- Jamf Nation Community
- Products
- Jamf Pro
- Re: Jamf Connect Login "Unable to load Identity Pr...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Jamf Connect Login "Unable to load Identity Provider"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-01-2019 11:46 AM
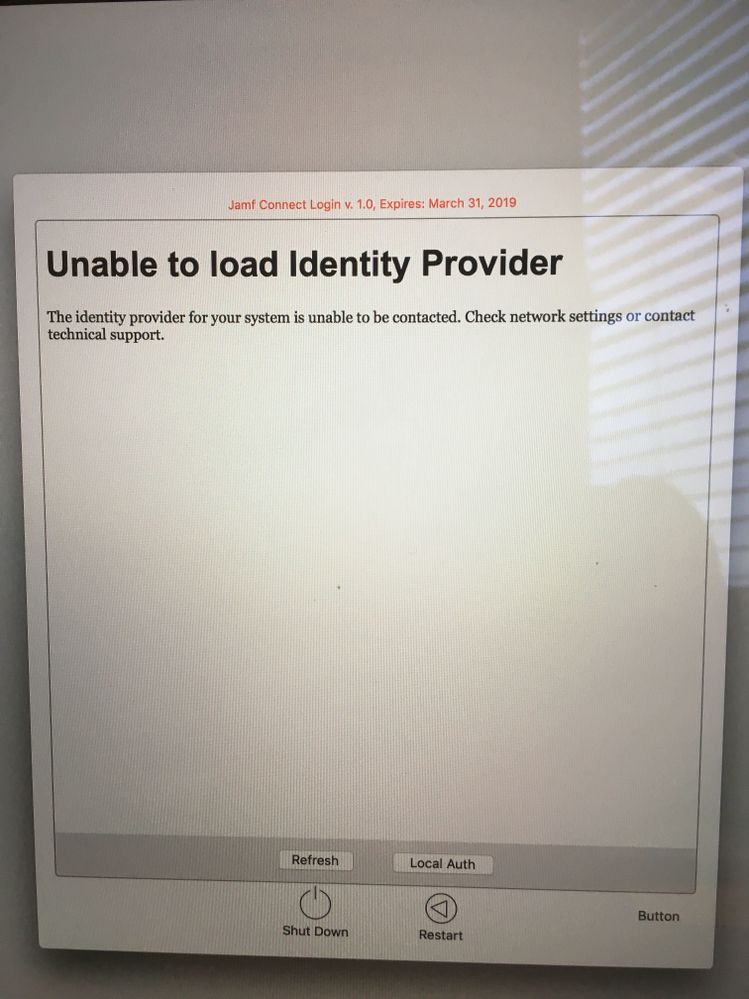
I have deployed the 2 plist files to the machine and updated the "Auth Server" setting to our Azure url. Deployed Jamf Connect license mobilconfig to the device and installed the Jamf Connect Login software. The login screen says "Unable to load identity Provider" This is for Azure, What am I forgetting to do?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-08-2019 07:04 AM
I'm having the same issue but with Okta.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-12-2019 07:14 AM
We are using Jamf connect login . We plan to use it for okta. We are facing the same issue even if we set okta authserver preference with our okta instance, and we also created an application in okta for jamf connect, but the issue still exists. Does anyone know how to fix this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2019 05:31 AM
I've reset the authorizationdb using /usr/local/bin/authchanger -reset -Okta, after that the login window changed to this:
But now the log states:
2019-02-15 14:13:50.379036+0100 0x21e8 Error 0x0 712 0 SecurityAgent: (JamfConnectLogin) [com.jamf.connect:CheckOktaMech] Unable to get Okta Server
I think it has to do with adding a native custom application to Okta, but can't find out the URI's for authorization. Maybe this helps with AzureAD as well..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2019 08:10 AM
I'm in exact the same spot as @nickvanjaarsveld. I am not seeing anything else in the documentation that would point me in the right direction to move forward.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-19-2019 12:27 PM
I ran into this issue as well, but with Okta. I was trying to figure it out on my own for a couple of weeks. I finally reached out to Jamf support and had them look over the plists I created for both NoMAD Pro and Jamf Connect Login. It took them a few days as well, but they did end up getting me a resolution today. It seems that there was a key missing (that I didn't come across in any of the documentation) that identifies the Okta as the IdP. The key is below and needs to be added to the com.jamf.connect.login.plist you create for Jamf Connect Login.
