- Jamf Nation Community
- Products
- Jamf Pro
- Re: Jamf Pro 10.30.1 Security Upgrade
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Jamf Pro 10.30.1 Security Upgrade
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 08:40 AM
Hi Jamf Nation,
On June 15, 2021, we were made aware of a URL redirect vulnerability, affecting Jamf Pro customers who host their environments on-premises and less than 1% of Jamf Cloud customer environments. We have not discovered any evidence of malicious use of the vulnerability.
CVE-2021-35037 has been reserved. Additional technical details will be included in the CVE once our on premises customers have had a reasonable interval to patch.
The vulnerability allows for arbitrary URL redirection using a very specifically-formatted Jamf Pro URL. This is assessed to be a CVSS 6-7 (medium - high) severity issue affecting Jamf Pro versions: 10.30 and earlier
We have pushed out a configuration change to all affected Jamf Cloud customers to address the vulnerability. No further action is required from these customers. For Jamf Pro customers who host their environments on-premises, Jamf Pro 10.30.1 has been made available and a notification has been sent to these customers. We strongly recommend they upgrade their environment to Jamf Pro 10.30.1 as soon as possible. No other customers are affected by this vulnerability. If you have any questions, please reach out to Customer Success for more assistance or post a comment here. We will update this post with information as it becomes available.
How is the vulnerability exploited?
An attacker may craft a URL that appears to be for a customer's Jamf Pro instance, but when clicked will forward a user to an arbitrary URL that may be malicious. This is commonly used as part of a phishing campaign.
What is the potential impact of the vulnerability?
Your users may trust a URL due to the Jamf Pro context and provide an attacker with information, access or even install malware.
If your Jamf Pro instance uses https to communicate, note that any malicious URL being redirected to that does not have a valid certificate would result in warnings from common browsers to any users that may click an exploited URL.
Is it remotely exploitable?
An attacker can craft an exploited URL without any connection to your devices or services. They only need to have the URL to your Jamf Pro instance. Victims are exploitable if they can reach a Jamf Pro server and are presented with this malicious URL.
Does a device have to be enrolled in Jamf to be vulnerable?
Since the attacker only leverages a Jamf Pro instance as an intermediary to trick a user into visiting a malicious URL, the user and device do not have to be enrolled or associated with Jamf in any way. As long as the user has access to the Jamf Pro instance and clicks the exploited URL, they are vulnerable.
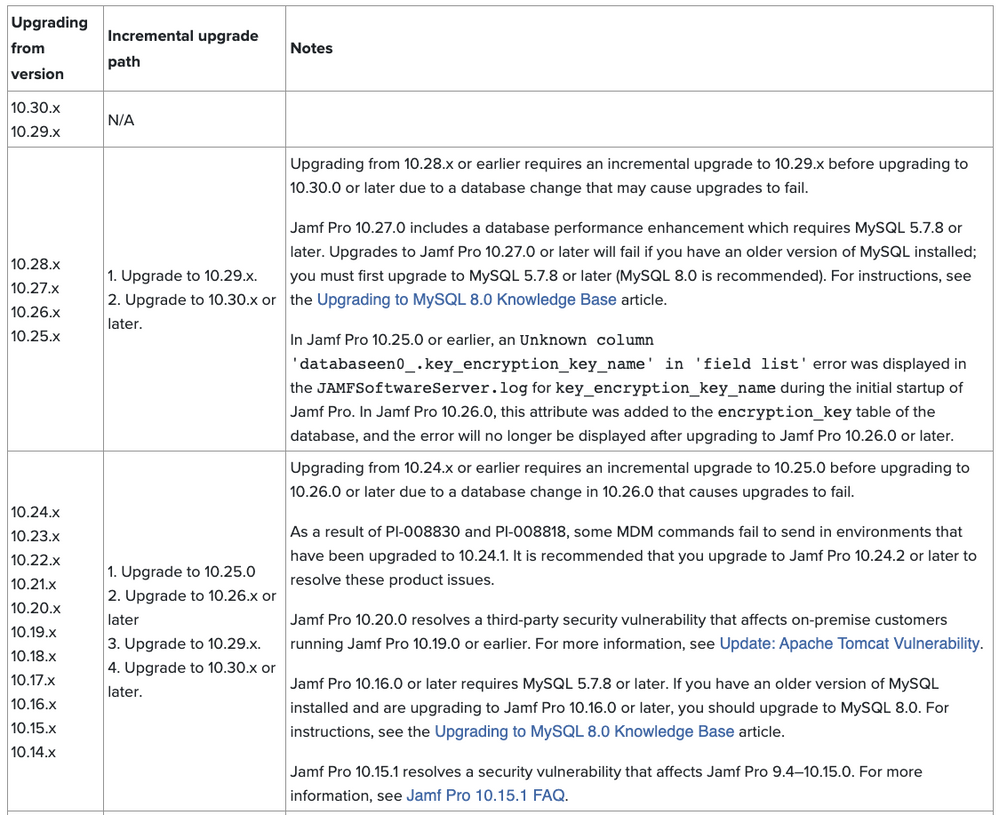
