- Jamf Nation Community
- Products
- Jamf Pro
- Re: Jamf pro cloud connection to on-prem Microsof...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2021 02:56 AM - edited 09-29-2021 03:07 AM
Hi friends,
I am new at Jamf and appreciate your help.
We use Jamf Pro in the cloud and we have a local Microsoft CA server.
My goal is to install certificates from the local CA using Jamf pro cloud on the mac devices.
I understand there are two ways to do this:
1. Using Jamf ADCS Connector
2. Using Jamf SCEP with local NDES server
Am I right?
What is the right and secure way to do it?
We also have Azure and Intune if that can help.
Thanks
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2024 08:05 AM
I'd be very interested in some more detail around this, diags/screenshots/gotchas/watchas etc if you have time to provide?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-29-2021 04:32 AM
AD-CS is the way forward, but if you have Azure we found it easier to create a Azure proxy connection to the server running the AD-CS connector and publish it out that way (that vey similar to how Intune provide its certificates from the premise CA using its own internal connector)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-29-2021 04:52 AM
That way there will be no need to open ports out?
Is there a guide on how to do this?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-29-2021 05:23 AM
There's still ports to setup for the proxy in Azure, but it meant I didn't have to deal with our network team at all and punch more holes in the firewall.
I don't have a guide for the Azure side, as my Azure SME did this part for me, but for the Jamf side I pieced information from both Travelling Tech Guy's blog
https://travellingtechguy.blog
and watching Laurent's JNUC presentation on AD-CS
https://www.youtube.com/watch?v=PbQOG5rJBcQ&t=1683s
Setup is really in two parts
1) getting the AD-CS connector installed and communicating with Jamf
2) setting ups PKI and certificate templates for the payloads to the clients
The best tip I can give for the latter what Laurent mentions in his presentation of don't use an existing certificate template being used for Windows but create a new one specifically for the Mac's
If I have listened to this first around it would of saved a whole lot of time troubleshooting
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2022 07:17 AM
I am seeing comments below indicating that this wouldnt work since the certs wont be passed through app proxy. How did you get around that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2021 06:28 AM - edited 09-29-2021 08:35 AM
Thank you @garybidwell .
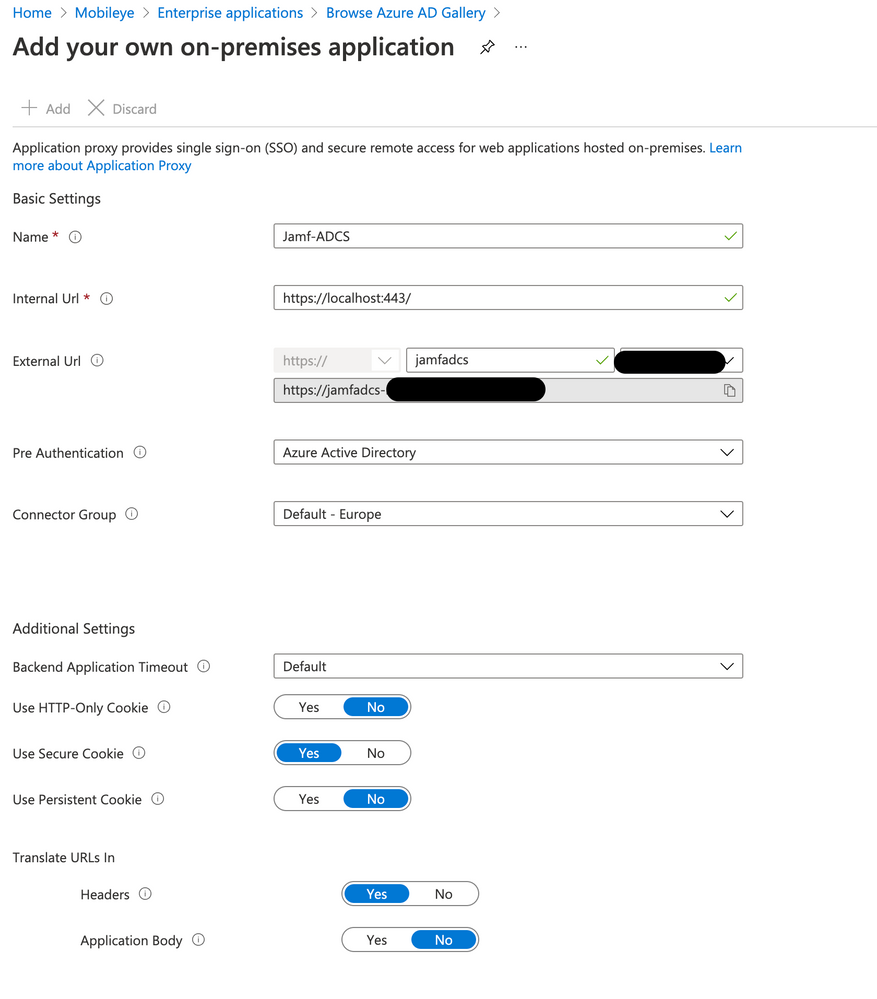
1. I installed the connector, and for -fqdn I used the full name of the server:
.\deploy.ps1 -fqdn jamfadcs.contoso.lan -jamfProDn contoso.jamfcloud.com -cleanInstall
2. I installed the Azure Proxy connector
3. I am in the process of creating the app in azure and not sure what data I should give in the internal Url (localhost or the name of the server?) and how to configure the other settings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-24-2022 08:58 AM
My understanding is this doesnt work
https://macnotes.wordpress.com/2020/11/10/can-jamf-adcs-connector-use-azure-web-app-proxy/
Azure Application Proxy decrypts and re-encrypts the traffic it proxies and the Azure/cloud version doesn’t have native support for the client-certificate based authentication used by Jamf ADCD Connector.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2022 07:18 AM
How did you ultimately solve this challenge?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2022 08:03 AM - edited 08-18-2022 08:21 AM
Ah yeah, this one took me a few days to figure out ...In our environment, the purpose of this was to do cert based 802.1x authentication.
