it the subfolders that need to go there. I've put everything everywhere and it absolutely does not work under any conditions at all. I've tried making the CCK2 config to contain a few specific settings like home page and certs and disable updates, and I've made it to only contain certs. Nothing works. I think the first clue I need is EXACTLY where do you put the AutoConfig stuff.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-10-2016 07:08 AM
We should start a support group for this disaster!
We recently received a series of Certificate Authority, proxy server certs and Firefox prefs that our in-house security team mandated be a part of Firefox. There was one new CA cert, a handful of prefs and twelve certs, the latter needing to go under Servers in Firefox certificates view.
We DO NOT have the ability to add these prefs/certs for new users - Users that have not yet run Firefox so that the initial FF user profile is generated. We're working on a means of doing this.
<Shaking fists at sky>
Many moons ago, you could take a pref.js/firefox.cfg and cert8.db file from a working, test Firefox instance - inject these into /Applications/Firefox.app/Contents/Resources, and both new and existing users were good to go.
Mozilla, in their infinite wisdom and apparent sadism towards enterprise admins, did away with so many of these sanity-driven features around FF 45 or so. Not only did the centralized profile defaults structure go away, but the injection of Servers certificates has been deprecated.
I used CCK2 to create a small framework of desired prefs and adding the Certificate Authority piece. Other than that, CCK2 is just disastrous to any kind of enterprise-related use with Firefox.
</Fists>
Our JSS Firefox policy consists of two packages and one script.
Package 1: A DMG with the Firefox app directly from Mozilla. We quick start the app, run it so initial settings, etc. are in place and them use Composer to build the DMG
Package 2: A DMG containing Firefox prefs, Mozilla's NSS tools (compiled from their source code) and certificates
The script is run after the package have been deployed. Here are highlights of the script:
#!/bin/sh
#Pull a list of bona fide users present on the machine. Excludes admin and daemon/service accounts
#User names outputted to a temp file
dscl . -list /Users UniqueID | grep -v Old | awk '$2 >= 500 { print $1; }' > /Library/Application Support/JAMF/userlist.txt
##
#Firefox Certificate Update Routine
#The code below traverses the user's 'Application Support' directory
#Where a Firefox profile is located, the script extracts the unique profile foldername
#Certificates are updated using an in-house compile of Mozilla's open source NSS/NSPR toolset
#The toolset is deleted from the machine once updates are complete
#
#1. Add the new CA root certificate
#2. Add certificates for new, local Intranet proxy hosts
##
while read i
do
# The loop will be processed for all user FF profiles found
# stderr omitted from results to keep the results clean
searchResult="$(find /Users/$i/Library/Application Support/Firefox -type f -name cert8.db 2> /dev/null)"
if [ -e "$searchResult" ]
then
# Capture user name where FF profile path found
# Capture name of Mozilla's randomly-generated profile directory
# Both values are ECHOed to stdout so that the info will be included in the policy's installation logs
# For quicker troubleshooting
UserName="$(echo $i)"
ProfilePath="$(echo $searchResult | awk -F "/" '{print $8}')"
echo "User Name: $i"
echo "Profile Path: $ProfilePath"
# We had a couple of older, expired CA certs that needed to be deleted before the new one gets added
# Even if multiple certs have the exact same CN or other attributes, Mozilla tools still make you delete them in serial fashion
/opt/local/bin/nss-certutil -D -n "CN=*OMITTED*" -d /Users/$i/Library/Application Support/Firefox/Profiles/$ProfilePath/
/opt/local/bin/nss-certutil -D -n "CN=*OMITTED*" -d /Users/$i/Library/Application Support/Firefox/Profiles/$ProfilePath/
/opt/local/bin/nss-certutil -A -n "CN=*OMITTED*" -t "CT,C,C" -d /Users/$i/Library/Application Support/Firefox/Profiles/$ProfilePath/ -i /Library/Application Support/JAMF/certs/client/CAcert1.cer
