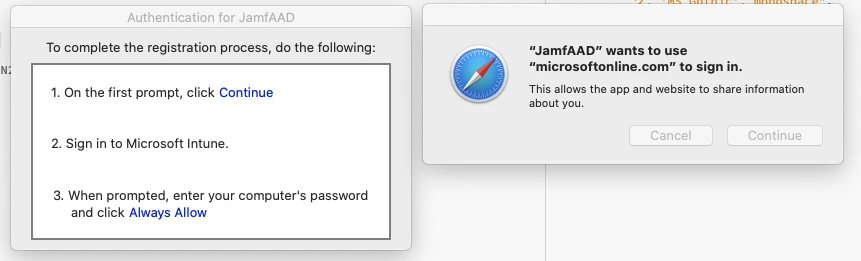
Getting this on some (but not all) of our Intune registered Macs that looks like it's coming from JamfAAD. Nothing triggers it that I can tell, totally random. We recently went through registering everyone in Intune and saw a similar message at the end of the procedure (when JamfAAD launches), but everything had been fine since then. The only thing that changed was we upgraded JSS to 10.25 last night and we changed the Intune connector this morning from Manual to Cloud Connector (which was pretty seamless). Anyone know what could be causing this?