At first my intention was to use the SCEP server already setup for our windows based devices enrolled through intune, struggled with it but failed to get it to work. This was (as I later found out) due to the intune connector, it takes over SCEP preventing you from using it for other purposes. So I spun up a new SCEP server specifically for Mac devices to retrieve a cert from our Windows PKI.
Once that was clear the general steps were this:
- Create an AzureAD app
- Install the the AAD App Proxy on the new SCEP server and link it back
- Create service account
- Create cert template in PKI
- Go into JAMF -> Settings -> PKI Cert -> Management Cert Template -> External CA -> Configure this as a SCEP proxy, pointing to the URL of your Azure AD App.
- Create a Configuration Profile with the SCEP, Cert and Network information.
LMK If you want screenshots or more detail, I know I glossed over a bunch of stuff.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2022 12:34 PM
Thank you. We are going with the dmz route on ADCS connector.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-24-2022 07:03 AM
I likely would have done the same if I had a DMZ setup. But since I didnt ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-24-2022 01:22 AM
can you help me with screenshot i struggling to do the same setup we have created a new Scep server for jamf and success we get the certificate the certificate is getting rejected by the radius server.
i have question is the ipsec offline is mandatory
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:10 PM
not working for me ( unable to get client certificate )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2024 08:05 AM
I'd be very interested in some more detail around this, diags/screenshots/gotchas/watchas etc if you have time to provide?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:09 PM
for me also client certificate unable to issue , it works well with the default certificate issued via proxy , how to fix this ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-18-2022 07:18 AM
Did you get this fully working? Did you do another work around?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-03-2021 03:53 PM
I have not yet been able to make it work and if anyone can help it would be greatly appreciated. Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-20-2021 06:49 AM
Just curious if you made any progress on this. I am starting down the same path.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-11-2022 10:53 AM
Any update, I am really curious too?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:15 PM
ADCS is working for us to get client certificate but via Azure Proxy unable to get client certificate but i m getting default offline certificate IPSEC. : any advise here pls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:23 PM
Register the certificate template in registry to issue the certificate to Jamf.
By default the registry entry is ipsec, later i found NDES template was not register to issue as default certificate once you update this Template your CA authority will issue the registered certificate template.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:33 PM
i have updated registry on below templates i have mentioned client certificate template created for JamfNDES
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MSCEP
EncryptionTemplate
GeneralPurposeTemplate
SignatureTemplate
after making these changes now Configuration profile in pending state earlier it was working with default
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:37 PM
You need to restart the server to apply the settings have you completed it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:38 PM
Also add the fingerprint haash key to your configuration profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:45 PM
yes server have restarted already
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:46 PM
yes fingerprint hash key seems to be same and it have not changed ( i have checked it already )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:54 PM
So do you use this sever dedicated to JAMF.
If you have intune or any other mdm using the same server to get certificate, definitely this will not work and in jamf you might see pending .
you might need dedicated server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:58 PM
For more understanding i might like to take look at all your setting , this need lot of understanding to set up its better let me know we can check this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 08:01 PM
yeah sure i am wishing too. let me know how to proceed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 07:59 PM
yes i am using fresh server setup and not shared with intune
and earlier with default certificate(IPSEC offline it worked well) when i hardcode registry with my certificate it is not issuing certificate and i dont know which log do i need to validate here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2022 08:03 PM
Email me bharath.r@mindtree.com with meeting url lets get connected and check this together
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-17-2024 11:22 AM
Did it Work finally ? @MannyKrishna or @bharathr1092750 I'm trying to implement the similar setup and kind of stuck. Any help would be greatly appreciated.