Important Notice: Upgrading from 10.28.x or earlier requires an incremental upgrade to 10.29.x before upgrading to 10.30.0 or later. Please reference this document on incremental-upgrade-scenarios for more details
We apologize that some customers experienced an issue accessing Jamf Account subpages. As of 9 am CST, June 21, this issue has been resolved and everyone should have access to all Jamf Account pages.
Aaron Kiemele
Chief Information Security Officer, Jamf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 08:56 AM
Are versions prior to 10.30.0 (eg: 10.29.1) susceptible to the exploit?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 08:57 AM
Is this affecting older versions of Jamf Pro On-Prem or strictly 10.30?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 09:12 AM
+1 please add affected versions of Jamf Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 09:17 AM
We really need to know if previous versions are affected. We haven't upgraded to 10.30.0 yet so it's important for me to know if our current version is vulnerable so I can prioritize the update.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 09:26 AM
Best thing is to put in an urgent support ticket. I just did. If they get enough of them, hopefully they'll update this post to let everyone know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 09:31 AM
[Update] - Updated above to include the following: Affected Jamf Pro versions: 10.30 and earlier
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 09:32 AM
Looks like description has been updated. "affecting Jamf Pro versions: 10.30 and earlier"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 10:34 AM
@Aaron.Kiemele Please advise the severity of this vulnerability for Internet-facing nodes which are running in Limited Access. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 10:51 AM
Just a heads up to any on-prem who need to upgrade, it appears there is an incremental dependency for going from 10.28 and lower, so anyone not yet on 10.29 be aware.
https://www.jamf.com/jamf-nation/articles/647/incremental-upgrade-scenarios-for-jamf-pro-10-0-0-or-later
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 10:54 AM
So Should I upgrade to Jamf Pro 10.29.2 and then to 10.30.1 from 10.28?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 10:57 AM
Thats what the document says, and my own failed upgrade in test would confirm that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 10:59 AM
Deleted
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 11:21 AM
Any difference in upgrading to 10.25 or 10.26 before going to 10.29 the 10.30.x ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 11:42 AM
- If you're on 10.14-10.24, you must Upgrade to 10.25 before going to 10.26 due to a DB change.
- Before going to 10.27, you must first upgrade to MySQL 5.7.8 or later (MySQL 8.0 is recommended).