/opt/local/bin/nss-certutil -A -n "*OMITTED*" -t "P,P,P" -d /Users/$i/Library/Application Support/Firefox/Profiles/$ProfilePath/ -i /Library/Application Support/JAMF/certs/client/ServerCert2.cer
/opt/local/bin/nss-certutil -A -n "*OMITTED*" -t "P,P,P" -d /Users/$i/Library/Application Support/Firefox/Profiles/$ProfilePath/ -i /Library/Application Support/JAMF/certs/client/ServerCert3.cer
cp -r /Library/Application Support/JAMF/JamfCustomapps/prefs/* /Applications/Firefox.app/Contents/Resources/
# Run a quick check of installed certs in the user's Firefox profile path. Query run against cert8.db
# Values ECHOed to stdout for inclusion in the policy's installation logs
certCheck="$(/opt/local/bin/nss-certutil -L -d /Users/$i/Library/Application Support/Firefox/Profiles/$ProfilePath)"
prefsCheck="$(cat /Users/$i/Library/Application Support/Firefox/Profiles/$ProfilePath/prefs.js | grep ntlm)"
echo $certCheck
echo $prefsCheck
fi
done < /Library/Application Support/JAMF/userlist.txt
#Clean up temp stores for certificates and NSS toolset
rm -fr /Library/Application Support/JAMF/JamfCustomApps/prefs
rm -fr /Library/Application Support/JAMF/JamfCustomApps/certsHere are some example values related to the script:
bash-3.2# pwd
/Users
bash-3.2# find . -type f -name cert8.db 2> /dev/null
./administrator/Library/Application Support/Firefox/Profiles/i8kfah8z.default/cert8.db
./mharper/Library/Application Support/Firefox/Profiles/9k5orbbs.default/cert8.db
bash-3.2# /opt/local/bin/nss-certutil -L -d /Users/mharper/Library/Application Support/Firefox/Profiles/9k5orbbs.default/
Certificate Nickname Trust Attributes
SSL,S/MIME,JAR/XPI
Google Internet Authority G2 ,,
<OMITTED>-Auth P,P,P
CN=<OMITTED> CT,C,C
DigiCert SHA2 Extended Validation Server CA ,,
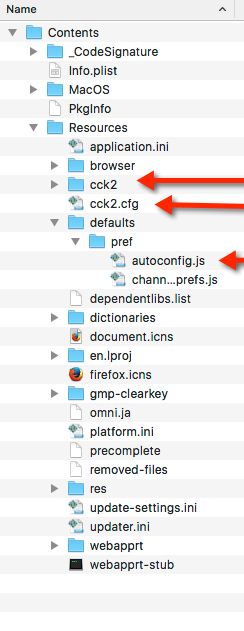
DigiCert SHA2 Secure Server CA ,,Below is a screenshot of the folders/files taken from our customized FF instance and injected into the target machine's installed instance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-10-2016 07:13 AM
Regarding CCK2, I'd like to add that it is an INCREDIBLE tool. We use it to create the initial config items that we need. It seems that the guiltier party in this mess would be Mozilla and their changes to FF structure over time.
The creator of CCK2 (Mike Kaply) is very active in the Mozilla dev community and has stuck it to them something fierce for their changes to the defaults functionality
@gregneagle - Your AutoPKG recipe is incredibly, incredibly awesome :)
I just want to give full credit and respect to the authors of these tools.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-10-2016 07:54 AM
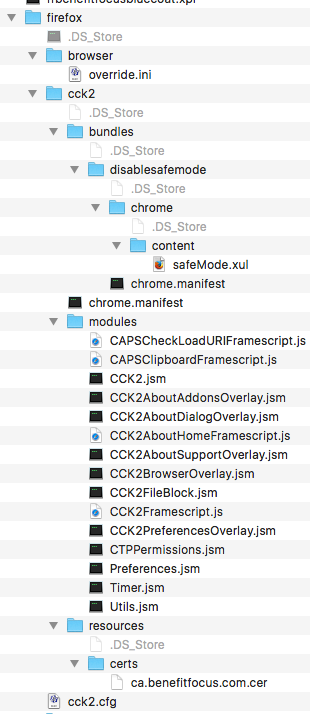
FWIW I have no issues with CCK and ESR 45.2.0. The instructions are vague for macOS but putting the output in the following locations works. I have noted in testing this I needed to open Firefox.app once before injecting the cck2 output, code signing was pitching a fit otherwise. Was able to drop this into a pkg and install it on another machine successfully.
I have switched to the autopkgr method which has been working well but I wanted to make sure I could still get this method working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-10-2016 09:14 AM
@Kaltsas - That looks good! I need to try that again when I get a moment.
We are effectively vetting these Infosec-mandated requests with each new release of Firefox. So far, it's been successful.
HOWEVER,
There is no longer any means of adding Server certificates unless you script it using the NSS certutil command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-11-2018 12:28 PM
Could you let me know where the following information is found on how to do this? I already use AutoPkg:
Greg Neagle has an AutoPkg recipe that generates a pkg installer that installs Firefox with your autoconfig.zip. Works great. Just create an override, put the autoconfig.zip in the same directory as the override, and run.If it's using CCK2, I'm still trying to find how to run that and make it work for the Certificate part of Firefox.
Thank you in advance.
Found my answer, thank you to everyone.