<key>OIDCProvider</key>
<string>Okta</string>
I had to refresh the login window a few times after the new config profile was push out but it ended up connecting to Okta. The support tech also advised to put "authchanger -reset -Okta" in the Execute Command section (Files and Processes payload) of the app policy. I would presume that the same could be achieved for Azure if you substitute the "Okta" values with "OIDC". Hope this helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-19-2019 03:42 PM
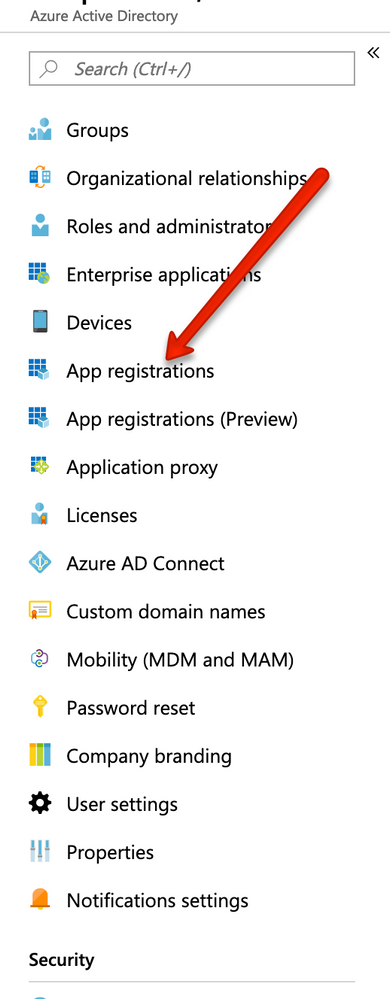
Have you logged into portal.azure.com and added to app registrations?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2019 05:05 AM
Found this blog as well, which helped me to at least authenticate through Okta. However, while authenticating is working properly now, I'm getting an error that states:
"Unable to create account. Error: One of the parameters provided was invalid."
Blog URL: https://travellingtechguy.eu/how-to-use-nomad-login-okta-with-jamf-pro/#Tutorial
Maybe this helps @andre.sanchez
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2019 08:19 AM
If you're using Azure AD, I'm going through this right now and you don't need to use the two PLIST files that talk about AuthServer. You just need to use the on named com.jamf.connect.login.plist and com.jamf.connect.verify.plist
You'll need to have created the Azure App Registration outlined here:
https://docs.jamf.com/jamf-connect/1.0.0/login/administrator-guide/Integrating_Jamf_Connect_Login_with_Azure.html
You'll use the values from the Azure App registration in those PLIST to set the OIDCClientID and OIDCROPGID
This guide is useful as well:
https://travellingtechguy.eu/jamf-connect-login-with-azure/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-11-2019 02:42 PM
I found a potential problem that can generate this symptom. Wifi typically does not connect until after you log in and so the Azure login page cannot display until after the user has logged in. I'm unsure if this applies pre-Mojave. It looks like there are some CLI-based ways to resolve this problem however the solution for me was to deploy a wifi profile via my MDM(Intune) which causes wifi to connect pre-login, although it does require the user to refresh once after boot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-11-2019 02:42 PM
I found this was caused because wifi was not connecting. I deployed the wireless connection via MDM policy and now I can load it without any issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-13-2019 03:49 PM
I get this every time on first boot. Occurs even when connected via ethernet with WiFi disabled. I hit the Refresh button and it loads straight away.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-18-2019 10:55 PM
@jamesandre try authchanger -reset -Okta
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-19-2019 12:36 PM
@Kumarasinghe Running this after deploying the pkg and config profiles worked for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-20-2019 09:28 AM
If this was caused by lack of wifi, and you had do deploy a wireless policy with MDM, wouldn't that mean that you could only use this on known access points that you had built an MDM policy for?
It seems to me that you'd always need to be connected to the internet, at least, for first connection when the account is set up. Am I missing something about how this is supposed to work?
I don't see how you could build and MDM wireless profile and predict various scenarios where the user would be trying to set this up.
I too am getting the error "Unable to load Identity Provider". I have the app registered in Azure and have built the plist. Did everyone here have to sign the plist? I didn't do that and am wondering if that's my whole problem. I'm waiting for a cert from apple. Is the "Developer ID Installer" cert what I would use to sign a plist?
thanks