- Upgrading from 10.28.x or earlier requires an incremental upgrade to 10.29.x before upgrading to 10.30.0 or later due to a database change that may cause upgrades to fail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 12:24 PM
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 01:07 PM
@dan-snelson, The severity of this issue doesn't change for instances in Limited Access mode as this is a URL redirect and the goal is to bring you to some other URL other than your Jamf Pro server. Your Limited Access endpoint configuration of not allowing login to Jamf Pro would still be in place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 01:09 PM
Thanks, Obi-@mike.paul!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 01:20 PM
Update - Updated above to include information on incremental upgrade scenarios for jamf pro 10.0.0 or later
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 01:40 PM
Hi, We are able to upgrade our server from 10.26 - 10.29.2 - 10.30.1 . Upgrade was smooth . No issues during upgrade .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2021 04:54 PM
That's one way to get all of your user base to finally get around to upgrading their on-prem servers :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-19-2021 02:03 AM
Hop it's just me, but I see no assets in my account...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-19-2021 05:37 AM
Jamf - not all of your users got an email about this. I put a ticket in on friday and pay for premium support and no response. not a great look.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-19-2021 09:04 AM
Heads up for those of you who have to do incremental upgrade from before 10.29. You'll likely hit this if you use Computer Security and Privacy payload in your config profiles.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-20-2021 06:03 AM
The Assets page (in fact the whole account.Jamf.com) is delivering a blank page (since three days!)! So no Download ist possible … It seems like a couple of things are going wrong at Jamf. Which is isn’t really trustworthy for a IT security company …
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-20-2021 09:25 AM
I’m just here to say thank you for the correct use of “premises.”
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2021 01:02 AM
I'm trying to access the account.jamf.com URL, and have a blank page since yesterday.
Can you ?
Can't open ticket, too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2021 01:10 AM
deletet, because of double posted
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2021 01:13 AM
Same here, I can not access the "My Assets" page, it's just blank
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2021 01:15 AM
As many others, my "My Assets" page is blank, too. There ist no content and no update to version 10.30.1 available. I have tested with different browsers. No worry, it's only a security patch... no big thing at all....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2021 07:05 AM
Update - Added the reserved CVE number to the above post. - CVE-2021-35037
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-22-2021 04:20 AM
For all who have a blank page (We got this since about a week).
If you look at it it will show a cors error..
You can have a workaround with an extension like "Allow CORS: Access-Control-Allow-Origin" in Chrome.
It is really just a workaround till it is fixed..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-22-2021 11:33 AM
[Update] - document now reflects a resolution to an issue where some customers experienced an issue accessing Jamf Account subpages. As of 9 am CST, June 21, this issue has been resolved and everyone should have access to all Jamf Account pages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-23-2021 02:39 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-23-2021 04:00 AM
@Aaron.Kiemele Is jamf going to address that only some customers got emails about this critical update? This isn't the first time this has happened.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-23-2021 06:35 PM
@CasperSally Thank you for the feedback. It is our absolute intent to communicate quickly and responsibly to those we believe may be potentially impacted by security vulnerabilities. In some cases, we have used filters on direct email communication to avoid unnecessary action or concern by those who have not been impacted. It is evident that this may not have worked correctly. Our team is working to remediate this urgently to ensure it does not happen again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-24-2021 09:52 AM
We're still running 10.28 but making arrangements to update to 10.30.1.
It was my understanding that Jamf was going to start making use of the announcements in the Resource Center found in the lower right hand side of the browser window. If that's the case, why is there no mention of 10.30.1? I only see mention of 10.30.
For security issues, in my opinion, Jamf should be blasting such announcements out via every avenue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-25-2021 06:39 AM
@jhuls We got an email announcement on Friday 6/18/2021 but has been a real pain as they aren't sending regular email comms on releases anymore.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-25-2021 10:10 AM
[Update] - added clarification around potential exploitation and impact of URL redirection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
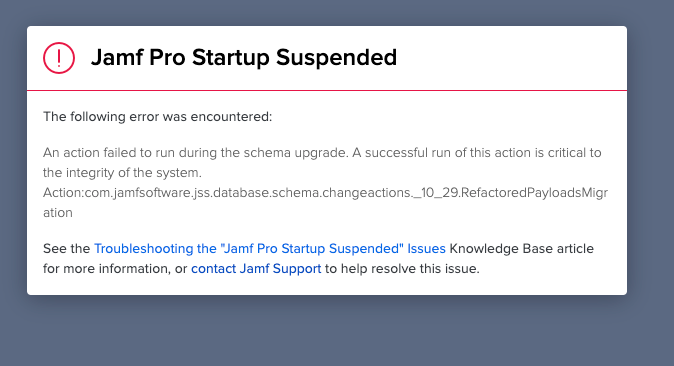
Posted on 06-28-2021 12:51 AM
So, I tried to U/G this weekend and had the following error upgrading from 10.28.0 to 10.29.0